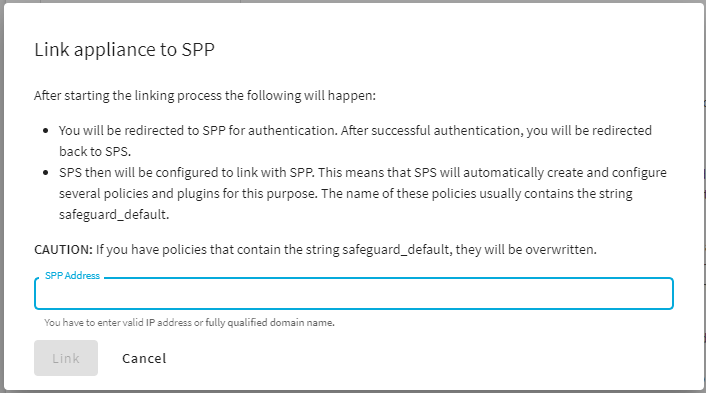
To configure SPS to use the linked SPP in Sessions-initiated (SPS-initiated) workflows, complete the following steps. For details on the workflow, see Using SPS with SPP.
Prerequisites
-
Minimum versions:
-
SPP version 2.8
-
SPS version 6.2 and newer, including 6.0.2 and newer versions of the 6.0.x branch, but excluding 6.1.x
-
-
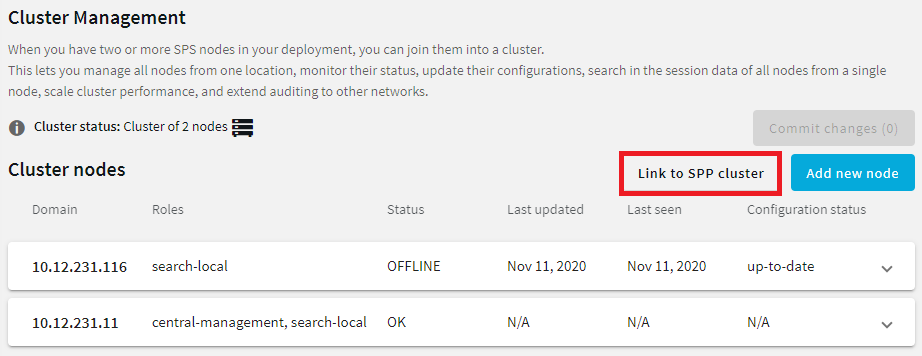
You must have built an SPS cluster by promoting an SPS node to the role of the Central Management node, even if it is a single node. For more information, see Creating a cluster.
|
|
CAUTION: When linking your One Identity Safeguard for Privileged Sessions (SPS) deployment to your One Identity Safeguard for Privileged Passwords (SPP) deployment, ensure that the SPS and SPP versions match exactly, and you keep the versions synchronized during an upgrade. For example, you can only link SPS version 6.6 to SPP version 6.6, and if you upgrade SPS to version 6.7, you must also upgrade SPP to 6.7. Make sure that you do not mix Long Term Supported (LTS) and feature releases. For example, do not link an SPS version 6.0 to an SPP version 6.1. |
Limitations
-
Only SSH and RDP sessions are supported.
-
Users must perform gateway authentication on SPS with the same username they have Entitlements for in SPP.
-
For SSH sessions, the gateway authentication can use a Local User Database, an LDAP server, or an Active Directory server as authentication backend.
Note that SPP does not support every type of LDAP and Active Directory settings that SPS does. Verify that you can configure both appliances to access and retrieve data from the LDAP or Active Directory server.
-
For RDP sessions, SPS must be configured to act as a Remote Desktop Gateway. For details, see Using One Identity Safeguard for Privileged Sessions (SPS) as a Remote Desktop Gateway.
The gateway authentication can use a Local User Database or an Active Directory server as authentication backend. When using an Active Directory server, note the following points.
-
Both SPS and SPP must use the same server, and be the member of the same domain as the Active Directory server.
-
SPP does not support every type of Active Directory settings that SPS does. Verify that you can configure both appliances to access and retrieve data from the Active Directory server.
-
SPS does not receive the domain of the authenticated user from the Domain Controller. SPS assumes that the user belongs to the same domain that SPS is joined into. (Configuring trust between the Domain Controller of SPS and the Domain Controller of the user does not solve this problem.)
-
-
-
You must use a uniform address for the target server. Use either its IPv4 address or its hostname everywhere: when configuring the Assets in SPP, the Connection Policies and Channel Policies in SPS, and also when the user sets the target address in the SSH/RDP application. Otherwise, the authentication will fail.
To configure SPS for Sessions-initiated workflow
-
Select Credential Store > safeguard_default
-
Select AA plugin > safeguard_default
-
Select Usermapping policy > safeguard_default
-
Configure gateway authentication. The users must perform gateway authentication on SPS with the same username they have Entitlements for in SPP. For details, see Configuring gateway authentication.
-
When you are using an Approve/deny workflow on SPP, increase the Idle timeout setting of the Connection Policy. SPS will wait for an approval from SPP until half the time set in Idle timeout. For example, if the authorizer on SPP has 2 minutes to approve the access request, set the Idle timeout option on SPS to more than double this value, for example, 5 minutes.
Configure Connection Policies on SPS to audit your sessions. Note that you have to complete these steps for each Connection Policy that uses SPP as a Credential Store. For the general steps on configuring Connection Policies, see Configuring connections.