Inband destination selection in RDP connections
To use inband destination selection with RDP connections, it is recommended to use One Identity Safeguard for Privileged Sessions (SPS) as a Remote Desktop Gateway (or RD Gateway). For details, see Using One Identity Safeguard for Privileged Sessions (SPS) as a Remote Desktop Gateway.
To use inband destination selection with RDP connections without using One Identity Safeguard for Privileged Sessions (SPS) as a Remote Desktop Gateway (or RD Gateway), you must use SSL-encrypted RDP connections (see Enabling TLS-encryption for RDP connections).
Configure your RDP clients so SPS can record the username of client uses in the connection. If you do not configure these settings on the clients, SPS will automatically display a login screen for the users to enter their usernames and passwords.
Navigate to Local Group Policy Editor > Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Connection Client and enable the Prompt for credentials on the client computer option in the clients. For details, see the Microsoft Documentation.
Also, your users have the option to encode the address of the destination server in their username, in the username field of their client application. Note that SPS automatically displays a login screen if it cannot determine the username used in the connection, or you have not encoded a destination server in the username field. You can specify the destination address in the login screen when prompted.
When encoding the address of the destination server in the username, there are a few points to keep in mind. Since most RDP client applications limit which special characters can be used in usernames, this is not always intuitive.
For the Microsoft Remote Desktop application (mstsc) and the login screen that SPS displays, note the following points:
-
Use the % character to separate the fields, for example: username%my-targetserver
-
Do not use the @ character.
-
To specify the port number of the server (if it does not use the default port), use the caret ^ character, for example: username%my-targetserver^6464
-
To specify an IPv6 address, replace the colons with carets, and enclose the address in parentheses. For example, to target the ::1 IP address, use username%(^^1). To target port 6464 of the same server, use username%(^^1)^6464.
Usernames in RDP connections
When processing RDP connections, One Identity Safeguard for Privileged Sessions (SPS) attempts to extract the username from the connection. For example, you need the username to:
-
Use gateway authentication for the connection. For details on gateway authentication, see "Configuring gateway authentication" in the Administration Guide.
-
Use usermapping policies. In this case, SPS compares the username on the server with the username on the gateway. For details on usermapping policies and gateway authentication, see "Configuring usermapping policies" in the Administration Guide and "Configuring gateway authentication" in the Administration Guide, respectively.
NOTE: In certain cases, SPS receives an empty username from the server, and the connection will be denied by the usermapping policy unless a policy is set for the connection that allows every user for the given group. To add such a policy, specify * in the Username on the server field of the usermapping policy. For a list of cases when SPS receives empty username, see Windows settings that interfere with username extraction.
-
Search or filter connections by the username on the SPS search interface, or create automatic statistics based on the username.
-
Find the connection of the user on the Four Eyes and Active Connections pages.
-
Usernames are also essential if you want to use One Identity Safeguard for Privileged Analytics. If you are interested in One Identity Safeguard for Privileged Analytics, contact our Sales Team, or your One Identity representative.
SPS can record the username automatically if the RDP connection is using Network Level Authentication (CredSSP), and usually in other scenarios as well. If SPS cannot automatically extract the username, it displays the following login screen, which allows you to paste text-based clipboard contents. Note that SPS can display this login screen only in TLS-encrypted connections.
The known scenarios that interfere with RDP usernames are listed in Windows settings that interfere with username extraction.
NOTE: SPS supports usernames both in UPN (such as username@domain) and down-level logon name (such as DOMAIN\username) formats.
Figure 213: Server-side login in RDP
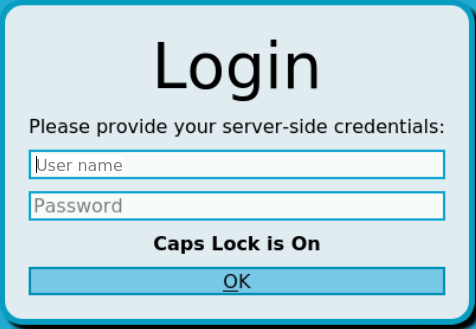
To ensure that your users can access the target servers only when their username is recorded, you can configure SPS to terminate RDP connections if it cannot reliably extract the username. To terminate such connections, clear the RDP Control > Settings > Permit unreliable usernames option.
Windows settings that interfere with username extraction
The following settings on the Windows client or server can prevent SPS from correctly extracting the username from the RDP connection. As a result, the username is not visible on the Search, Four Eyes and Active Connections pages.
-
The DontDisplayLastUserName option is enabled on the server. The DontDisplayLastUserName security setting of Windows servers specifies whether the username from the last successful login is displayed on the login screen as a default for the next login. To disable the DontDisplayLastUserName security setting, do one of the following.
-
There is no server-side authentication. To avoid this problem, ensure that your server requires authentication from the users.
-
If the server is Windows 2003 Server or Windows XP and the Allow to save credentials or Remember my credentials options are enabled in the Remote Desktop client application. In this case, disable these options on the client, and delete any credentials that have already been saved on the client.
Saving login credentials for RDP on Windows
You can use automatic RDP login on Windows, but the stored credentials are not trusted by default, and you have to enter the password for each connection. Create the following local policies on the client to allow delegating saved credentials:
-
Start the Group Policy Editor: run gpedit.msc.
-
Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > System > Credentials Delegation.
-
Open the Allow Delegating Saved Credentials with NTLM-only Server Authentication policy.
-
Click Show and enter TERMSRV/*.
-
Click Apply.
-
Open the Allow Delegating Saved Credentials policy.
-
Click Show and enter TERMSRV/*.
-
Click Apply.
-
Open the Allow Delegating Default Credentials with NTLM-only Server Authentication policy.
-
Click Show and enter TERMSRV/*.
-
Click Apply.
-
Open the Allow Delegating Default Credentials policy.
-
Click Show and enter TERMSRV/*.
-
Click Apply.
-
Verify that the Deny Delegating Saved Credentials policy does not contain TERMSRV/* in the list.
-
Close the Group Policy Editor.
-
From the command line, issue the gpupdate /force command.
Configuring RemoteApps
Overview
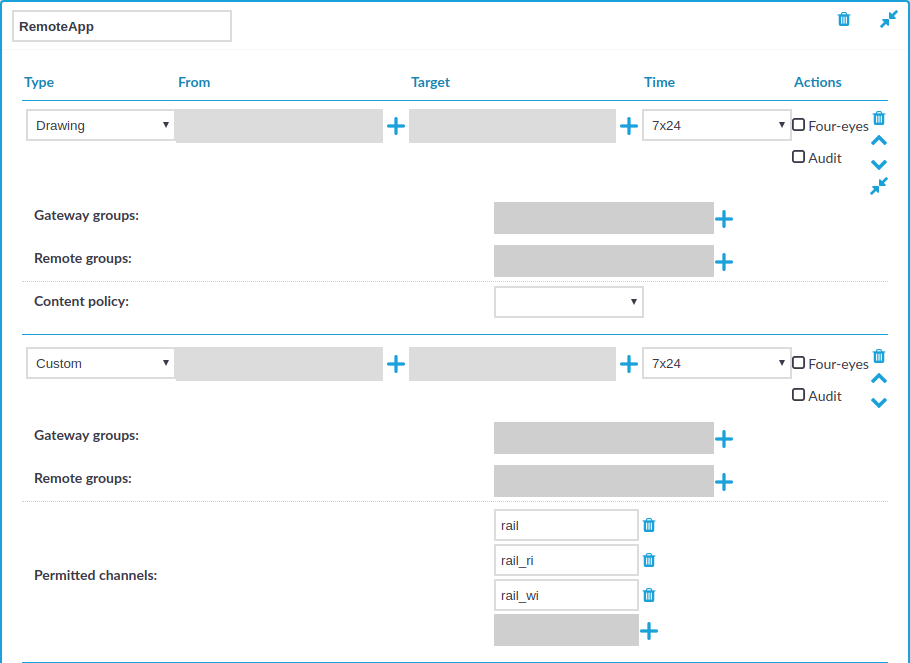
RemoteApps use RDP channels that are denied by default. When configuring RDP connections for RemoteApps on One Identity Safeguard for Privileged Sessions (SPS), create a custom channel policy which enables the following channels:
-
Drawing
-
rail
-
rail_ri
-
rail_wi
Figure 214: RDP Control > Channel Policies — Configuring the required channels for RemoteApps
Prerequisites
-
You must disable the Use advanced RemoteFX graphics for RemoteApp group policy on the RDP server.
The policy is available at Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Remote Session Environment > Use advanced RemoteFX graphics for RemoteApp.
-
You must have the Remote Desktop (RD) Licensing role installed.
To configure RemoteApps
-
Navigate to RDP Control > Channel Policies.
-
Click  to create a new channel policy.
to create a new channel policy.
-
Enter the name for the channel policy.
-
Choose Drawing as the channel type.
-
Click  to add an additional channel type.
to add an additional channel type.
-
Choose Custom as the second channel type.
-
In Permitted channels, click  to add the following channels:
to add the following channels:
(You have to click  for each channel.)
for each channel.)
-
Click  to save the channel policy.
to save the channel policy.
-
You have created a channel policy for RemoteApps.
When you configure a connection that uses RemoteApps in RDP Control > Connections, select this channel policy as the Channel policy of the connection.



 to create a new channel policy.
to create a new channel policy. to save the channel policy.
to save the channel policy.