New features between SPS 5.1 and 5.11 - RDP
RDP improvements
You can now display a banner to your clients in RDP sessions. For example, this banner can inform the users that the connection is audited. For details, see "Creating and editing protocol-level RDP settings" in the Administration Guide.
Figure 7: Graphical banner in RDP
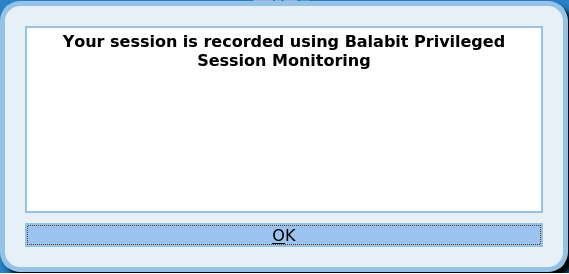
The Authentication and Authorization plugins now can request information interactively from the user in a graphical window, for example, a ticket ID, or a one-type password. To request a plugin that interoperates with your authentication or authorization system, contact our Support Team.
If the server requires Network Level Authentication and the Allow me to save credentials option is not selected in the RDP client, SPS now automatically displays a graphical prompt where the users can enter their usernames and passwords.
Figure 8: Server-side login in RDP
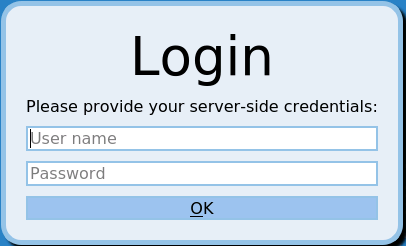
Interactive RDP improvements
When using inband destination selection, your users now do not have to encode any data in the username: SPS can display an interactive prompt in the RDP connection to request the address of the destination server, username, and other required information. For details, see "Inband destination selection in RDP connections" in the Administration Guide.
As a smaller improvement, SPS now supports using certificate chains in the signing CA used for RDP connections.
TLS-encryption for RDP connections
Enabling TLS-encryption in an RDP connection policy has been simplified. When the connection is encrypted, SPS has to show a certificate to the peer. You can define the type of certificate to show to the peers.
In case of compatibility issues, you also have the option to allow fallback to legacy RDP Security Layer (also known as: Standard RDP Security). However, it is not advised due to security reasons.
For more information, see "Enabling TLS-encryption for RDP connections" in the Administration Guide.
Windows 2019 Server support
SPS now supports Windows 2019 Server as a client and server in RDP sessions.
Certificate Revocation Lists (CRLs) in signing CAs
It is now possible to configure the CRL that you generated using your Certificate Authority (CA) in your Public Key Infrastructure (PKI) solution. This is the CRL information that will be shown to clients connecting to SPS. For more information, see "Signing certificates on-the-fly" in the Administration Guide.
New features between SPS 5.1 and 5.11 - web interface
Required minimum version of encrypted protocol
You can now configure the required minimum version of the default web listener.
The default setting is TLS 1.2. You can configure SPS to use TLS 1.0, but it is not advised, because there are known serious attacks against TLS (for details, see: https://tools.ietf.org/html/rfc7457).
For more information, see "Configuring user and administrator login addresses" in the Administration Guide.
Boot messages and upgrade logs displayed on web interface
In addition to displaying upgrade logs and boot messages on the local console, SPS now shows information about the upgrade and reboot processes on the web interface, too. The information displayed in the browser and on the console is the same. For details, see "Controlling One Identity Safeguard for Privileged Sessions (SPS): reboot, shutdown" in the Administration Guide and "Upgrade checklist" in the Administration Guide.
|
|
NOTE:
This feature is enabled after the first boot to version 5 F2 or later. So during the upgrade from 5.0 to version 6.0, you will not be able to see any upgrade logs on the web interface. |
Maximum Transmission Unit (MTU) for network interfaces
To support deployment in more complex networking environments, it is now possible to set the MTU for each network interface individually. For details, see "Network settings" in the Administration Guide and "Managing logical interfaces" in the Administration Guide.
Other changes
-
When using X.509 certificates to authenticate on the SPS web interface, SPS can now extract the name of the user from the UserPrincipalName field of the certificate. For details, see "Authenticating users with X.509 certificates" in the Administration Guide.
- Command detection and window title detection in content policies have changed and they are case-insensitive as of SPS version 5.8.0. In earlier versions, both used to be case-sensitive. For more information, see "Creating a new content policy" in the Administration Guide.
- The Indexing history section on the Indexer > Indexer status page has been removed and it is now possible to search for indexing details. For more information about the indexing search filters that you can use, see "List of available search filters" in the Administration Guide.
-
Alerts defined in Content Policies are now only sent out again if there is change in the matched screen contents to avoid flooding security administrators with alerts.
- The script used for exporting and importing the configuration of SPS through the console has changed, it is now: /opt/scb/bin/configbundle.py. As a result, the required commands have changed, too. For details, see "Exporting and importing the configuration of SPS using the console" in the Administration Guide.
- It is now possible to upload a certificate chain when configuring a remote syslog server to send system log messages to. This is handled both on the web interface and the REST API of SPS. For details, see "Configuring system logging" in the Administration Guide.
-
It is now possible to specify the base DN of LDAP subtrees for users and for groups separately. Specifying a sufficiently narrow base for the LDAP subtrees can speed up LDAP operations. For details, see "Managing One Identity Safeguard for Privileged Sessions (SPS) users from an LDAP database" in the Administration Guide and "Authenticating users to an LDAP server" in the Administration Guide.
-
Backup policies can be configured to run more than once a day.
-
You can now select which Server Message Block protocol version to use in the Archive and Backup policies if your server uses SMB/CIFS.
New features between SPS 5.1 and 5.11 - REST API
Sessions schema change in REST API
In order to better integrate SPS with One Identity Safeguard for Privileged Analytics, some architectural changes have been introduced. These changes have brought alterations for the sessions schema of the REST API. As a result, REST responses have changed in the case of the following endpoints:
-
/api/audit/sessions
-
/api/audit/sessions/<session-id>
-
/api/audit/sessions/<session-id>/content
-
/api/audit/sessions/<session-id>/alerts
-
/api/audit/sessions/<session-id>/events
-
Search, download and index sessions section restructure
The Search, download and index sessions section has been restructured and updated in the SPS REST API.
For more information, see "Search, download, and index sessions" in the REST API Reference Guide.
-
HTTP connection policies can now be configured through REST
The endpoint is now writable and allows create, update and delete.
For more information, see "HTTP connections" in the REST API Reference Guide.
-
The user now has the same privileges on the web UI and REST API
For the user to have full access over the SPS REST API, they must have the REST server privilege. The user privileges on the web UI and REST API are now synchronized. For example, if the user has the ICA Control / Connections privilege then they can access this page on the web UI and also the /api/configuration/ica/connections endpoint on the REST API.
For more information, see "Authenticate to the SPS REST API" in the REST API Reference Guide.
-
Changes to audit data access rules (ADAR) on REST
The endpoint can only be queried and is not writable. It does not allow create, update, or delete.
For more information, see "Audit data access rules" in the REST API Reference Guide.
-
When querying the /api/info endpoint, the response now contains the hash of the XML database (config_hash) running on a given SPS host.
For details, see "Retrieve basic firmware and host information" in the REST API Reference Guide.
-
It is now possible to change the settings for the RDP protocol using the /api/configuration/rdp/settings_policies/ endpoint.
For details, see "RDP settings policies" in the REST API Reference Guide.
-
The api/audit/sessions/stats endpoint provides statistics about recorded sessions. For details, see "Session statistics" in the REST API Reference Guide.
-
The api/audit/sessions/histogram endpoint provides a histogram about the recorded sessions. For details, see "Session histogram" in the REST API Reference Guide.
-
You can now enable One Identity Safeguard for Privileged Analytics using the REST API. For details, see "Enable One Identity Safeguard for Privileged Analytics" in the REST API Reference Guide.
-
The api/configuration/policies/analytics endpoint allows you to configure One Identity Safeguard for Privileged Analytics by adding and removing analytics policies. For details, see "Configure One Identity Safeguard for Privileged Analytics" in the REST API Reference Guide.
-
You can now read and update the license of SPS. For details, see "Manage the SPS license" in the REST API Reference Guide.
-
Changing the root and admin passwords of SPS has been documented. For details, see "Passwords stored on SPS" in the REST API Reference Guide.
-
Configuring RDP connection policies using the REST API has been documented. For details, see "RDP connection policies" in the REST API Reference Guide.
-
You can complete the Welcome Wizard using the API.
-
You can now upload the SPS license file using the API.
-
You can now change the password of local users, for example, the admin, and the root passwords.
-
New content endpoint: A new endpoint, /api/audit/sessions/<session-id>/content, has been added, which enables you to search in the contents of individual connections. For details, see "Searching in connection content" in the REST API Reference Guide.
-
Filter events: The filtering functionality previously only available under the api/audit/sessions endpoint is now added to the api/audit/sessions/<session-id>/events endpoint, too. This means that you can now search in the events of individual connections. For more information, see "Session events" in the REST API Reference Guide.
-
Backup and archive policies can now be configured using the REST API.
-
Health status information about the Central Management node and the cluster nodes is now available at the /api/cluster/status endpoint of the node.
-
You can now download audit trails from SPS using the REST API. For details, see "Download audit trails" in the REST API Reference Guide.
Enhancements
The following is a list of enhancements implemented in SPS 6.0.
| Enhancement | Issue ID |
|---|---|
|
Created PDF reports have been enhanced with the others label and others subsection, which indicate that more data is available but cannot be displayed in the report unless the search is further refined. |
|
|
The "Top X" predefined report subchapters now include the others label, which indicates that more data is available but cannot be displayed in the report unless the search is further refined. |
|

