When you install from the product ISO, the setup wizard copies available software packages to a default location on the local computer.
The default directories are:
- On Windows platforms: %SystemDrive%:\Program Files\Quest Software\Management Console for Unix\software\qas\default
- On Unix and Linux platforms: /opt/quest/mcu/software/qpm/default
Note: If you install Management Console for Unix from the Authentication Services ISO, the "default" directory is replaced with the Authentication Services version number.
If you plan to install Authentication Services software onto your hosts from the console, you must ensure the path to the packages is correctly set in System Settings.
To ensure the path to the Authentication Services software packages is correctly set
- Make note of where your Authentication Services software packages are located.
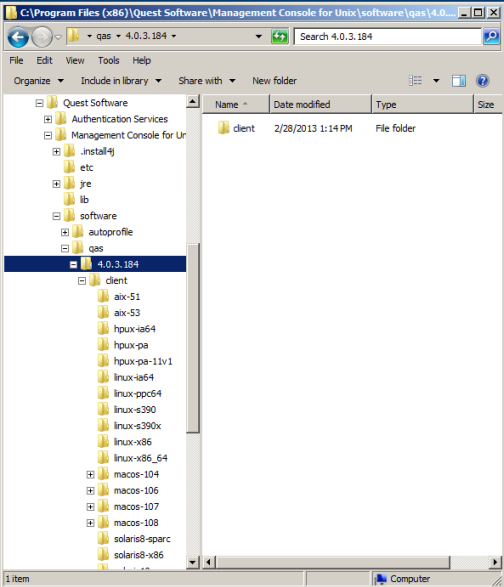
-
Log onto the mangement console using the supervisor account or an Active Directory account with rights to change System Settings; that is, an account in the Console Administration role. See Console Roles and Permissions system settings for details.
-
From the top-level Settings menu, navigate to System settings | Authentication Services.

-
In the Path box, enter the path where the Authentication Services software packages are located on the server.
-
Click OK to save your selection and close System Settings.
While the mangement console always allows you to add Unix hosts and manage local users and groups without a license, One Identity provides a free 30-day unlimited-use trial license that allows you to manage any number of hosts with Authentication Services 4.x.
License Alerts
After your license expires you will receive a "license" alert if you continue to use the product after the expiration date. The alert is triggered when you log into the console or update licenses from System Settings.
Usage Alerts
You will receive a "usage" alert if you exceed the number of hosts allowed by your current product license.
To refresh Authentication Services license information in the console
-
Log onto the mangement console using the supervisor account or an Active Directory account with rights to change System Settings; that is, an account in the Console Administration role.
-
From the top-level Settings menu, navigate to System settings | Authentication Services.
-
Click Check for licenses.
Note: If the mangement console is not configured for Active Directory that option is disabled.
-
Click OK to save the System Settings and return to the mangement console.
Note: The Import Authentication Services Licenses feature does not upload the license to the Authentication Services license application container in Active Directory; it only imports it to the console server for use by Management Console for Unix.
To import a Authentication Services license
-
Log onto the mangement console using the supervisor account or an Active Directory account with rights to change System Settings; that is, an account in the Console Administration role.
-
From the top-level Settings menu, navigate to System settings | Authentication Services.
-
Click Import.
-
Browse for the license file and click OK.


