By default, Active Roles attempts to create or rename a (non-local) home folder on the file server when the Home Directory property is set or modified on a user account in Active Directory. If creation or renaming of the home folder fails (for example, because the file server is inaccessible), then the creation or modification of the user account fails, as well. To prevent such an error condition, a Home Folder AutoProvisioning policy can be configured so that Active Roles applies the changes to the Home Drive and Home Directory properties in Active Directory without attempting an operation on the file server. This policy option enables the use of a tool other than Active Roles for creating home folders on the file server.
Active Roles comes with a preconfigured Policy Object that allows the creation or renaming of home folders when setting home folder properties on user accounts in Active Directory. The Policy Object is located in the Configuration/Policies/Administration/Builtin container in Active Roles Console tree. The name of the Policy Object is Built-in Policy - Default Rules to Provision Home Folders. If you want to prevent Active Roles from attempting to create or rename home folders, you can modify the policy in the built-in Policy Object or configure and apply another Home Folder AutoProvisioning policy with the respective option turned off.
You can create a new Home Folder AutoProvisioning policy with the Active Roles Console.
To configure a Home Folder AutoProvisioning policy
-
On the Policy to Configure page, select Home Folder AutoProvisioning, then click Next.
Figure 49: Home folder management
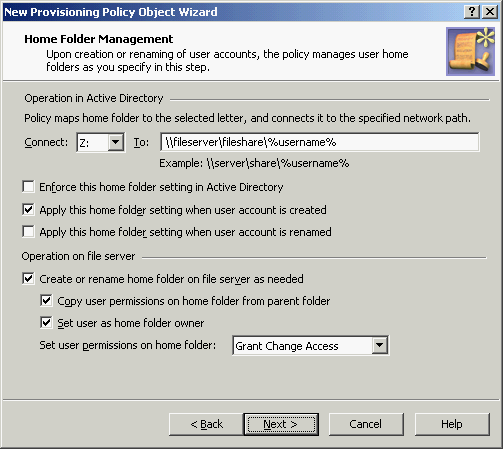
-
On the Home Folder Management page, do the following:
-
From the Connect list, select the drive letter to which you want the policy to map the home folder.
-
In the To box, specify a network path to the home folder. The path must include a common share at one level above the home folders. For example, if you want to create home folders on the share Home of the server Ant, use the following path:
\\Ant\Home\%username%
NOTE: Paths containing just the server and username, like \\SERVER\%username% are not valid.
-
To have the policy verify that the home folder path and name on user accounts are set in compliance with this policy, select Enforce this home folder setting in Active Directory.
When this check box is cleared, the policy allows home folder paths and names that differ from the path and name prescribed by the policy.
-
To have Active Roles automatically set the home folder properties in accord with this policy upon user account creation in Active Directory, select Apply this home folder setting when user account is created.
-
To have Active Roles automatically set the home folder properties in accord with this policy upon user account renaming in Active Directory, select Apply this home folder setting when user account is renamed.
-
To have Active Roles attempt creation or renaming of a (non-local) home folder on the file server when home folder properties are set or changed on a user account in Active Directory, select Create or rename home folder on file server as needed.
If you want to configure the policy so that it not only sets home folder properties on user accounts in Active Directory but also creates or renames home folders and home shares in accord with the policy settings, you must keep the Create or rename home folder on file server as needed check box selected (this is the default setting). If the check box is cleared, then the policy can only set or verify home folder properties on user accounts in Active Directory.
-
Specify how you want the policy to configure permission settings on home folders. You can choose from the following options:
-
Copy user permissions on home folder from parent folder: Upon creation or renaming of a home folder for a user account, ensures that the user account has the same rights on the home folder as on the folder in which the home folder resides.
-
Set user as home folder owner: Upon creation or renaming of a home folder for a user account, ensures that the user account is set as the owner of the home folder.
-
Set user permissions on home folder: Upon creation or renaming of a home folder for a user account, ensures that the user account has the specified access rights on the home folder (such as Change Access or Full Access).
Click Next.
-
On the Home Share Management page, specify settings for user home shares. Do the following:
-
Select Create home share when home folder is created or renamed for the policy to create or rename the home share when creating or renaming the home folder.
-
(Optional) In Share name prefix and Share name suffix, type a prefix and suffix for the name of the home share.
-
(Optional) In Description, type a comment to add to the home share.
-
If you want to limit the number of users that can connect to the share at a time, click Allow this number of users and specify the maximum number of users in the box next to that option. Otherwise, click Maximum allowed.
Click Next.
-
On the Enforce Policy page, you can specify objects to which this Policy Object is to be applied:
-
Click Next, then click Finish.
Upon creation or renaming of a user account, the policy can configure the user account in Active Directory to connect the home folder to the specified network path. From the Connect list, select the drive letter to which you want the policy to map the home folder. In the To box, specify a network path to the home folder. Ensure that the path meets the following requirements:
-
A valid network path must begin with the UNC name of a network file share, such as \\Server\Share\, and should normally include the %username% notation. For example, with the Connect: Z: To: \\Server\Share\%username% option, the policy can configure a user account in Active Directory so that the Home Drive property of the user account is set to Z: and the Home Directory property of the user account is set to \\Server\Share\LogonName where LogonName stands for the pre-Windows 2000 logon name of the user account.
-
The path must include a common share at one level above the home folders. For example, if you type \\Comp\Home\%username%, the policy creates home folders on the share Home on the server Comp, with the name of the folder being the same as the user logon name (pre-Windows 2000). The path \\Comp\%username% is invalid.
-
The folder on the network file share in which you want the policy to create home folders must be listed in the Home Folder Location Restriction policy. For instructions on how to view or modify the list see Configuring the Home Folder Location Restriction policy.
-
If you want the policy to create home shares (see Set user permissions on home folder), you should not specify an administrative share, such as C$, as the common share in the To box. Otherwise, the policy may be unable to create home shares when creating home folders. Thus, if you specify \\Comp\C$\%username%, the policy can successfully create home folders in the folder C:\ on the computer Comp, but it may fail to create home shares.
Use this option to have Active Roles verify whether the Home Drive and Home Directory properties on user accounts in Active Directory are in compliance with the Connect: <drive letter> To: <network path> setting specified by this policy.
For example, with the Connect: Z: To: \\Server\Share\%username% policy setting, this option causes a policy violation condition in Active Roles upon an attempt to modify a user account so that the Home Drive property is assigned a drive letter other than Z: or the Home Directory property is assigned a network path other than \\Server\Share\LogonName where LogonName stands for the pre-Windows 2000 logon name of the user account.
When this option is turned off, the policy allows a home folder path and name that differs from the path and name prescribed by this policy. A Property Generation and Validation policy can be configured to generate the Home Drive and Home Directory properties on user accounts, or those properties can be specified manually. In either case, Active Roles updates the user account so that the folder with the specified path and name is set as the user home folder. If necessary, Active Roles creates the folder.
When this option is turned on, the policy behaves as follows:
-
It ensures that the path and name of the home folder is in compliance the policy settings. If a different path or name is specified upon creation or modification of a user account, the policy does not allow the changes to the home folder path and name to be committed to the directory.
-
The Check Policy command causes the policy to verify the existing home folder settings. The policy check results inform about policy violations, if any, and provide the ability to fix the home folder path and name settings on user accounts so as to bring them into compliance with the policy settings.
By selecting the Enforce this home folder setting in Active Directory check box, you ensure that the home folders on user accounts are set in compliance with this policy.
By clearing the check box, you get the option of applying a Property Generation and Validation policy in order to generate and validate the Home Drive and Home Directory properties, and thus have Active Roles create and assign home folders in accordance with the flexible, highly customizable rules provided by a Property Generation and Validation policy.
IMPORTANT: When setting the Home Drive and Home Directory properties, Active Roles does not create the home folder if the network path of the folder to hold the home folder is not listed in the Home Folder Location Restriction policy. The policy defines a list of the folders on network file shares in which creation of home folders is allowed, and prevents Active Roles from creating home folders in other network locations. For instructions on how to view or modify the policy settings, see Configuring the Home Folder Location Restriction policy.

