A set of procedures performed by hardware, software, and administrators to monitor access, identify users requesting access, record access attempts, and grant or deny access. Compare with authorization. See also ACL.
A set of data that informs a computer's operating system which permissions, or access rights, that each user or group has to a specific system object, such as a directory or file. Each object has a unique security attribute that identifies which users have access to it, and the ACL is a list of each object and user access privileges such as read, write, or execute.
Acronym for Access Control Entry.
Acronym for Access Control List.
Access Control Lists can be applied to Group Policy objects that determine whether or not the policy will be applied on a system.
Microsoft's network directory service for computers.
Active Directory Application Mode, a Windows 2003 service in which LDAP runs as a user service rather than as a system service.
Active Directory Services Interface, an editor (browser), scripting language, and so on.
Active Directory Users and Computers (ADUC) is a Microsoft Management Console snap-in that you use to administer Active Directory (AD). You can manage objects (users, computers), Organizational Units (OU), and their attributes.
With respect to a directory, the organization of the accounts relies on properties they have in common. This similarity may be due to departmental structure or geographical location of the people that use the accounts.
ActiveRoles Server is a product installed on a Windows server that uses SQL Server for configuring data and publishing itself as a connection point object within Active Directory. It is a cross-platform, roles-based provisioning system that allows additional attributes to be stored for an object. For example, ARS can put a newly hired engineer into all the appropriate groups on all platforms relevant to their job description.
Authentication is the process of determining whether someone or something is, in fact, who or what it is declared to be. In private and public computer networks (including the Internet), authentication is commonly done through the use of logon passwords. Knowledge of the password is assumed to guarantee that the user is authentic. Each user registers initially (or is registered by someone else), using an assigned or self-declared password. On each subsequent use, the user must know and use the previously declared password. The weakness in this system for transactions that are significant (such as the exchange of money) is that passwords can often be stolen, accidentally revealed, or forgotten. Logically, authentication precedes authorization (although they may often seem to be combined).
In migrating identities from disparate NIS domains, identities from the first source repository are migrated without any changes to their internal identity (ID) and the first repository becomes the authoritative source. In case of ID conflict or mismatch, IDs in all remaining sources are changed to match those in the first source.
Authorization is the process of giving someone permission to do or have something. In multi-user computer systems, a system administrator defines for the system which users are allowed access to the system and what privileges of use (such as access to which file directories, hours of access, amount of allocated storage space, and so on). Assuming that someone has logged in to a computer operating system or application, the system or application may want to identify what resources the user can be given during this session. Thus, authorization is sometimes seen as both the preliminary setting up of permissions by a system administrator and the actual checking of the permission values that have been set up when a user is getting access. Logically, authorization is preceded by authentication.
When Block Inheritance is set on a GPO link, all GPOs above the link level are excluded from GPO processing unless the GPO is enforced.
Common Access Card, a smart card issued by the United States Department of Defense (DoD) for active-duty military, civilian employees and contractors.
One Identity font that contains standard icons used in the user interfaces for various One Identity products.
Essentially the distinguished name in reverse; generally, a software-internal representation, such as acme.com/engineering/jim.
Common Internet File System, a Microsoft technology. See also SMB.
Common Name, a component of a distinguished name (DN).
Component Object Model, a Microsoft technology that enables components to communicate, used by developers to create reusable software components, link components together to build applications, and take advantage of Windows services like Active Directory.
A proof of qualification or competence attached to a user or session, an object verified during an authentication transaction. In Kerberos parlance, a message containing the random key along with a service name and the user's long-term key.
Data Encryption Standard is a cypher selected as an official Federal Information Processing Standard (FIPS) for the United States in 1976. It is characterized by a relatively short key length (56 bits) and is considered less secure for many application environments than some alternatives.
Provisory authentication based on prior login and used in case of network failure. The maximum duration of a stored password hash is configurable.
In Active Directory, a centrally-managed group of computers.
The server that responds to security authentication requests in the Active Directory domain.
Flare default style that can be used to group content within a topic. It is a resource to structure and collapse content especially in non-print outputs.
Directory-specific entry in an LDAP environment.
If a GPO is enforced, then it will be applied regardless of block inheritance settings.
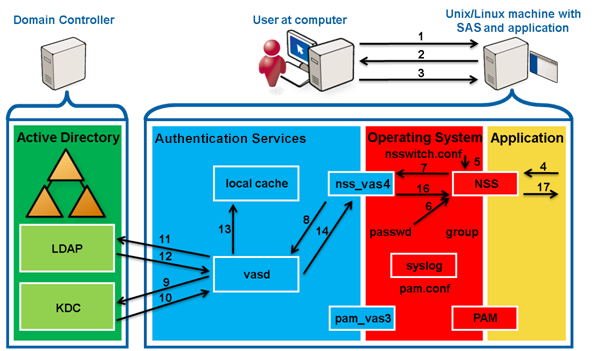
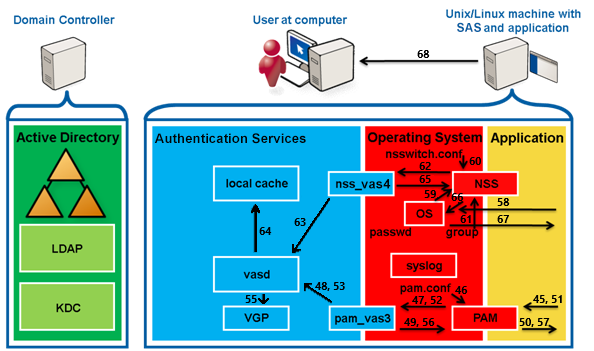
A piece of hardware, software, or both that sets rules about what network traffic can cross it. These rules can focus on the protocols used by the traffic and ports in use. Authentication Services, for instance, requires a set of ports by which it implements its services. Those ports must not be blocked. However, if a host has access to Active Directory, to its domain controllers, and so on, then the ports needed by Authentication Service are open. For Authentication Services specifically, this means 88 (TCP/UDP for Kerberos ticket services), 389 (LDAP queries and ping), 464 (TCP/UDP for Kerberos passwords), and 3268 (TCP for Global Catalog access); optionally, 53 (UDP for DNS SRV records) and 123 (UDP for time-synchronization with Active Directory). For Authentication Services Group Policy, port 445 (TCP for Microsoft DS).
The collection of all objects and their attributes and rules in Active Directory. It is named "forest" because it holds one or more trust-linked trees, allowing users in one domain to access resources in another domain.
Fully Qualified Domain Name; a domain name specified exhaustively, such as somehost.example.com.
Flexible Single Master Operations; a multi-master-enabled database such as Active Directory that provides the flexibility of allowing changes at any domain controller in the enterprise, but also gives rise to the possibility of conflicts and the need to resolve them, especially for certain tasks. Collectively, FSMO tasks are used where standard data transfer and update methods on multiple peer domain controllers are ill-adapted to multi-master replication, for example: schema update and modification domain naming (addition or removal of domains in the forest), relative ID assignment (including SIDs), infrastructure (security) maintenance (including GUIDs, SIDs, and reference object DN in cross-domain references), and <a href="#PDC">PDC</a> emulation. These tasks are handled in a single master model by Windows 2000/2003.
(also in lower case) A field in the Unix /etc/passwd file that contains general information about the user including things like full name, telephone number, and so on, depending completely on the host implementation.
group identity, standard C library object, represented by gid_t, identifying a group.
Group identity; broad term referring to the underlying number that identifies a group of users or other objects in a directory service.
List of short definitions of product-specific terms.
Group Policy Management Console; a Microsoft tool.
Group Policy Object; an actual directory object tied to system volume instance. The group policy object is a collection of settings that define what a system looks like and how it behaves for a defined group of users. A GPO is created, using the Group Policy Management Console when there are such settings. GPOs are associated with a container such as a site, domain, or organizational unit (OU). GPOs are very powerful and can be used to distribute software and updates such as Tivoli (IBM). See also group policy.
A Microsoft technology that reduces the cost of supporting Windows users by providing centralized management of computers and user in Active Directory. Group Policy controls various aspects of an object including security policy, software installation, login, folder redirection, and software settings. Such policies are stored on group policy objects (GPOs).
Generic Security Service; security services provided atop underlying, alternative cryptographic mechanisms such as Kerberos. According to RFC 2744, the GSS API allows a caller application to authenticate a principal identity associated with a peer application to delegate rights to another peer, and to apply security services such as confidentiality and integrity on a per-message basis.
Globally Unique Identifier; a number, address, or other cookie used to represent an object uniquely in a directory service, file system, and so on. In Active Directory, the GUID is a unique, unchanging 128-bit string used for search and replication.
Describes the action of a Unix or Linux workstation being incorporated into an Active Directory domain by means of the vastool join command.
The Key Distribution Center in Kerberos. Part of a cryptosystem to reduce the intrinsic risk of exchanging keys, basically consisting of the authentication server (AS) and the ticket-granting server (TGS).
A software application that requires or performs Kerberos authentication.
A computer network authentication protocol that proves the identity of intercommunicating points on an insecure network like a LAN or the Internet in a secure manner. Guards against eavesdropping and replay attacks.
An authentication system developed at the Massachusetts Institute of Technology (MIT). Kerberos is designed to enable two parties to exchange private information across an otherwise open network. It works by assigning a unique key, called a ticket, to each user that logs on to the network. The ticket is then embedded in messages to identify the sender of the message.
A file containing authentication credentials used, usually in place of a password, for authentication.
Loadable Authentication Module, IBM's precursor to PAM on the AIX (Unix) operating system. Authentication Services provides a LAM-based implementation on AIX. LAMs are configured in /usr/lib/security/methods.cfg.
LDAP Data Interchange Format. See also Lightweight Directory Access Protocol (LDAP).
Prefix associated with Authentication Services runtime libraries and interfaces.
A software protocol for enabling anyone to locate organizations, individuals, and other resources such as files and devices in a network, whether on the public Internet or on a corporate intranet. LDAP is a "lightweight" version of Directory Access Protocol (DAP), which is part of X.500, a standard for directory services in a network.
Mapped User allows Authentication Services to authenticate against Active Directory while taking identity and Unix attributes from local files. It is implemented by replacing the 'x' placeholder in /etc/passwd with the user principal name (UPN) (Linux and Unix only), or by creating a local-to-AD user map file and specifying the location of that file in /etc/opt/quest/vas/vas.conf (Linux, Unix, or Mac).
Microsoft Identity Integration Server; a server that manages the flow of data between all connected data sources and automates the process of updating identity information (for example, of employees, and so on) in the implementing environment.
Microsoft Management Console, for which Authentication Services has a snap-in used when browsing users or groups and getting their properties.
Network-Attached Storage; file-level data storage connected, often remote, but not appearing as a local volume/disk. This is in opposition to SAN.
Native Active Directory mode refers to a network being serviced completely by either Windows 2000 or Windows 2003 servers, but not both. If servers from both versions are present, the services offered can only be a common subset of the two. If all servers are running Windows 2003 Server, then all the features that this operating system offers over its predecessor are available. Not being in native mode has ramifications for various components, that is, local groups are not added to the PAC of the Kerberos ticket; group membership is not available.
Network Information Services; a Unix client-server directory service protocol, originally Sun Microsystems' "Yellow Pages." It provides centralized control over many types of network objects including users, groups, and network services like printers. NIS arose as a solution to each Unix host having its own /etc/passwd and groups files as the resident authority on users and groups when these notions needed to be extended over a network. NIS domains are flat (no hierarchy), use no authentication and the NIS map files are limited to 1024 bytes in size.
Circumstance that needs special attention.
Name service caching daemon; provides a cache for the most common name service request on Linux and Unix from the passwd, group, and hosts databases through standard C library interfaces including getpwnam, getpwuid, getgrnam, getgrgid, gehostbyname, and others. The configuration file is /etc/nscd.conf.
Name Service Switch; interface to nsswitch.conf that controls how look-ups are done for users (/etc/passwd), groups (/etc/grps), hosts (/etc/hosts), and so on. For example, getpwnam goes through NSS, which is extensible and configurable (just as is PAM), to reach variably passwd, vasd, NIS, or LDAP.
Network Time Protocol, as implemented by a server that keeps time on the network and is accessible to other nodes for the purpose of all keeping the same notion of time.
An Active Directory container object used within domains. An organizational unit is a logical container into which users, groups, computers, and other organizational units are placed. It can contain objects only from its parent domain. An organizational unit is the smallest scope to which a group policy object can be linked, or over which administrative authority can be delegated.
Organization Unit. See also Personality container.
If a GPO specifies a policy and another GPO further down in the GPO application chain is allowed to overwrite the previously specified policy, then the policy supports override.
Privileged Attribute Certificates, used by Kerberized applications for fine-grained access control to services, a feature of Microsoft's Kerberos implementation.
Pluggable Authentication Module; an architecture and shared libraries created by Sun Microsystems for the Solaris operating system that permits intervention into and specialization of the authentication process. PAMs are configured in /etc/pam.conf or in individual files off /etc/pam.d/.
Primary Domain Controller; an NT concept, emulated on Windows 2000/2003, that performs a number of crucial tasks in an enterprise including time synchronization, password replication, recording of password failures, account lock-out, and modification or creation of GPOs.
An Active Directory organization unit (OU) designated to contain user and group personalities. Unix clients specify a Unix personality container (vastool join -p) in order to join the domain in Unix Personality Management (UPM) mode.
Consists of a primary Personality container, along with any secondary Personality containers. Only the Personalities, Active Directory users, and Active Directory groups that reside within that Personality scope will be usable on the Unix system.
Public Key Infrastructure; a way to ensure secure transactions over the wire; an arrangement providing for third-party vetting of user identities typically placing any keys within a certificate. Not yet a standard; there are myriad implementations.
Portable Operating System Interface; the open operating interface standard accepted worldwide. It is produced by IEEE and recognized by ISO and ANSI.
In Kerberos, this is basically a simple account including name, password, and other information stored in the database and encrypted using a master key.
The process of providing customers or clients with accounts, the appropriate access to those accounts, all the rights associated with those accounts, and all of the resources necessary to manage the accounts. When used in reference to a client, provisioning can be thought of as a form of customer service.
(pronounced "arcfour") A stream cipher in such popular protocols as secure sockets layer (SSL). RC4 generates a pseudo random stream of bits XOR'd with the clear-text password, for example. RC4 is more secure than DES.
A Kerberos term that usually maps to an Active Directory domain, not because they are the same thing, but because for implementation, it is a natural alignment.
A free software implementation of Microsoft's networking protocol that runs on *nix systems and is capable of integrating with an Active Directory (Windows) domain as either a primary domain controller or as a domain member. See also SMB.
Storage Area Network; an architecture for attaching remote storage devices (disk arrays, tape libraries, optical jukeboxes, and so on) to servers in such a way that to the operating system these appear as locally attached. This is in opposition to NAS where it is clear that the storage is remote.
Reference to legislation enacted in response to recent and spectacular financial scandals, to protect shareholders and the general public from accounting errors and fraudulent practices. The act is administered by the Securities and Exchange Commission, which sets deadlines for compliance and publishes rules on requirements. SOX defines which records are to be stored and for how long. It also affects IT departments whose job it is to store electronic records.
Safeguard Authentication Services.
A domain controller that holds the schema operations master role in Active Directory. The schema master performs write operations to the directory schema and replicates updates to all other domain controllers in the forest. At any time, the schema master role can be assigned to only one domain controller in the forest.
The Secure Sockets Layer (SSL) is a commonly used protocol for managing the security of message transmission on the Internet. SSL uses a program layer located between the Internet's Hypertext Transfer Protocol (HTTP) and Transport Control Protocol (TCP) layers. SSL is included as part of both the Microsoft and Netscape browsers and most web server products. Developed by Netscape, SSL also gained the support of Microsoft and other Internet client/server developers, becoming the de facto standard until evolving into Transport Layer Security (TLS). The sockets part of the term refers to the sockets method of passing data back and forth between a client and a server program in a network or between program layers in the same computer. SSL uses the public/private key encryption system from RSA, which also includes the use of a digital certificate.
An entity that can be positively identified and verified by means of a technique known as authentication.
A GSSAPI mechanism that allows the secure negotiation of the mechanism to be used by two different GSSAPI implementations. In essence, SPNEGO defines a universal but separate mechanism, solely for the purpose of negotiating the use of other security mechanisms. SPNEGO itself does not define or provide authentication or data protection, although it can allow negotiators to determine if the negotiation has been subverted, once a mechanism is established.
An authentication process in a client/server relationship where the user, or client, can enter one name and password and have access to more than one application or access to a number of resources within an enterprise. Single sign-on removes the need for the user to enter further authentications when switching between applications.
Used to design the online output window.
Server Message Block; a protocol that exists primarily for trust relationships, the concept upon which NetBIOS is based and hence, used by DOS and Windows. The message format is used for sharing files, directories and devices. CIFS (Common Internet File System) is a synonym for SMB. See also Samba.
Flare file type that can be used to reuse content. The One Identity Safeguard Authentication Services contains various default snippets.
When files or settings are left on the system after group policy has been un-applied, the files and settings are said to be tattooed. Unless otherwise documented a policy should remove all associated settings and files when the policy is unlinked. A policy that supports non-tattooing will not leave any files or settings behind after it is un-applied.
Ticket-granting server, part of a key-distribution server (KDC).
Ticket-granting ticket, the initial ticket given by the Kerberos authentication server permitting the TGS to be contacted
A voucher that isn't easily forged and proves that the bearer has properly applied for authentication to a service. In Kerberos parlance, a message containing a random key, the same one that was passed in the credential, plus the user's name, the whole being encrypted using the service's long-term key. Tickets obviate the inconvenience of using a password in that they can be supplied to different services rather than performing separate authentication of the password with each service. See credential.
Additional, useful information.
User identity, broad term referring to the underlying number that identifies a user in a directory.
Vintela Authentication Services.
Configuration file on the path /etc/opt/quest/vas/vas.conf that is Authentication Services' equivalent (and more) to Kerberos' krb5.conf.
The name of the Autentication Service daemon.
Quest Group Policy, Unix group policy product.