Server host keys
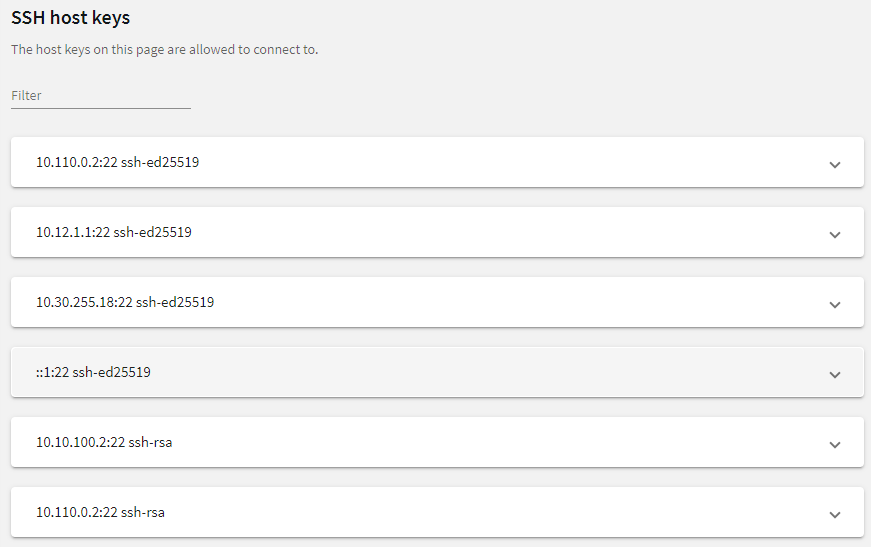
The host keys of the trusted servers can be managed on the SSH Control > Server Host Keys page. When a client tries to connect to a server, One Identity Safeguard for Privileged Sessions (SPS) verifies the host key of the server. SPS allows connections only to the servers listed on this page, unless the Accept key for the first time or the Accept certificate for the first time option is enabled in the connection policy.
Figure 242: SSH Control > Server Host Keys — Server host keys
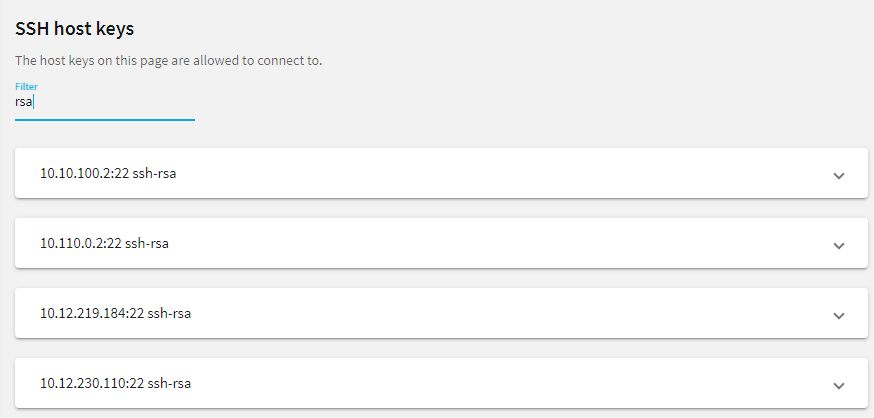
To filter, start typing into the Filter field. For example, enter rsa or an IP address and only relevant results are displayed.
Figure 243: SSH Control > Server Host Keys — Filtered RSA host keys
Automatically adding the host keys of a server to One Identity Safeguard for Privileged Sessions (SPS)
The host keys of the servers can be added either automatically or manually.
To add the host key automatically
-
Navigate to the SSH Control > Connections.
-
Configure a connection: fill the From, To, and Port fields.
You can use IPv4 and IPv6 addresses as well.
-
To configure a transparent connection, enter the IP address of the server into the To field.
-
To configure a non-transparent connection, enter the IP address of SPS into the To field, and the address of the target server into the Target field.
-
Click  to display the advanced settings and verify that the Server side host key settings > Plain host key check option is set to Accept key for the first time.
to display the advanced settings and verify that the Server side host key settings > Plain host key check option is set to Accept key for the first time.
Click  .
.
-
Initiate an SSH connection from the client to the server. SPS will automatically record the host key of the server — the server's IP address and the host key will be listed on the SSH Control > Server Host Keys page.
Manually adding the host key of a server
The following describes how to add the host key manually.
To add the host key manually
-
Navigate to the SSH Control > Server Host Keys and click Create new.
Figure 244: SSH Control > Server Host Keys — Create new
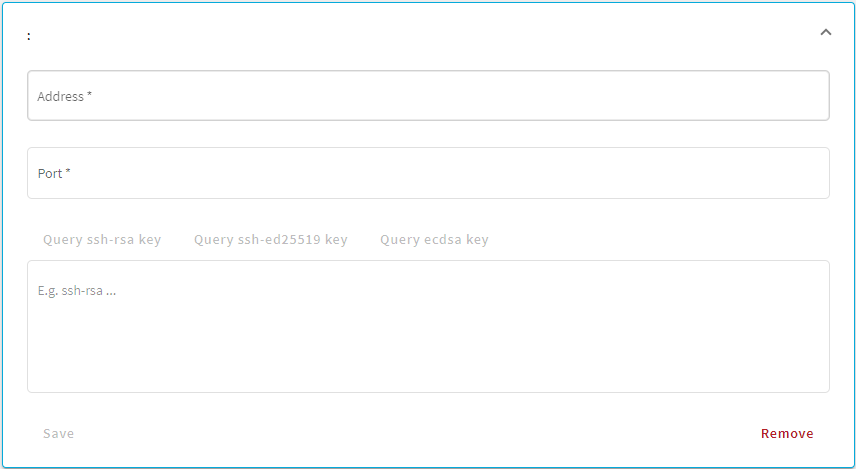
-
Enter the IP address and port of the server into the Address and Port fields.
You can use IPv4 and IPv6 addresses as well.
Figure 245: SSH Control > Server Host Keys — Example of active Query fields
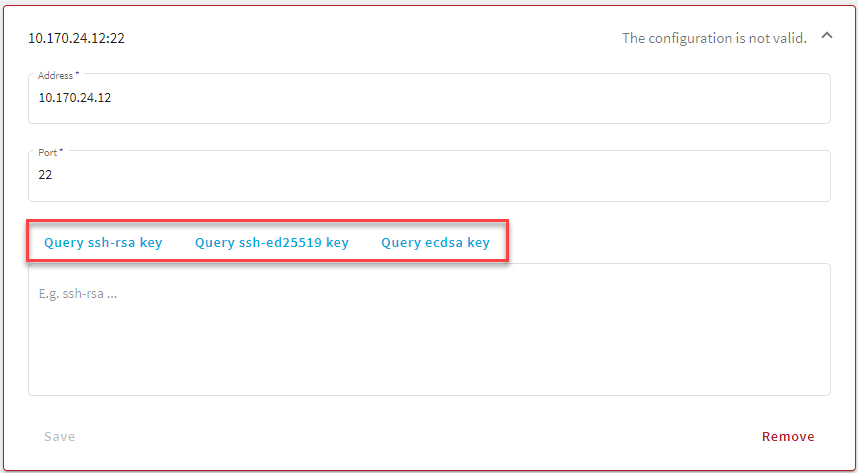
-
Once you fill out the Address and Port fields, the Query... fields become active and you can query the public part of the host key of the server.
SPS allows you to use the following SSH host keys:
-
RSA (ssh-rsa), which is the most widely used public-key algorithm for the SSH key. In SPS, uploading RSA SSH host keys are supported in PKCS #1 PEM, PKCS #8 PEM, OpenSSH (openssh-key-v1), and PuTTY private key formats.
NOTE:
TIP: One Identity recommends using 2048-bit RSA keys (or stronger).
-
Ed25519 (ssh-ed25519), which offers a better security and faster performance compared to RSA.
In SPS, uploading Ed25519 SSH host keys are supported in PKCS #8 PEM, OpenSSH (openssh-key-v1), and PuTTY private key formats.
-
ECDSA NIST P-256 (ecdsa-sha2-nistp256), which is a variant of the Digital Signature Algorithm (DSA). In SPS, uploading ECDSA SSH host keys are supported in SEC1 PEM, PKCS #8 PEM, OpenSSH (openssh-key-v1), and PuTTY private key formats.
You can have multiple SSH server host keys on SPS for the same server, however, you cannot set more than one key for each type. For example, you can keep your old RSA SSH key and generate a new Ed25519 key but you cannot set two RSA keys.
Alternatively, paste the public part of the host key of the server.
-
Click Save.
Creating and editing protocol-level SSH settings
SSH settings determine the parameters of the connection on the protocol level. For example, when the server-side connection is built, the timeout value, and greeting message of the connection. The following parameters determine which algorithms are used in the connections, and can be set independently for the client and the server side: key exchange, host key, cipher, MAC, and compression algorithms.
|

|
Caution:
Before modifying any of the algorithm settings, check whether the default algorithms are supported by your SSH client and server.
If yes, then you can leave these settings untouched.
If not and you need to amend the default algorithm settings, ensure that the client and server sides are harmonized. You can either do that in One Identity Safeguard for Privileged Sessions (SPS) or on the client/server itself.
Note that modifying algorithm settings in SPS is recommended to advanced users only. If you are unsure about which settings to amend, then contact our Support Team for assistance. |
Figure 246: SSH Control > Settings — SSH settings
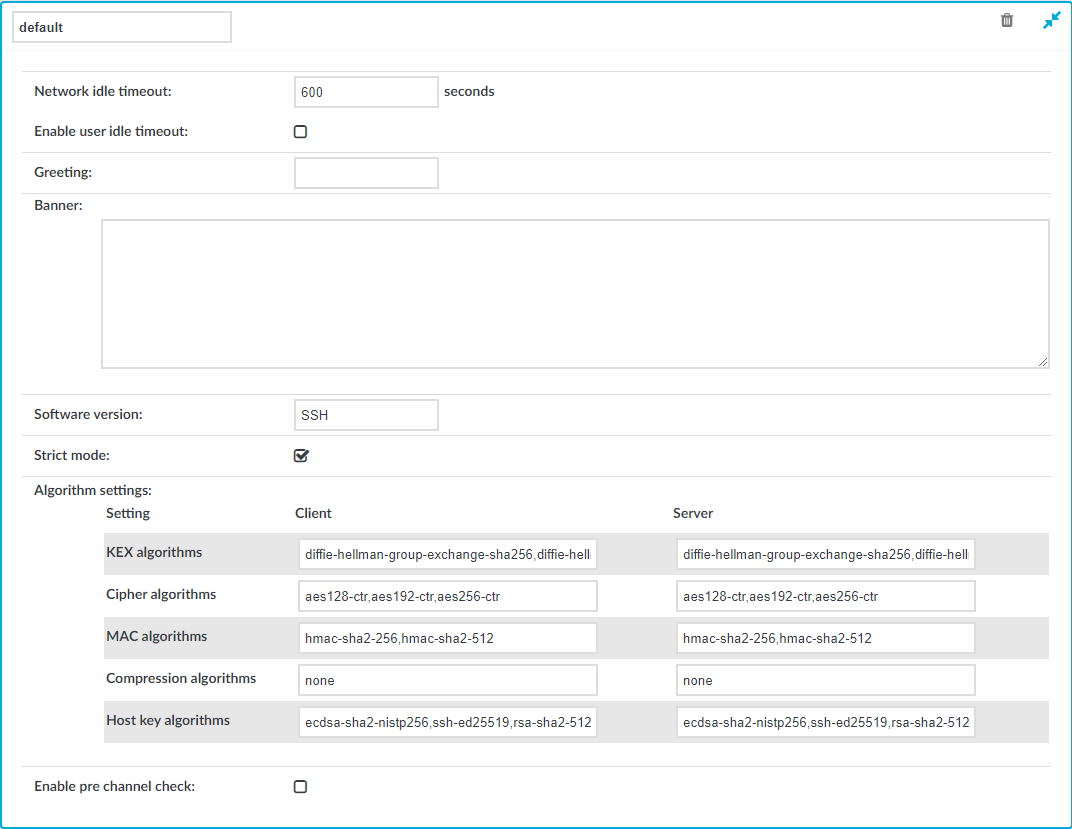
To create a new SSH settings profile or edit an existing one
-
Navigate to the SSH Control > Settings and click  to create an SSH setting profile. Enter a name for the profile (for example strongencryption).
to create an SSH setting profile. Enter a name for the profile (for example strongencryption).
-
Click  to display the parameters of the SSH connection.
to display the parameters of the SSH connection.
-
Network idle timeout: Connection timeout value in seconds. To avoid early timeout, set it to a larger value, for example a week (604800 seconds).
Even if the user is not active, the session can contain activity that must be audited (for example, the output of a script). The idle timeout period will start only after this activity has stopped.
|

|
Caution:
Determining if a connection is idle is based on the network traffic generated by the connection, not the activity of the user. For example, if an application or the taskbar of a graphical desktop displays the time which is updated every minute, it generates network traffic every minute, negating the effects of timeout values greater than one minute and preventing One Identity Safeguard for Privileged Sessions (SPS) from closing the connection. |
-
User idle timeout: If no user activity is detected, terminate the session after the configured time has passed since the last user activity.
This can be useful if only user-generated network traffic is important in a session. By using this option, situations described in the caution of Network idle timeout (such as a taskbar clock keeping the network traffic open indefinitely) can be avoided. To enable user idle timeout, select Enable user idle timeout and enter a value that is greater than or equal to the value of Network idle timeout.
-
To display a greeting message to the clients after connecting the server, enter the message into the Greeting field.
-
To display a banner message to the clients before authentication (as specified in RFC 4252 — The Secure Shell (SSH) Authentication Protocol), enter the message into the Banner field. For example, this banner can inform the users that the connection is audited.
-
Optional. You can specify additional text to append to the SSH protocol banner, for example to mask the OpenSSH version upon connection. Enter the text in the Software version field.
-
If needed, modify the encryption parameters. SPS enforces policies on the various elements of the encrypted SSH communication, such as the MAC, key-exchange, and cipher algorithms that are permitted to be used. The parameters can be set separately for the client and for the server side. The attributes are comma-separated strings listing the enabled methods/algorithms, in the order of preference.
For a complete list of the available parameters, see Supported encryption algorithms.
NOTE:
Do not use the CBC block cipher mode, or the diffie-hellman-group1-sha1 key exchange algorithm. For details, see .
-
To check the protocol-level parameters of the connections very strictly, select the Strict mode option. This option is enabled by default. When this option is enabled:
SPS will reject connections that use unrealistic parameters, for example:
SPS will reject port-forwarding connections where the address in the port-forwarding request and the channel-opening request does not match.
NOTE: Strict mode can interfere with certain client or server applications.
NOTE: Strict mode is not working with the Windows 10 internal Bash/WSL feature, because it uses a very large terminal window size. Using Windows 10 internal Bash/WSL is not supported.
-
Before establishing the server-side connection, SPS can evaluate the connection and channel policies to determine if the connection might be permitted at all, for example it is not denied by a Time Policy. To enable this function, select the Enable pre channel check option. That way SPS establishes the server-side connection only if the evaluated policies permit the client to access the server.
-
Click  .
.
-
Select this settings profile in the SSH settings field of your connections.



 to display the advanced settings and verify that the Server side host key settings > Plain host key check option is set to Accept key for the first time.
to display the advanced settings and verify that the Server side host key settings > Plain host key check option is set to Accept key for the first time. .
.



 to create an SSH setting profile. Enter a name for the profile (for example strongencryption).
to create an SSH setting profile. Enter a name for the profile (for example strongencryption).