-
Title
How to Configure Initial Random Password With a Custom Script -
Description
What are the steps to Implement Initial Random Password With a Password Script? -
Resolution
Enable and Test Initial Random Password
1. In Designer, disable the Configuration parameter UseCentralPassword (QER\Person\UseCentralPassword):
2. Enable TargetSystem\ADS\Accounts\InitialRandomPassword:
3. Disable TargetSystem\ADS\Accounts\UserMustChangePassword:
4. Commit changes to database.
5. Set the Active Directory password policy in Manager: ADS | Basic configuration data | Password policies. (Please note that password policies can also be configured in Designer: Base Data |Security settings | Password policies.)
6. To test, create a new ADSAccount in Manager. Once the provisioning task has completed, locate the new user on a Domain Controller and verify the pwdLastSet attribute has a value. If it is null, the steps have not been completed correctly. Verify settings have been saved and committed. E.g.:
Adding and Implementing a Custom Password Script
Please note that One Identity Support is unable to assist with custom scripts. Therefore it is recommended to either utilize the SDK Script Library for examples or consult with Professional Services for assistance. The script utilized in this example is a minor modification of the example script in the technical documentation.
1. Create a custom script in Designer, e.g.:
2. Save and Commit to Database then Compile the Database.
3. In Manager enter the script name in the 'Generate script' field in the master data for the Active Directory password policy on the Scripts tab:
4. On the test tab the base object must be the ADSAccount table, e.g.: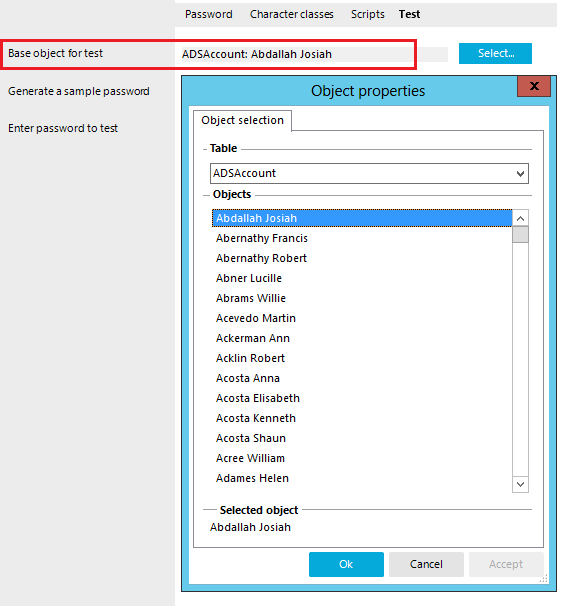
5. Click "Generate" from the "Test" tab to generate a password and confirm the script works as it should and save the changes.
For more information please refer to the Administration Guide: Custom scripts for password requirements.
