The indexers that run on an external host send log messages into the standard syslog of the external host. These log messages are not visible on One Identity Safeguard for Privileged Sessions (SPS). If a problem occurs, check the logs of SPS and the external indexer to find out which component on which host causes the problem. If the problem is on the external indexer host, verify that the required decryption keys are available on the host, then restart the indexer service using the following command.
-
On Red Hat or CentOS 6.5:
service external-indexer restart
-
On Red Hat or CentOS 7:
systemctl restart external-indexer.service
If the problem persists, contact our Support Team. You can increase the log level of the indexer processes from the configuration file.
The status of audit-trail processing is displayed on the Indexer page of the Main Menu.
Elements of the Indexer page
The following list describes the elements of the Indexer page and their functions.
-
Worker status: displays various data about the worker groups.
-
Indexer IP address: displays the IP address of the indexer (either the indexer running on One Identity Safeguard for Privileged Sessions (SPS) or an external indexer). It may display the following:
- 127.0.0.1: indicated the indexer running on SPS.
- An IP address other than127.0.0.1: indicates an external indexer.
-
Capabilities: the type of job(s) this worker will perform.
-
Capacity: the available and total Capacity (Maximum parallel audit trails to process) of the indexer, and also the number of active processes that are Indexing an audit trail, or Generating video or Generating screenshot.
-
Processing: audit trails that are currently being processed per connection policy.
-
Waiting for processing: audit trails waiting to be processed.
When you see audit trails in the Indexing column, that could mean any of the following:
-
The maximal queue size is 1000. If there are many trails waiting to be indexed, SPS will keep lots of trails in the queue.
-
The worker with the appropriate key for decryption is not available at the moment, and other workers do not have the required key.
-
There are no workers available that have the required capability.
-
Optical Character Recognition (OCR) engine status: It allows you to check and report if there were indexed audit trails where the OCR engine failed. Perform a search on the Search interface using the provided link and if the search returns any results, contact our Support Team to submit a report.
Figure 261: Indexer > Indexer status — Monitoring the status of the indexers
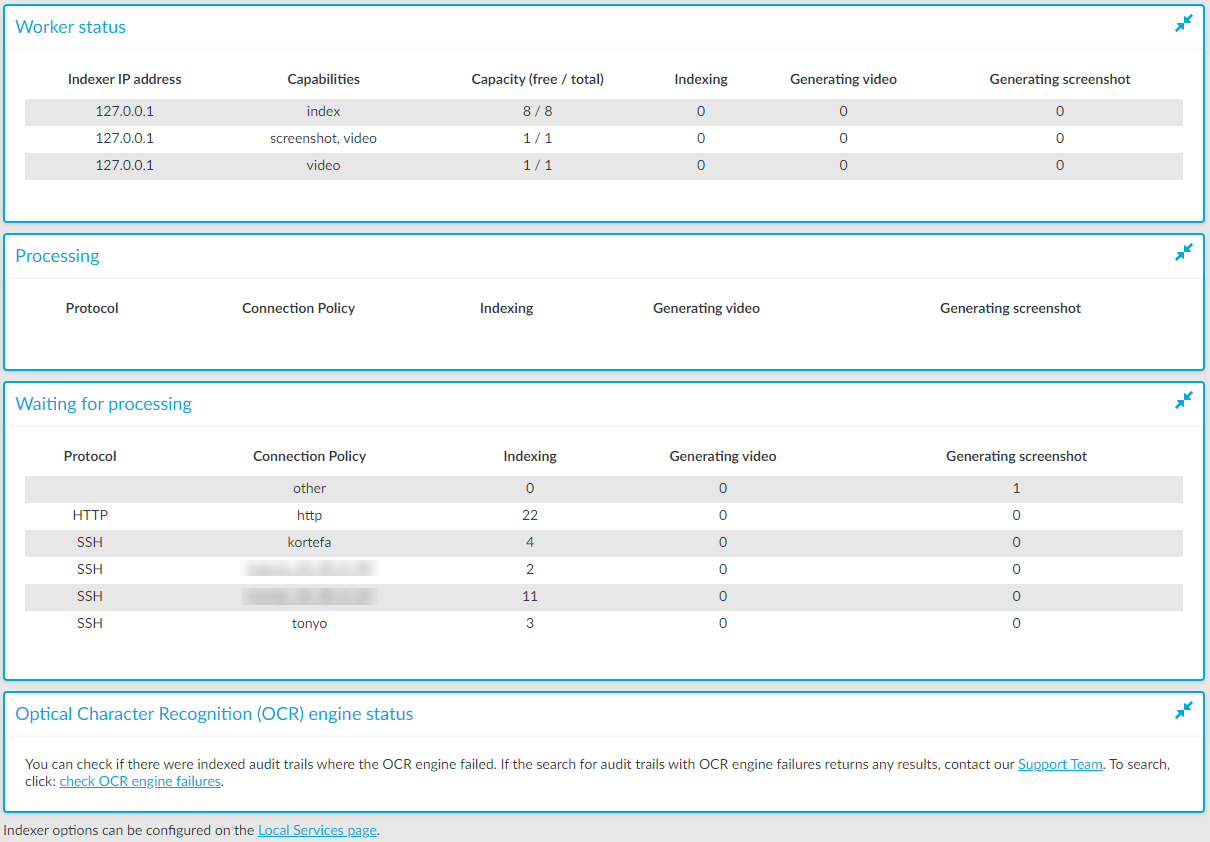
To automatically refresh the Indexer Status page every 5 seconds, select Auto refresh. To refresh the page immediately, click Refresh now.
This section describes the configuration format and options of the HTTP indexer (that is, how and which fields of the HTTP audit trails are indexed). For details on how to customize HTTP indexing, see Customizing the indexing of HTTP traffic.
NOTE: If you want to index HTTP POST messages, include the "application/x-www-form-urlencoded" Content-Type in the General > WhiteList list. The indexer will decode URL encoding (percentage encoding), and create key=value pairs from the form fields and their values. Note that in the values, the indexer will replace whitespace with the underscore (_) character. To avoid indexing sensitive information (for example, passwords from login forms), use the Form > Blacklist option.
General
Type: Top level item
Description: Determines which HTTP Content-Types are indexed. An HTTP message is indexed only if its Content-Type is listed in Whitelist and is not listed in Blacklist.
For example:
"General": {
"Whitelist": ["text/.*", ".*json.*", "multipart/.*", "application/x-www-form-urlencoded"],
"Blacklist": ["text/css", "application/javascript", "text/xslt", ".*xml.*"]
},
General (Whitelist)
Type: list
Description: The list of HTTP Content-Types to index. Every entry of the list is treated as a regular expression.
For example:
"Whitelist": ["text/.*", ".*json.*", "multipart/.*", "application/x-www-form-urlencoded"],
General (Blacklist)
Type: list
Description: The list of HTTP Content-Types that are not indexed. Every entry of the list is treated as a regular expression.
For example:
"Blacklist": ["text/css", "application/javascript", "text/xslt", ".*xml.*"]
Form
Type: Top level item
Description: Determines which fields are indexed in HTTP POST messages.
For example:
"Form": {
"Blacklist": ["password", "pass"]
},
NOTE: If you want to index HTTP POST messages, include the "application/x-www-form-urlencoded" Content-Type in the General > WhiteList list. The indexer will decode URL encoding (percentage encoding), and create key=value pairs from the form fields and their values. Note that in the values, the indexer will replace whitespace with the underscore (_) character. To avoid indexing sensitive information (for example, passwords from login forms), use the Form > Blacklist option.
Form (Blacklist)
Type: list
Description: The list of fields that are not indexed in HTTP POST messages (for example, when submitting forms, such as login forms). Every entry of the list is treated as a regular expression.
For example:
"Blacklist": ["password", "pass"]
Html
Type: Top level item
Description: Include this section in the configuration to process text/html messages. HTML tags are stripped from the text, and only their content is indexed (for example, <html><title>Title</title></html> becomes Title).
For example:
"Html": {
"Attributes": ["href", "name", "value", "title", "id", "src"],
"StrippedTags": ["script", "object", "style", "noscript", "embed", "video", "audio", "canvas", "svg"]
}
Html (Attributes)
Type: list
Description: The list of HTML attributes that extracted as key=value pairs and indexed. Note that in the values, the indexer will replace whitespace with the underscore (_) character, and decode URL encoding. For example:
"Attributes": ["href", "name", "value", "title", "id", "src"],
Note that for the content attribute of the meta name="description", meta name="keywords", meta name="author" and meta name="application-name" is always indexed.
For example, if an audit trail contains the following HTML:
<head>
<meta name="description" content="Web page description">
<meta name="keywords" content="HTML,CSS,XML,JavaScript">
<meta name="author" content="OI SA">
<meta charset="UTF-8">
</head>
Then the index will contain the following text:
description=Web_page_description keywords=HTML,CSS,XML,JavaScript author=OI_SA
Html (StrippedTags)
Type: list
Description: The list of HTML tags that are not indexed.
For example:
"StrippedTags": ["script", "object", "style", "noscript", "embed", "video", "audio", "canvas", "svg"]

