One Identity Safeguard for Privileged Sessions (SPS) provides a plugin framework to integrate SPS to external systems to authenticate or authorize the user before authenticating on the target server. Such plugins can also be used to request additional information from the users, for example, to perform multi-factor authentication.
You can use an Authentication and Authorization plugin (aa-plugin) in the following protocols:
-
MSSQL
Remote Desktop (RDP)
-
Secure Shell (SSH)
-
TELNET
-
To request a plugin that interoperates with your authentication or authorization system, contact our Support Team.
-
For details on configuring SPS to use a plugin, see Using a custom Authentication and Authorization plugin to authenticate on the target hosts.
Detailed information about this topic
If a Connection Policy has an Authentication and Authorization plugin (AA plugin) configured, One Identity Safeguard for Privileged Sessions (SPS) executes the plugin as the last step of the connection authorization phase. SPS can request the client to perform other types of authentication before executing the plugin. Using an AA plugin in a Connection Policy is treated as gateway authentication if:
-
the plugin authenticates the user
-
authentication is successful
-
the plugin returns the gateway_user and gateway_groups elements, identifying the user it has authenticated
Other types of gateway authentication will come before authentication by the AA plugin, so information from any other type of gateway authentication (for example, the username and usergroups of this authentication) will already be available and therefore can be used by the plugin. If the Authentication and Authorization plugin does perform gateway authentication, you can use a Credential Store as well.
However, for technical reasons, the web-based gateway authentication (that is, authenticating on the SPS web interface if the Require Gatweay Authentication on the SPS Web Interface option is selected in the Connection Policy) is performed after the AA plugin, so using AA plugin and ticking Require Gateway Authentication on the SPS Web Interface at the same time is not a valid configuration.
The plugin can interactively request additional information from the client in the SSH, Telnet, and RDP protocols.
NOTE: In SPS 5.8, a user's group membership is determined by querying only the relevant groups configured for the connection from the LDAP/AD server, instead of retrieving all groups of a given user.
This may cause problems when using AD/LDAP-based gateway authentication together with an AA plugin. The AA plugin authorize() hook may be called with only a subset of groups as group membership lookup does not consider groups referenced in the AA plugin code.
As a possible workaround, you can add a rule to the channel policy assigned to the connection that never matches (for example, set the From address to 0.0.0.0/32), but contains all the gateway groups that the plugin requires. This channel rule will never match, but it will cause SPS to evaluate if a user is a member of those groups, and will make them available for the plugin if so.
Note that only groups queried by SPS are affected. Gateway groups returned by the AA plugin authenticate() hook are passed to the authorize() hook unchanged.
SPS executes the authorize method after the authentication method and any inband gateway authentication or inband destination selection steps. As a result, the authorize method already has access to the IP address of the target server and the remote username (the username used in the server-side connection).
Optionally, the plugin can return the gateway_user and gateway_groups values. SPS will only update the gateway username and gateway groups fields in the connection database if the plugin returns the gateway_user and gateway_groups values. The returned gateway_user and gateway_groups values override any such attributes already available on SPS about the connection (that means that channel policy evaluations will be affected), so make sure that the plugin uses the original values appropriately.
If the plugin returns the gateway_user and gateway_groups values, you may have to configure an appropriate Usermapping policy in the Connection Policy. If the plugin returns a gateway_user that is different from the remote user, the connection will fail without a usermapping policy. For details on usermapping policies, see Configuring usermapping policies in the Administration Guide.
Prerequisites
- SPS supports Authentication and Authorization plugins in the RDP, SSH, and TELNET protocols.
- In RDP, using an AA plugin together with Network Level Authentication in a Connection Policy has the same limitations as using Network Level Authentication without domain membership.
- In RDP, using an AA plugin requires TLS-encrypted RDP connections. For details, see Enabling TLS-encryption for RDP connections in the Administration Guide.
Optionally, the plugin can return the gateway_user and gateway_groups elements. SPS will only update the gateway username and gateway groups fields in the connection database if the plugin returns the gateway_user and gateway_groups elements. The returned gateway username and gateway groups override any such attributes already available on SPS about the connection, so make sure that the plugin uses the original values appropriately.
If the plugin returns the gateway_user and gateway_groups elements, you may have to configure an appropriate Usermapping Policy in the Connection Policy. If the plugin returns a gateway_user that is different from the remote user, the connection will fail without a Usermapping Policy. For details on Usermapping Policies, see Configuring usermapping policies in the Administration Guide.
The following describes how to configure One Identity Safeguard for Privileged Sessions (SPS) to use an Authentication and Authorization plugin (AA plugin) before accessing the target host.
Prerequisites
-
To use a custom plugin, you need to upload a working AA plugin to SPS. This plugin is a script that uses the SPS API to access an external system. If you want to create such a plugin, contact our Support Team for details and instructions or see Creating Custom Authentication and Authorization Plugins.
For more information on uploading plugins, see Uploading plugins.
-
Verify the integrity of the plugin.
For more information on verifying the integrity of plugins, see Verifying the integrity of a plugin.
-
SPS supports AA plugins in the MSSQL, RDP, SSH, and Telnet protocols.
-
In RDP, using an AA plugin together with Network Level Authentication in a Connection Policy has the same limitations as using Network Level Authentication without domain membership.
-
In RDP, using an AA plugin requires TLS-encrypted RDP connections. For details, see Enabling TLS-encryption for RDP connections in the Administration Guide.
To configure SPS to use an Authentication and Authorization plugin before accessing the target host
-
If your plugin supports configuration, then you can create multiple customized configuration instances of the plugin for your site. Create an instance by completing the following steps:
-
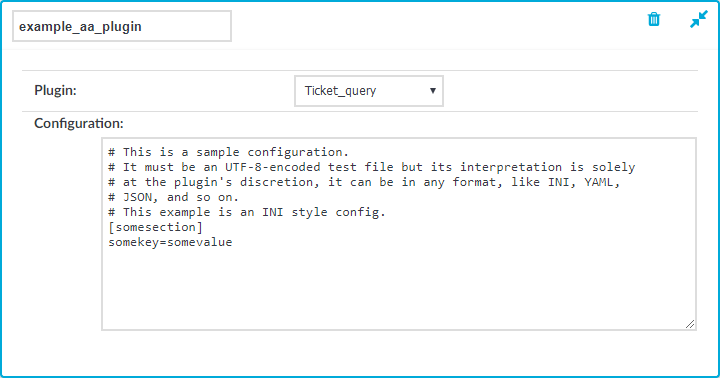
Navigate to Policies > AA Plugin Configurations. Select the plugin to use from the Plugin list.
-
The Configuration textbox displays the example configuration of the plugin you selected. You can edit the configuration here if you wish to create a customized instance of the plugin.
NOTE: Plugins created and issued before the release of SPS 5.1 do not support configuration. If you create a configuration for a plugin that does not support this, the affected connection will stop with an error message.
Figure 331: Policies > AA Plugin Configurations — Creating a customized plugin configuration instance
-
Navigate to the Connection policy where you want to use the plugin (for example, to Traffic Controls > RDP > Connections), select the plugin configuration instance to use in the AA plugin field, then click  .
.
-
If the plugin sets or overrides the gateway username of the connection, configure a Usermapping policy and use it in the Connection policy. For details, see Configuring usermapping policies in the Administration Guide.
-
Verify that the configuration works properly: try to establish a test connection. For details, see Performing authentication with AA plugin in Remote Desktop connections in the Administration Guide. If the plugin is configured to store any metadata about the connection, these data will be available in the Additional metadata field of the SPS Search interface.
The following describes how to establish a terminal connection (SSH, TELNET, or TN3270) to a server.
To establish a terminal connection (SSH, TELNET, or TN3270) to a server
-
Connect to the server.
To encode additional data as part of the username, you can use the @ as a field separator, for example:
ssh token_id=id@user@server
Replace id with your actual token ID.
-
If One Identity Safeguard for Privileged Sessions (SPS) prompts you for further information (for example, a one-time password), enter the requested information.
-
Authenticate on the server.
-
If authentication is successful, you can access the server.


 .
.