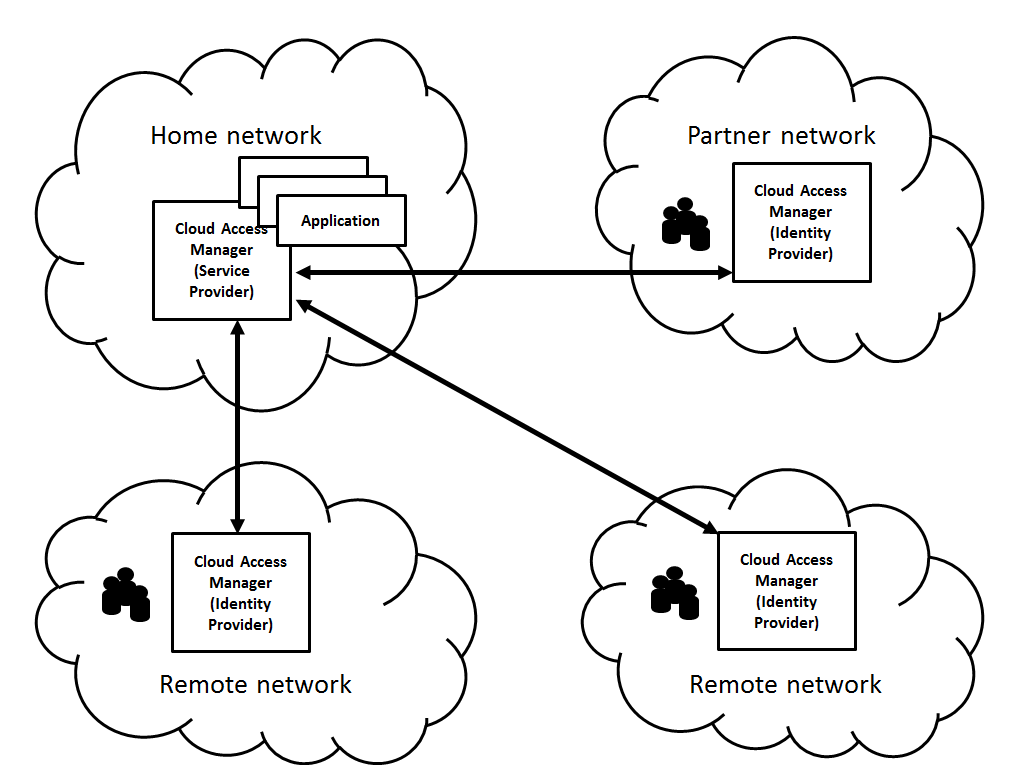
Dell™ One Identity Cloud Access Manager 8.1.2 - How to Configure as an Identity Provider
Prerequisites
Before starting the configuration, please make sure the following prerequisites are met:
Configuration
|
• |
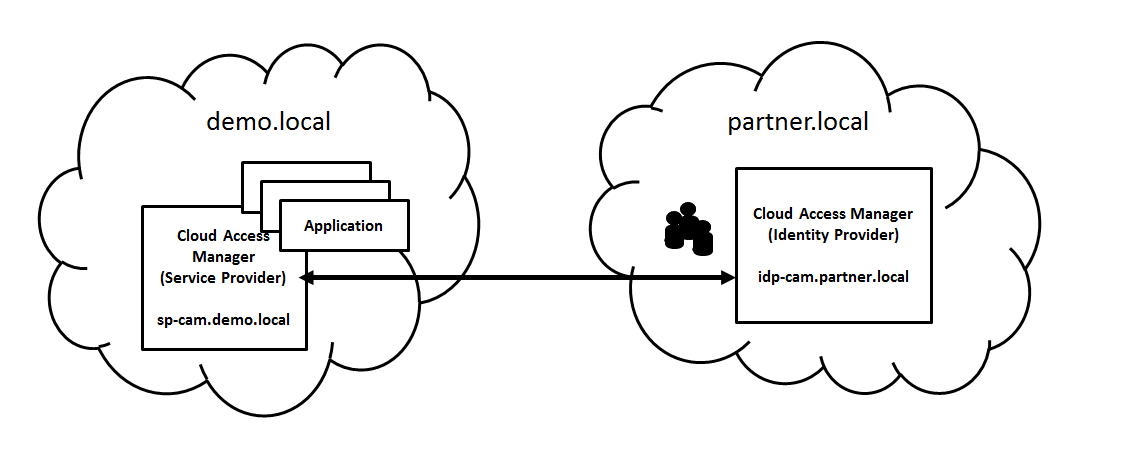
Configuring the SAML application on idp-cam.partner.local describes how to configure the Identity Provider (IDP) Cloud Access Manager instance (on idp-cam.partner.local) with a SAML application to define the service provider (SP) Cloud Access Manager instance (on sp-cam.demo.local). |
|
• |
Setting up the front-end Authenticator in sp-cam.demo.local describes how to configure the SP Cloud Access Manager instance (on sp-cam.demo.local) with a front-end authenticator (FEA) definition for the IDP Cloud Access Manager instance (on idp-cam.partner.local). |
|
• |
Testing your configuration describes how to test a federated logon to the SP Cloud Access Manager instance authenticating against the IDP Cloud Access Manager instance. |
Configuring the SAML application on idp-cam.partner.local
There are two methods you can use to create the SAML application:
|
2 |
|
3 |
In the Create an Application Using a Template section select the Dell One Identity Cloud Access Manager template. |
|
4 |
On the Settings for Cloud Access Manager enter sp-cam.demo.local as the Cloud Access Manager hostname and then click Save & Next. |
|
5 |
|
6 |
|
7 |
Click Next. |
|
8 |
The Permissions page is displayed. Here you can grant or deny access to the application based on role membership. Select Allow Role Access to specify which roles will have access to Cloud Access Manager. |
|
10 |
Click Next. |
|
12 |
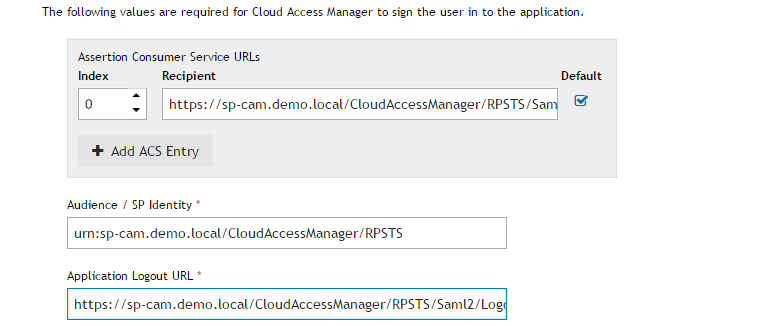
The Federation Settings page provides you with information that you may need to configure your Service Provider. In this example, we will generate metadata to set up our Service Provider. Click Download Metadata and transfer the downloaded file to your sp-cam.demo.local machine. |
|
2 |
|
3 |
|
4 |
|
5 |
|
6 |
|
7 |
|
8 |
Click Next. |
|
9 |
Click Next to advance to the External Access page. This asks you whether the application should be proxied for situations where external users are required to access applications on your internal network. When Cloud Access Manager is operating as an IDP, the application (SP) does not run on your internal network and therefore this is not required. Select Do not proxy this application. |
|
10 |
Click Next. |
|
11 |
The Permissions page is displayed. Here you can grant or deny access to the application based on role membership. Select Allow Role Access to specify which roles will have access to Cloud Access Manager. |
|
13 |
Click Next. |
|
15 |
The Federation Settings page provides you with information you may need to configure your Service Provider. In this example, we will generate metadata to set up our Service Provider. Click Download Metadata and transfer the downloaded file to your sp-cam.demo.local machine. |
|
2 |
|
4 |
Select the Claim Mapping section. |
|
5 |
Select the Send Cloud Access Manager role claim checkbox. |
|
6 |
Click Finish. |
- Herramientas de autoservicio
- Base de conocimientos
- Notificaciones y alertas
- Soporte de productos
- Descargas de software
- Documentación técnica
- Foros de usuarios
- Tutoriales en video
- Aviso de actualizaciones de páginas web (RSS)
- Comuníquese con nosotros
- Obtenga asistencia con las licencias
- Soporte Técnico
- Ver todos