The One Identity Manager Administration Guide for Connecting to LDAP describes how you set up synchronization of LDAP with One Identity Manager. The guide explains how to use One Identity Manager to manage the user accounts and groups of your LDAP environment.
This guide is intended for end users, system administrators, consultants, analysts, and any other IT professionals using the product.
NOTE: This guide describes One Identity Manager functionality available to the default user. It is possible that not all the functions described here are available to you. This depends on your system configuration and permissions.
Available documentation
You can access One Identity Manager documentation in the Manager and in the Designer by selecting the Help > Search menu item. The online version of One Identity Manager documentation is available in the Support portal under Technical Documentation. You will find videos with additional information at www.YouTube.com/OneIdentity.
One Identity Manager allows administration of objects, such as identities, groups, and organizational units that are managed in an LDAP directory. The LDAP mapping in One Identity Manager should be seen as a suggestion, and seldom corresponds to the property mapping in a custom LDAP directory. Whether, or how, the available properties will be used depends on the respective LDAP schema in use, and must be custom configured.
The default One Identity Manager installation concentrates on identity administration and their user accounts, user groups, and LDAP directory organizational units. The One Identity Manager data model is designed to manage administration of LDAP directory computers and servers.
One Identity Manager supplies templates for synchronization with several server systems. However, the synchronization connection has to be custom configured in any case.
Company identities are provided with the necessary user accounts in One Identity Manager. Different mechanisms can be used to link identities to their user accounts. These user accounts can also be managed separately from identities and therefore administrative user accounts can be set up. In order to provide the required permissions, LDAP groups are managed in One Identity Manager. In One Identity Manager, you can also manage organizational units in a hierarchical structure. Organizational units (branches or departments) are used to logically organize the objects in an LDAP directory such as user accounts and groups and thus make administration easier.
NOTE: The LDAP module must be installed as a prerequisite for managing One Identity Manager in LDAP Module For more information about installing, see the One Identity Manager Installation Guide.
In One Identity Manager, the following servers play a role in managing LDAP:
-
LDAP server
The LDAP server with the LDAP directory. This server is a selected live server with a good network connection to the synchronization server. The synchronization server connects to this server in order to access the LDAP objects.
-
Synchronization server
Synchronization server for synchronizing One Identity Manager data with LDAP. The One Identity Manager Service with the LDAP connector is installed on this server. The synchronization server connects to the LDAP server.
The LDAP connector is used for synchronization and provisioning LDAP. The LDAP connector communicates directly with an LDAP server.
Figure 1: Architecture for synchronization
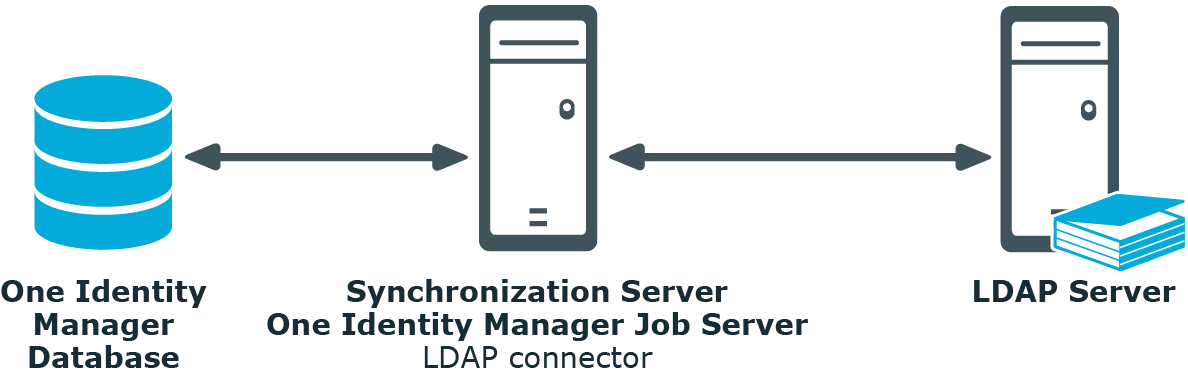
The following users are used for setting up and administration of LDAP.
Table 1: Users
| Target system administrators |
Target system administrators must be assigned to the Target systems | Administrators application role.
Users with this application role:
-
Administer application roles for individual target system types.
-
Specify the target system manager.
-
Set up other application roles for target system managers if required.
-
Specify which application roles for target system managers are mutually exclusive.
-
Authorize other identities to be target system administrators.
-
Do not assume any administrative tasks within the target system. |
| Target system managers |
Target system managers must be assigned to the Target systems | LDAP or a child application role.
Users with this application role:
-
Assume administrative tasks for the target system.
-
Create, change, or delete target system objects.
-
Edit password policies for the target system.
-
Prepare groups to add to the IT Shop.
-
Can add identities that do not have the Primary identity identity type.
-
Configure synchronization in the Synchronization Editor and define the mapping for comparing target systems and One Identity Manager.
-
Edit the synchronization's target system types and outstanding objects.
-
Authorize other identities within their area of responsibility as target system managers and create child application roles if required. |
| One Identity Manager administrators |
administrator and administrative system users Administrative system users are not added to application roles.
administrators:
-
Create customized permissions groups for application roles for role-based login to administration tools in the Designer as required.
-
Create system users and permissions groups for non role-based login to administration tools in the Designer as required.
-
Enable or disable additional configuration parameters in the Designer as required.
-
Create custom processes in the Designer as required.
-
Create and configure schedules as required.
-
Create and configure password policies as required. |
| Administrators for the IT Shop |
Administrators must be assigned to the Request & Fulfillment | IT Shop | Administrators application role.
Users with this application role:
|
|
Product owner for the IT Shop |
Product owners must be assigned to the Request & Fulfillment | IT Shop | Product owners application role or a child application role.
Users with this application role:
|
| Administrators for organizations |
Administrators must be assigned to the Identity Management | Organizations | Administrators application role.
Users with this application role:
|
| Business roles administrators |
Administrators must be assigned to the Identity Management | Business roles | Administrators application role.
Users with this application role:
|

