The rest of the guide will walk you through the steps required after the installation to get you started. You will learn how to do the following in the next sections:
-
Review and customize your network settings.
-
Configure a basic SSH Connection Policy.
-
Understand and customize the most important options around authentication and destination selection.
-
Understand and test real-time activity monitoring and Four Eyes Authorization.
-
Configure a basic RDP Connection Policy.
-
Understand and configure screen content indexing.
-
Understand and test the main functions of the search interface for audit recordings.
To start the setup of SPS
-
Connect to SPS.
The SPS virtual machine acquires an IP address from your DHCP server accessible in the virtual environment. After SPS has booted up, the console displays the IP address of the SPS web interface at login prompt. To connect to SPS, use this IP address. For details, or tips if SPS cannot receive an IP address, see The initial connection to One Identity Safeguard for Privileged Sessions (SPS) in the Administration Guide.
-
Complete the Welcome Wizard as described in Configuring One Identity Safeguard for Privileged Sessions (SPS) with the Welcome Wizard in the Administration Guide. Upload the evaluation license file you have downloaded with your support portal account.
General connection settings
SPS supports transparent and non-transparent proxy operation modes to make deployments in existing network infrastructures as easy as possible. SPS will automatically handle non-transparent and transparent connections simultaneously.
The following operation modes are possible:
-
Non-transparent proxy operation: This guide will focus on this operation mode.
-
Transparent mode: If you configure SPS proxies in transparent mode, the client usually addresses the target server directly. Therefore, you have to configure the connection policies in SPS accordingly. For more information, see Transparent mode in the Administration Guide.
-
Single-interface transparent mode: For more information, see Single-interface transparent mode in the Administration Guide.
Non-transparent proxy operation
This guide focuses on non-transparent proxy operation, which is the easiest to implement. In this configuration, clients connect to a server through SPS. That is, end-users address SPS explicitly, which then forwards connections to target systems based on various parameters depending on what destination selection method you select.
Figure 1: SPS in non-transparent mode
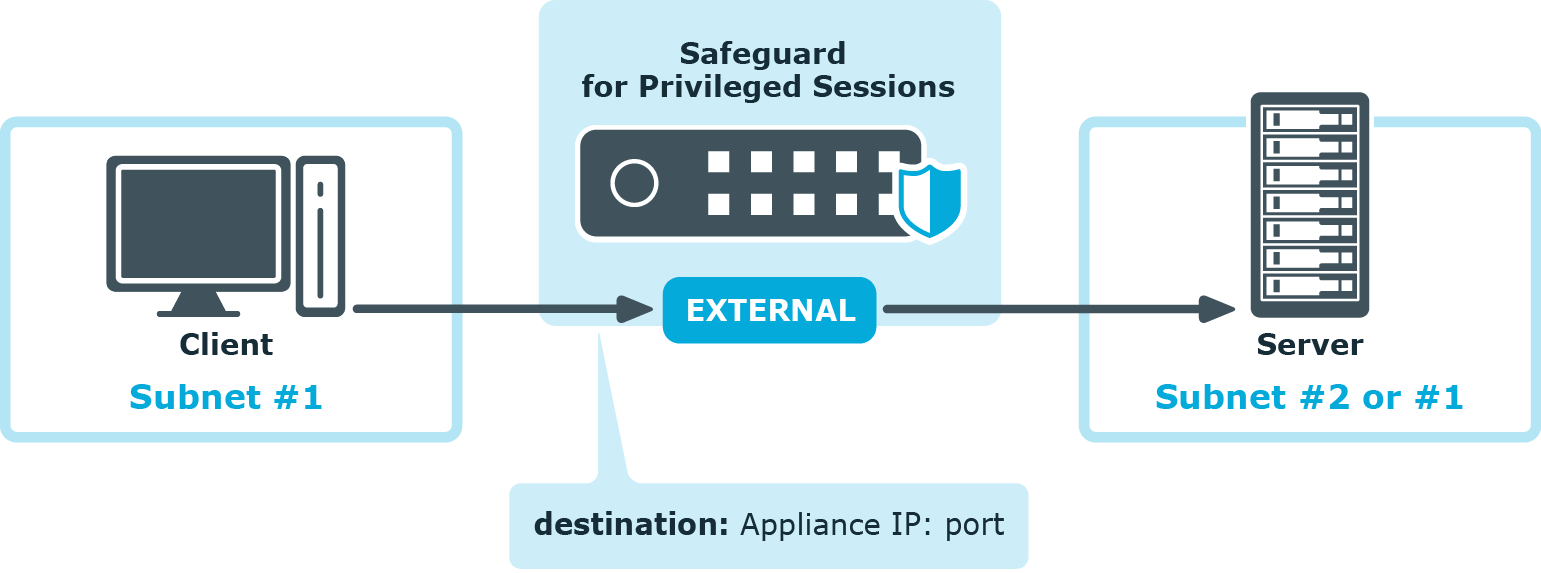
For an illustration of what happens when a client connects a server through SPS and how the different configuration options and policies of SPS affect this process, see:
-
Connecting to a server through One Identity Safeguard for Privileged Sessions (SPS) using SSH in the Administration Guide
-
Connecting to a server through One Identity Safeguard for Privileged Sessions (SPS) using RDP in the Administration Guide

