The Overview of all assignments report is displayed for some objects, such as authorizations, compliance rules, or roles. The report finds all the roles, for example, departments, cost centers, locations, business roles, and IT Shop structures in which there are employees who own the selected base object. In this case, direct as well as indirect base object assignments are included.
Examples:
-
If the report is created for a resource, all roles are determined in which there are employees with this resource.
-
If the report is created for a group or another system entitlement, all roles are determined in which there are employees with this group or system entitlement.
-
If the report is created for a compliance rule, all roles are determined in which there are employees who violate this compliance rule.
-
If the report is created for a department, all roles are determined in which employees of the selected department are also members.
-
If the report is created for a business role, all roles are determined in which employees of the selected business role are also members.
To display detailed information about assignments
-
To display the report, select the base object from the navigation or the result list and select the Overview of all assignments report.
-
Click the  Used by button in the report toolbar to select the role class for which you want to determine whether roles exist that contain employees with the selected base object.
Used by button in the report toolbar to select the role class for which you want to determine whether roles exist that contain employees with the selected base object.
All the roles of the selected role class are shown. The color coding of elements identifies the role in which there are employees with the selected base object. The meaning of the report control elements is explained in a separate legend. To access the legend, click the  icon in the report's toolbar.
icon in the report's toolbar.
-
Double-click a control to show all child roles belonging to the selected role.
-
By clicking the  button in a role's control, you display all employees in the role with the base object.
button in a role's control, you display all employees in the role with the base object.
-
Use the small arrow next to  to start a wizard that allows you to bookmark this list of employees for tracking. This creates a new business role to which the employees are assigned.
to start a wizard that allows you to bookmark this list of employees for tracking. This creates a new business role to which the employees are assigned.
Figure 3: Toolbar of the Overview of all assignments report.
Table 19: Meaning of icons in the report toolbar
|

|
Show the legend with the meaning of the report control elements |
|

|
Saves the current report view as a graphic. |
|
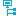
|
Selects the role class used to generate the report. |
|

|
Displays all roles or only the affected roles. |
When new user accounts are created in One Identity Manager, the passwords needed to log in to the target system are created immediately also. Various options are available for assigning the initial password. Predefined password policies are applied to the passwords, and you can adjust these policies to suit your individual requirements if necessary. You can set up email notifications to distribute the login information generated to users.
Detailed information about this topic
provides you with support for creating complex password policies, for example, for system user passwords, the employees' central password as well as passwords for individual target systems. Password polices apply not only when the user enters a password but also when random passwords are generated.
Predefined password policies are supplied with the default installation that you can use or customize if required. You can also define your own password policies.
Detailed information about this topic
You can customize predefined password policies to meet your own requirements if necessary.
Password for logging in to
The password policy is applied for logging in to . This password policy defines the settings for the system user passwords (DialogUser.Password and Person.DialogUserPassword) as well as the passcode for a one time log in on the Web Portal (Person.Passcode).
NOTE: The password policy is marked as the default policy. This password policy is applied if no other password policy can be found for employees, user accounts, or system users.
For detailed information about password policies for employees, see the One Identity Manager Identity Management Base Module Administration Guide.
Password policy for forming employees' central passwords
An employee's central password is formed from the target system specific user accounts by respective configuration. The Employee central password policy defines the settings for the (Person.CentralPassword) central password. Members of the Identity Management | Employees | Administrators application role can adjust this password policy.
IMPORTANT: Ensure that the Employee central password policy does not violate the target system-specific requirements for passwords.
For detailed information about password policies for employees, see the One Identity Manager Identity Management Base Module Administration Guide.
Password policies for user accounts
Predefined password policies are provided, which you can apply to the user account password columns of the user accounts.
IMPORTANT: If you do not use password policies that are specific to the target system, the password policy default policy applies. In this case, ensure that the default policy does not violate the target systems requirements.
NOTE: When you update version 7.x to version 8.2.1, the configuration parameter settings for forming passwords are passed on to the target system-specific password policies.
The Active Directory password policy is predefined for Active Directory. You can apply this password policy to Active Directory user accounts passwords (ADSAccount.UserPassword) of an Active Directory domain or an Active Directory container.
If the domains' or containers' password requirements differ, it is recommended that you set up your own password policies for each domain or container.
Furthermore, you can apply password policies based on the account definition of the user accounts or based on the manage level of the user accounts.
NOTE: password policies, global account policy settings for the Active Directory domain, and Active Directory account policies are all taken into account when verifying user passwords.
Ensure that the password policy does not violate the target system's requirements.
Related topics
Used by button in the report toolbar to select the role class for which you want to determine whether roles exist that contain employees with the selected base object.
icon in the report's toolbar.
button in a role's control, you display all employees in the role with the base object.
to start a wizard that allows you to bookmark this list of employees for tracking. This creates a new business role to which the employees are assigned.



