Password Manager Credential Checker
The Password Manager Credential Checker is based on PowerShell scripts used to check if the user’s password is compromised. Credential Checker deals with actions related to change password, reset password, change password in ADLDS and connected systems, or reset password in ADLDS and connected systems. By default, the Credential Checker PowerShell script implements VeriClouds CredVerify functionality for leaked password with hash segment.
|

|
IMPORTANT: If you prefer to use other credential checker service, modify the Credential Checker PowerShell script appropraitely. |
Configuring Password Manager credential checker
-
After the Password Manager is installed, on the Password Manager Administrator portal, go to General settings | Extensibility and select Turn the credential checker mode on or off to enable the feature.
- On the Password Manager installation path, open the compromised_password_checker script. It is available in the <installation location\One Identity\Password Manager\Service\Resources\CredentialChecker> location.
- Edit the script to provide the Vericlouds credentials:
$url=<valid URL>
$api_key=<valid Key>
$api_secret=<valid api secret>
- Save the file.
When you enter a new password on the Self-Service site using any of the workflows, such as, Forgot Password or Manage My Passwords, the Credential Checker validates the new password and check if it matches with the passwords listed in the VeriClouds. If the password matches, Provided password is compromised, type another password. If you've ever used it anywhere before, change it! is displayed.
This feature is not applicable if the user changes the password using CTRL+ALT+ DELETE on the Windows logon screen.
Typical Deployment Scenarios
This section describes typical deployment scenarios for Password Manager, including scenarios with installation of the Self-Service and Helpdesk sites on standalone servers, using realms, and others.
Simple Deployment
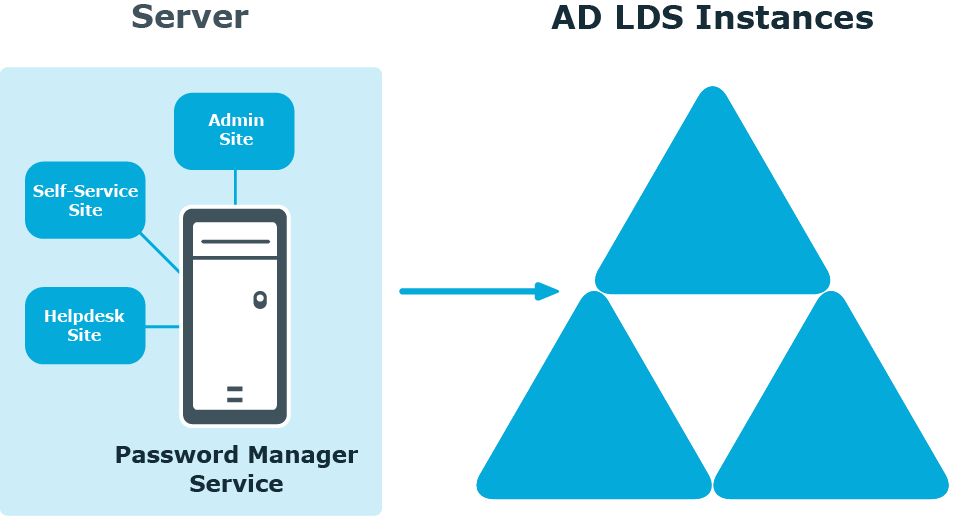
In this scenario, you install all main Password Manager components, i.e. the Password Manager Service, Administration, Self-Service and Helpdesk sites on a single server. This is the simplest deployment scenario, which can be used in small environments and for demonstration purposes.
Deployment of the Self-Service and Helpdesk Siteson Standalone Servers
Deployment of the Legacy Self-Service, Password Manager Self-Service Site, and Helpdesk Sites on Standalone Servers
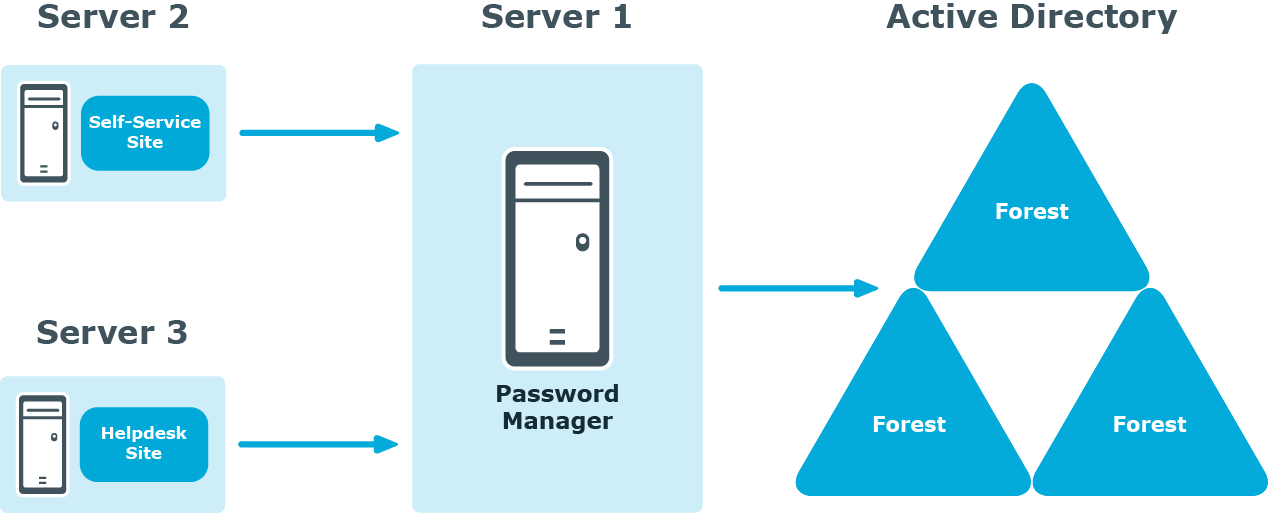
In this scenario, you install the Self-Service and/or Helpdesk sites on a standalone server. Note, that the Administration site cannot be installed separately from the Password Manager Service.
You can use this scenario to deploy Password Manager in an environment with a perimeter network. Installation of the Self-Service site in the perimeter network enhances security of your environment while preventing access to your internal network.
When deploying Password Manager in an environment with the perimeter network, it is recommended to do a full installation of Password Manager in the internal corporate network, and then install the Self-Service site in the perimeter network.
When deploying Password Manager in an environment with the perimeter network, it is recommended to do a full installation of Password Manager in the internal corporate network, and then install the Self-Service site in the perimeter network.
When you use this installation scenario, only one port should be open in the firewall between the corporate network and the perimeter network (by default, port number 8081 for the Self-Service site).



