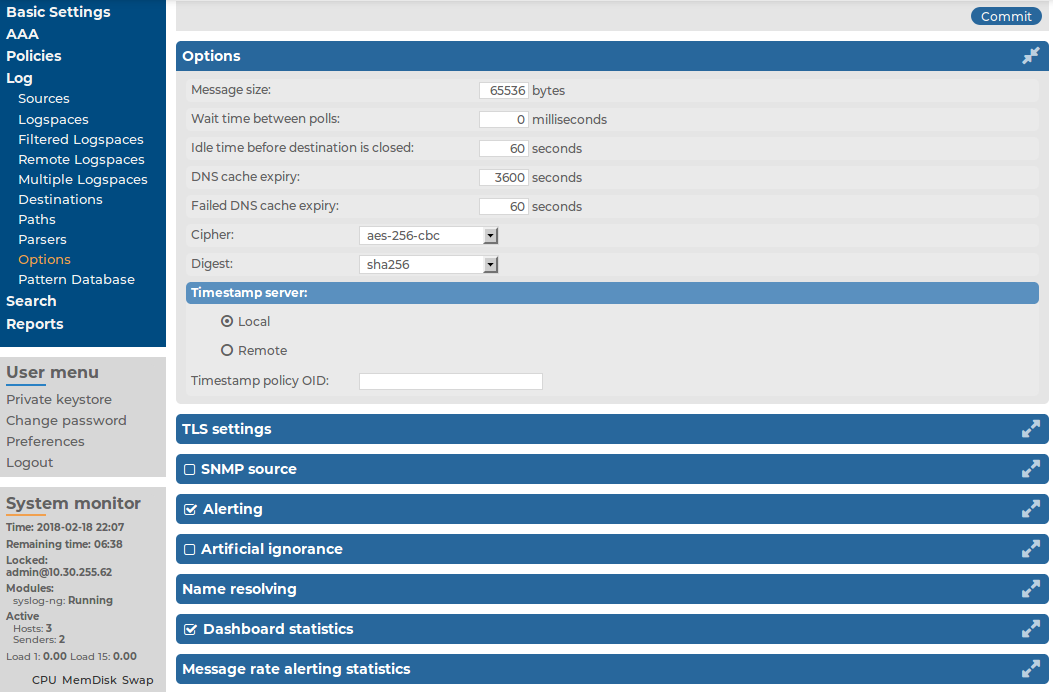
To configure the general options of the syslog-ng server running on the syslog-ng Store Box(SSB) appliance, navigate to Log > Options. The following options are available (note that options related to name resolution are discussed in Using name resolution on SSB):
Figure 199: Log > Options — Configuring syslog-ng options
-
Message size: Specifies the maximum length of incoming log messages in bytes. This option corresponds to the log-msg-size() parameter of syslog-ng. The maximum value of this parameter is 1000000 (1 MB).
NOTE: To be able to edit the Message size, you must have write/perform permission for the Basic Settings > System page. For details on how to assign user rights, see Managing user rights and usergroups.
-
Wait time between polls: The time to wait in milliseconds before checking if new messages have arrived to a source. This option corresponds to the time-sleep() parameter of syslog-ng.
-
Idle time before destination is closed: The time to wait in seconds before an idle destination file is closed. This option corresponds to the time-reap() parameter of syslog-ng.
-
Cipher: Select the cipher method used to encrypt the logstore. The following cipher methods are available: aes-128-cbc, aes-128-cfb, aes-128-cfb1, aes-128-cfb8, aes-128-ecb, aes-128-ofb, aes-192-cbc, aes-192-cfb, aes-192-cfb1, aes-192-cfb8, aes-192-ecb, aes-192-ofb, aes-256-cbc, aes-256-cfb, aes-256-cfb1, aes-256-cfb8, aes-256-ecb, aes-256-ofb, aes128, aes192, aes256, bf, bf-cbc, bf-cfb, bf-ecb, bf-ofb, cast5-cbc, cast5-cfb, des-cbc, des-cfb, des-cfb1, des-cfb8, des-ecb, des-ede, des-ede-cbc, des-ede-cfb, des-ede-ofb, des-ede3, des-ede3-cbc, des-ede3-cfb, des-ede3-ofb, des-ofb, desx-cbc, rc2-40-cbc, rc2-64-cbc, rc2-cbc, rc2-cfb, rc2-ecb, rc2-ofb, rc4, and rc4-40.
By default, SSB uses the aes-256-cbc method.
-
Digest: Select the digest method to use. The following digest methods are available: MD4, MD5, SHA-1, RIPEMD-160, SHA-224, SHA-256, SHA-384, and SHA-512.
By default, SSB uses the SHA-256 method.
Caution: The size of the digest hash must be equal to or larger than the key size of the cipher method. For example, to use the aes-256-cbc cipher method, the digest method must be at least SHA-256.


 icon in the TLS certificate field to upload the certificate.
icon in the TLS certificate field to upload the certificate.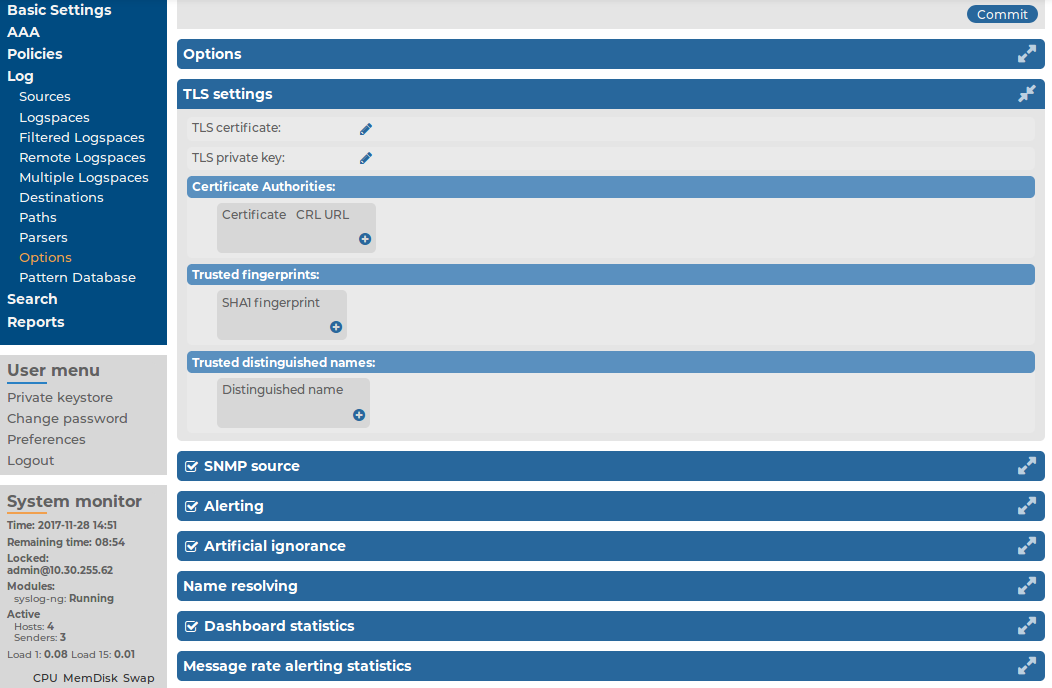
 in the Certificate Authorities field, then click
in the Certificate Authorities field, then click