The configuration of syslog-ng Store Box (SSB) can be exported (for manual archiving, or to migrate it to another SSB unit) from the Basic Settings > System page. Use the respective action buttons to perform the desired operation.
Figure 89: Basic Settings > System — Exporting the SSB configuration
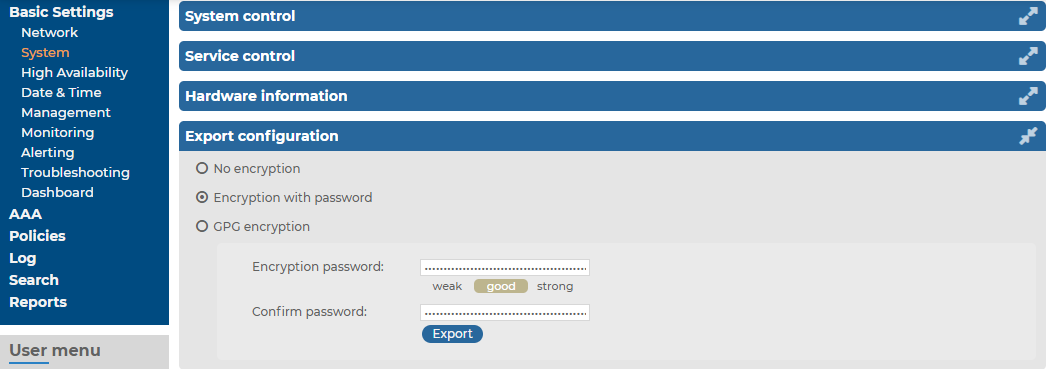
To export the configuration of SSB
-
Navigate to Basic Settings > System > Export configuration.
-
Select how to encrypt the configuration:
-
To export the configuration file without encryption, select No encryption.
|

|
Caution:
Exporting the SSB configuration without encyption is not recommended, as it contains sensitive information such as password hashes and private keys. |
-
To encrypt the configuration file with a simple password, select Encrypt with password and enter the password into the Encryption password and Confirm password fields.
NOTE: The syslog-ng Store Box (SSB) appliance accepts passwords that are not longer than 150 characters. The following special characters can be used:
! " # $ % & ' ( ) * + , - . / : ; < > = ? @ [ ] ^ - ` { | } |
-
To encrypt the configuration file with GPG, select GPG encryption. Note that this option uses the same GPG key that is used to encrypt automatic system backups, and is only available if you have uploaded the public part of a GPG key to SSB at Basic Settings > Management > System backup. For details, see Encrypting configuration backups with GPG.
-
Click Export.
NOTE: The exported file is a gzip-compressed archive. On Windows platforms, it can be decompressed with common archive managers such as the free 7-Zip tool.
The name of the exported file is <hostname_of_SSB>-YYYMMDDTHHMM.config. The -encrypted or -gpg suffix is added for password-encrypted and GPG-encrypted files, respectively.
The configuration of syslog-ng Store Box (SSB) can be imported from the Basic Settings > System page. Use the respective action buttons to perform the desired operation.
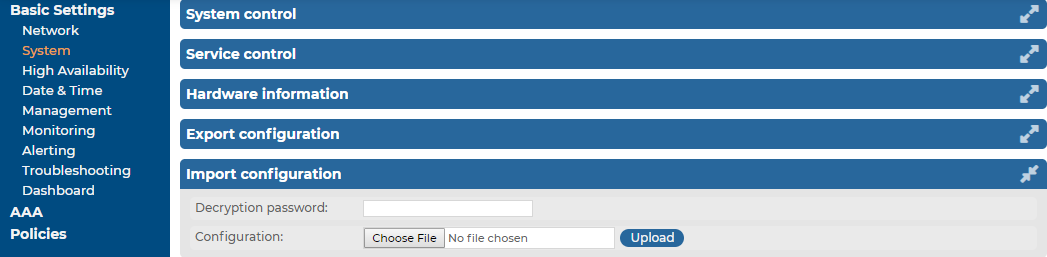
Figure 90: Basic Settings > System — Importing the SSB configuration
|

|
Caution:
It is possible to import a configuration exported from SSB 2.0 or 3.0 into SSB 7.0.4 LTS, but it is not possible to restore an 1.1 or 1.0 backup into 7.0.4 LTS. |
To import the configuration of SSB
-
Navigate to Basic Settings > System > Import configuration.
-
Click Choose File and select the configuration file to import.
-
Enter the password into the Decryption password field and click Upload.
NOTE: The syslog-ng Store Box (SSB) appliance accepts passwords that are not longer than 150 characters. The following special characters can be used:
! " # $ % & ' ( ) * + , - . / : ; < > = ? @ [ ] ^ - ` { | } |
|

|
Caution:
When importing an older configuration, it is possible that there are logspaces on SSB that were created after the backing up of the old configuration. In such case, the new logspaces are not lost, but are deactivated and not configured. To make them accessible again, you have to:
-
Navigate to Log > Logspaces and configure the logspace. Filling the Access Control field is especially important, otherwise the messages stored in the logspace will not be available from the Search > Logspaces interface.
-
Adjust your log path settings on the Log > Paths page. Here you have to re-create the log path that was sending messages to the logspace. |
This section describes how to use the console menu of syslog-ng Store Box (SSB), how to enable remote SSH access to SSB, and how to change the root password from the web interface.
Connecting to the syslog-ng Store Box (SSB) locally or remotely using Secure Shell (SSH) allows you to access the console menu of SSB. The console menu provides access to the most basic configuration and management settings of SSB. It is mainly used for troubleshooting purposes, the primary interface of SSB is the web interface.
NOTE: Detailed host information is displayed in the shell prompt:
The format of the bash prompt is:
(firmware_type/HA_node/hostname)username@HA_node_name:current_working_directory#
For example:
(core/master/documentation-ssb)root@ssb1:/etc#
-
firmware_type is either boot or core
-
HA_node is either master or slave
-
hostname is the FQDN set on the GUI
-
username is always root
The console menu is accessible to the root user using the password set during completing the Welcome Wizard.
Figure 91: The console menu
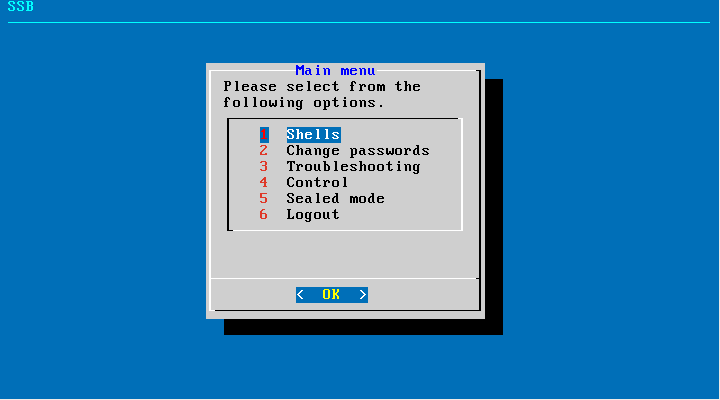
The console menu allows you to perform the following actions:
-
Change the passwords of the root and admin users.
-
Access the local core and boot shells. This is usually not recommended and only required in certain troubleshooting situations. In a high-availability cluster, you can also access the boot shell of the remote node.
-
Access the network-troubleshooting functions and display the available log files.
-
Reboot and shut down the system. In a high-availability cluster, you can also reboot or shutdown the remote node, or initiate a take over.
-
Enable and disable sealed mode. For more information, see Sealed mode.
-
Set the IP address of the HA interface.
NOTE: Note that logging in to the console menu automatically locks the SSB interface, meaning that users cannot access the web interface while the console menu is used. The console menu can be accessed only if there are no users accessing the web interface. The connection of web-interface users can be terminated to force access to the console menu.
On the secondary node of a high-availability cluster, the console menu is limited to troubleshooting and diagnostic functions (for example, you cannot change passwords or manage sealed mode).




