When the agent and policy server are on different sides of a firewall, Privilege Manager for Unix needs a number of ports to be kept open. By default, Privilege Manager for Unix can use ports in the 600 to 31024 range, but when using a firewall, you may want to limit the ports that can be used. For more information, see Restricting port numbers for command responses.
This section describes
-
how Privilege Manager for Unix uses ports from both the reserved and non-reserved port ranges during a session
-
how to configure Privilege Manager for Unix over a firewall and, optionally, Network Address Translation (NAT)
For each Privilege Manager for Unix session, the client (pmrun) and agent (pmlocald) use one port from both the reserved and non-reserved ranges. The policy server (pmmasterd) uses one port from its non-reserved range. Each agent can use the same port ranges as they are on separate machines and need only be large enough to support the maximum number of concurrent sessions on that agent. On the other hand, the policy server needs a port range large enough to support all sessions across all agents (minimum of one non-reserved port per session).
This diagram shows the minimum port ranges required for a single Privilege Manager for Unix session:
Figure 7: Privilege Manager for Unix port usage
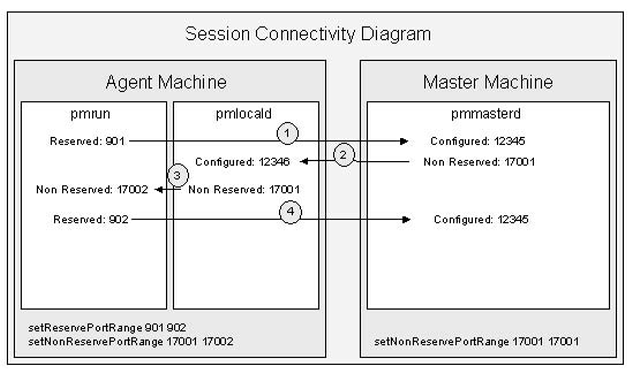
Connection 4 is used only to send back the exit status if I/O logging is not enabled.
If commands involve communication through a firewall, you can restrict the TCP/IP port numbers on which responses to pmrun commands are returned.
One Identity recommends that you assign a minimum of six ports to Privilege Manager for Unix in the reserved ports range (600 to 1023) and twice that number of ports in the non-reserved ports range (1024 to 65535). The more agents you have, the more ports you need.
To set the reserved port range
-
Add the following line to the /etc/opt/quest/qpm4u/pm.settings file:
setreserveportrange <lowportnumber> <highportnumber>
where <lowportnumber> is first port in the range and <highportnumber> is the last port in the range.
<lowportnumber> and <highportnumber> must be port numbers between 600 and 1023. For example:
setreserveportrange 600 612
To set the non-reserved port range
-
Add the following line to the /etc/opt/quest/qpm4u/pm.settings file:
setnonreserveportrange <lowportnumber> <highportnumber>
<lowportnumber> and <highportnumber> must be port numbers between 1024 and 65535. For example:
setnonreserveportrange 31000 65535
For more information about modifying the Privilege Manager for Unix configuration settings, see PM settings variables.
pmtunneld adds an additional layer of security by acting as a proxy for pmrun. Communication sent from pmlocald is transmitted using port number 12347, by default, and received by pmtunneld. pmtunneld then transmits the data to pmrun.
In the following example, the firewall is configured to allow the following connections:
-
One incoming connection from external host (EXT1) reserved port range (600 - 612) to internal host (INT1) port 12345.
-
One outgoing connection from internal host (INT1) non-reserved port range (31000 -31024) to external host (EXT1) port 12347.
Figure 8: pmtunneld configuration
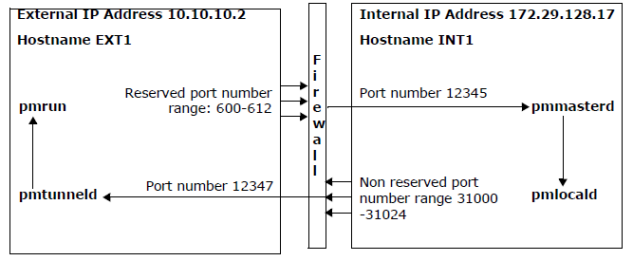
To configure pmtunneld, in the /etc/opt/quest/qpm4u/pm.settings file, specify the hosts that require pmlocald to use a fixed port when communicating with pmrun and the fixed port that pmlocald uses when communicating with pmrun.
In this example, you configure the external host (EXT1) by adding these lines to the /etc/opt/quest/qpm4u/pm.settings file:
tunnelport 12347
pmtunneldenabled yes
In this example, you configure the internal host (INT1) by adding these lines to the pm.settings file:
tunnelrunhosts EXT1
tunnelport 12347
Note that tunnelrunhosts can contain wild cards, such as, *.mydomain.com.
To allow commands to run on the external host, EXT1 in this example, create a firewall rule to allow pmmasterd to connect from the non-reserved port range to the pmlocald port on the external agent.
For more information about modifying the Privilege Manager for Unix configuration settings, see PM settings variables.


