Authenticating Web site users
The next diagram illustrates a scenario where Defender is configured to authenticate the users who access Web sites hosted on Microsoft Internet Information Services (IIS).
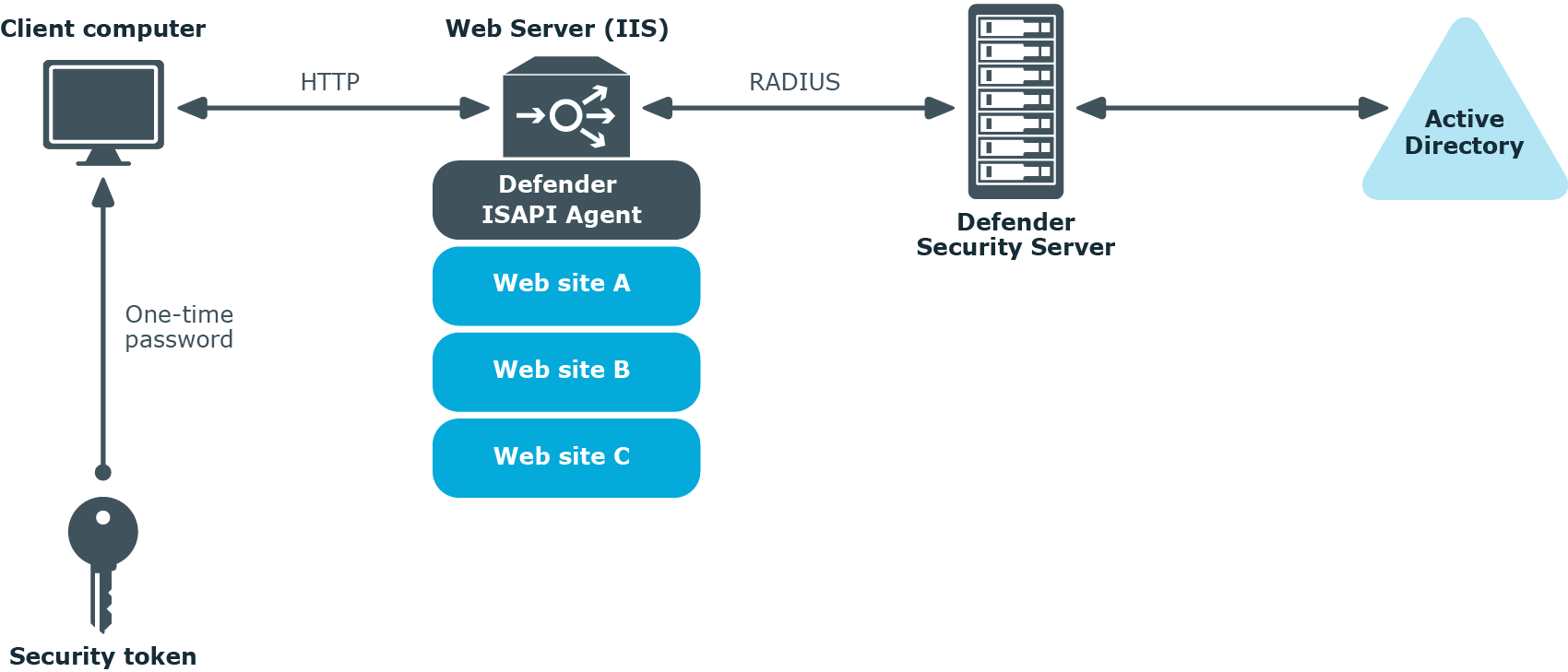
In this scenario, the Defender ISAPI Agent must be deployed on the Web Server that hosts the Web sites to be secured with Defender. The ISAPI Agent acts as an ISAPI filter and requires users to authenticate via Defender in order to get access to the Web sites hosted on the Web Server.
Authenticating users of Windows-based computers
Defender can also be configured to authenticate users when they sign in to their workstations running the Windows operating system.
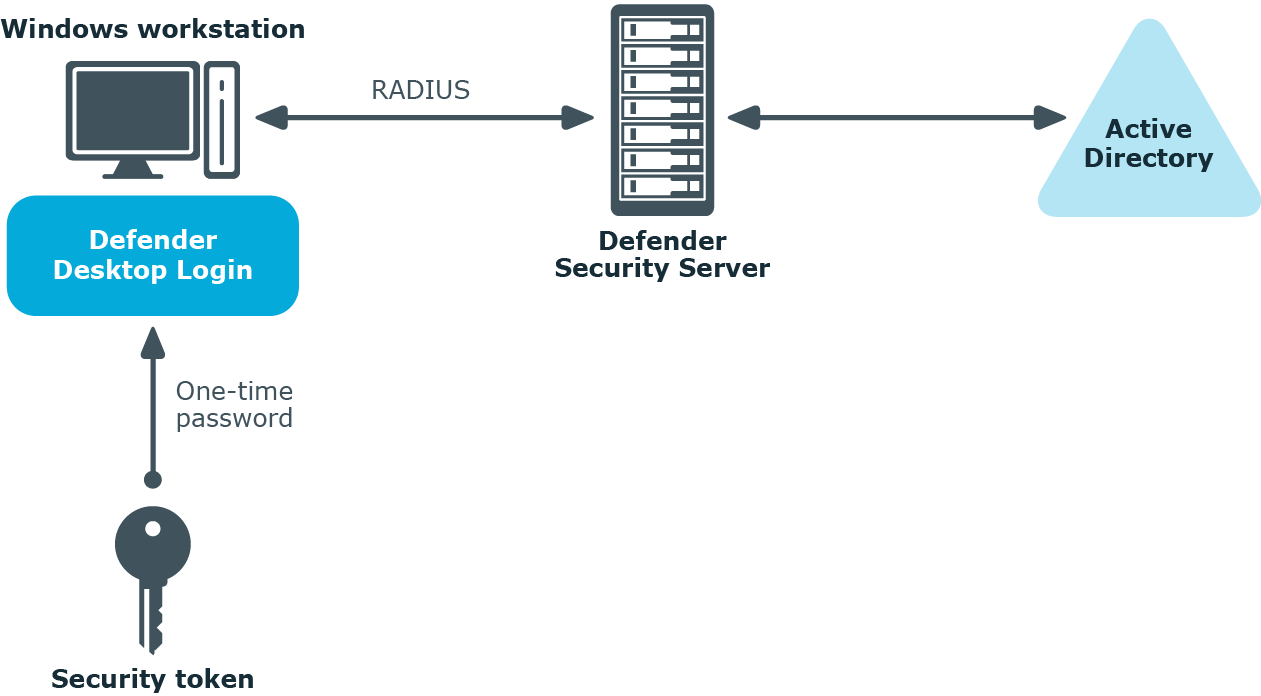
To implement this scenario, you need to install and configure a component called the Defender Desktop Login on each Windows workstation whose users you want to authenticate via Defender.
Deploying Defender
This section describes how to install Defender for the first time. Before you start, make sure that:
You can install Defender on physical computers or virtual machines. To install Defender for the first time, complete the following steps:
By completing these steps, you get a base Defender configuration which you can then extend to suit your needs. For example, you can extend the base configuration to do the following:
- Authenticate users who access you company’s resources via VPN. For more information, see “Securing VPN access” in the Defender Administration Guide.
- Authenticate users when they access Web sites hosted on Microsoft Web Server (IIS). For more information, see “Securing Web sites” in the Defender Administration Guide.
- Authenticate users when they sign in to their Windows-based computers. For more information, see “Securing Windows-based computers” in the Defender Administration Guide.
- Authenticate users when they access a PAM-enabled service in UNIX or Linux. For more information, see “Securing PAM-enabled services” in the Defender Administration Guide.
Step 1: Install required Defender components
To install the required Defender components
- In the Defender distribution package, open the Setup folder, and run the Defender.exe file.
- Complete the Defender Setup Wizard to install the required Defender components.
- For more information about the wizard steps and options, see Defender Setup Wizard reference.


