Client-side failover
syslog-ng PE can detect if the remote server of a network destination becomes inaccessible, and start sending messages to a secondary server. You can configure multiple failover servers, so if the secondary server becomes inaccessible as well, syslog-ng PE switches to the third server in the list, and so on. If there are no more failover servers left, syslog-ng PE returns to the beginning of a list and attempts to connect to the primary server.
The primary server is the address you provided in the destination driver configuration and it has a special role. syslog-ng PE nominates this destination over the failover servers, and handles it as the primary address.
When syslog-ng PE starts up, it always connects to the primary server first. In the failover() option there is a possibility to customize the failover modes.
Depending on how you set the failback() option, syslog-ng PE behaves as follows:
-
round-robin mode: If failback() is not set, syslog-ng PE does not attempt to return to the primary server even if it becomes available. In case the failover server fails, syslog-ng PE attempts to connect the next failover server in the list in round-robin fashion. This is the default behavior in syslog-ng PE version 7.0.9 and earlier.
Example: round-robin mode
In the following example syslog-ng PE handles the logservers in round-robin fashion if the primary logserver becomes inaccessible (therefore failback() option is not set).
destination d_network {
network(
"primary-server.com"
port(601)
failover( servers("failover-server1", "failover-server2") )
);
};
-
failback mode: If failback() is set, syslog-ng PE attempts to return to the primary server.
After syslog-ng PE connects a secondary server during a failover, it sends a probe every tcp-probe-interval() seconds towards the primary server. If the primary logserver responds with a TCP ACK packet, the probe is successful. When the number of successful probes reaches the value set in the successful-probes-required() option, syslog-ng PE tries to connect the primary server using the last probe.
NOTE: syslog-ng PE always waits for the result of the last probe before sending the next message. So if one connection attempt takes longer than the configured interval, that is, it waits for connection time out, you may experience longer intervals between actual probes.
Example: failback mode
In the following example syslog-ng PE attempts to return to the primary logserver, as set in the failback() option: it will check if the server is accessible every tcp-probe-interval() seconds, and reconnect to the primary logserver after three successful connection attempts.
destination d_network_2 {
network(
"primary-server.com"
port(601)
failover(
servers("failover-server1", "failover-server2")
failback(
successful-probes-required()
tcp-probe-interval()
)
)
);
};
If syslog-ng PE is restarted, it attempts to connect the primary server.
If syslog-ng PE uses TLS-encryption to communicate with the remote server, syslog-ng PE checks the certificate of the failover server as well. The certificates of the failover servers should match their domain names or IP addresses — for details, see Encrypting log messages with TLS. Note that when mutual authentication is used, the syslog-ng PE client sends the same certificate to every server.
The primary server and the failover servers must be accessible with the same communication method: it is not possible to use different destination drivers or options for the different servers.
NOTE: Client-side failover works only for TCP-based connections (including TLS-encrypted connections), that is, the syslog() and network() destination drivers (excluding UDP transport).
Client-side failover is not supported in the sql() driver, even though it may use a TCP connection to access a remote database.
For details on configuring failover servers, see network() destination options and syslog() destination options.
Routing messages: log paths, flags, and filters
Routing messages: log paths, flags, and filters
Table 11: Log statement flags
| catchall |
This flag means that the source of the message is ignored, only the filters of the log path are taken into account when matching messages. A log statement using the catchall flag processes every message that arrives to any of the defined sources. |
| drop-unmatched |
This flag means that the message is dropped along a log path when it does not match a filter or is discarded by a parser. Without using the drop-unmatched flag, syslog-ng PE would continue to process the message along alternative paths. |
| fallback |
This flag makes a log statement 'fallback'. Fallback log statements process messages that were not processed by other, 'non-fallback' log statements.
Processed means that every filter of a log path matched the message. Note that in case of embedded log paths, the message is considered to be processed if it matches the filters of the outer log path, even if it does not match the filters of the embedded log path. For details, see Example: Using log path flags. |
| final |
This flag means that the processing of log messages processed by the log statement ends here, other log statements appearing later in the configuration file will not process the messages processed by the log statement labeled as 'final'. Note that this does not necessarily mean that matching messages will be stored only once, as there can be matching log statements processed before the current one (syslog-ng PE evaluates log statements in the order they appear in the configuration file).
Processed means that every filter of a log path matched the message. Note that in case of embedded log paths, the message is considered to be processed if it matches the filters of the outer log path, even if it does not match the filters of the embedded log path. For details, see Example: Using log path flags. |
| flow-control |
Enables flow-control to the log path, meaning that syslog-ng will stop reading messages from the sources of this log statement if the destinations are not able to process the messages at the required speed. If disabled, syslog-ng will drop messages if the destination queues are full. If enabled, syslog-ng will only drop messages if the destination queues/window sizes are improperly sized. For details, see Managing incoming and outgoing messages with flow-control. |
Log paths
Log paths determine what happens with the incoming log messages. Messages coming from the sources listed in the log statement and matching all the filters are sent to the listed destinations.
To define a log path, add a log statement to the syslog-ng configuration file using the following syntax:
log {
source(s1); source(s2); ...
optional_element(filter1|parser1|rewrite1);
optional_element(filter2|parser2|rewrite2);
...
destination(d1); destination(d2); ...
flags(flag1[, flag2...]);
};
|

|
Caution:
Log statements are processed in the order they appear in the configuration file, thus the order of log paths may influence what happens to a message, especially when using filters and log flags. |
NOTE: The order of filters, rewriting rules, and parsers in the log statement is important, as they are processed sequentially.
Example: A simple log statement
The following log statement sends all messages arriving to the localhost to a remote server.
source s_localhost {
network(
ip(127.0.0.1)
port(1999)
);
};
destination d_tcp {
network(
"10.1.2.3"
port(1999)
localport(999)
);
};
log {
source(s_localhost);
destination(d_tcp);
};
All matching log statements are processed by default, and the messages are sent to every matching destination by default. So a single log message might be sent to the same destination several times, provided the destination is listed in several log statements, and it can be also sent to several different destinations.
This default behavior can be changed using the flags() parameter. Flags apply to individual log paths, they are not global options. For details and examples on the available flags, see Log path flags. The effect and use of the flow-control flag is detailed in Managing incoming and outgoing messages with flow-control.
Embedded log statements
Starting from version 3.0, syslog-ng can handle embedded log statements (also called log pipes). Embedded log statements are useful for creating complex, multi-level log paths with several destinations and use filters, parsers, and rewrite rules.
For example, if you want to filter your incoming messages based on the facility parameter, and then use further filters to send messages arriving from different hosts to different destinations, you would use embedded log statements.
Figure 30: Embedded log statement
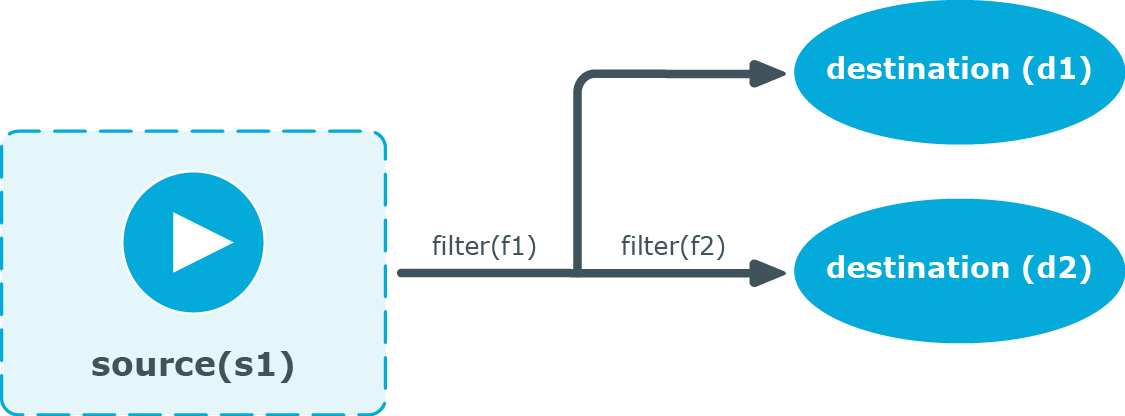
Embedded log statements include sources — and usually filters, parsers, rewrite rules, or destinations — and other log statements that can include filters, parsers, rewrite rules, and destinations. The following rules apply to embedded log statements:
-
Only the beginning (also called top-level) log statement can include sources.
-
Embedded log statements can include multiple log statements on the same level (that is, a top-level log statement can include two or more log statements).
-
Embedded log statements can include several levels of log statements (that is, a top-level log statement can include a log statement that includes another log statement, and so on).
-
After an embedded log statement, you can write either another log statement, or the flags() option of the original log statement. You cannot use filters or other configuration objects. This also means that flags (except for the flow-control flag) apply to the entire log statement, you cannot use them only for the embedded log statement.
-
Embedded log statements that are on the same level receive the same messages from the higher-level log statement. For example, if the top-level log statement includes a filter, the lower-level log statements receive only the messages that pass the filter.
Figure 31: Embedded log statements
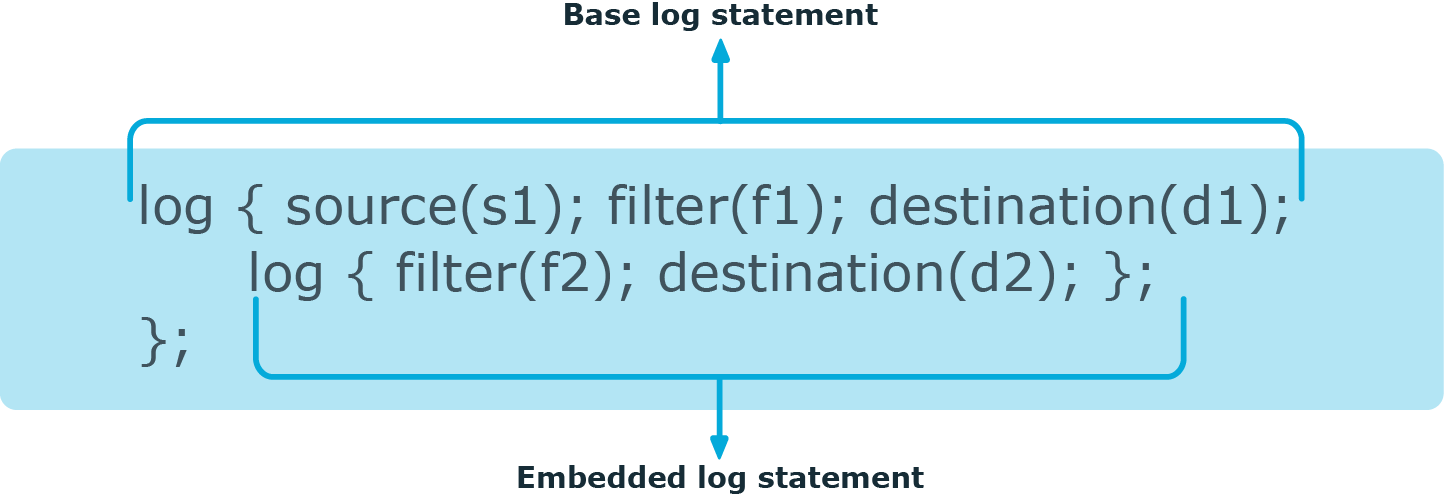
Embedded log filters can be used to optimize the processing of log messages, for example, to re-use the results of filtering and rewriting operations.



