Deployment of the Password Manager Self-Service and Helpdesk Sites on Standalone Servers
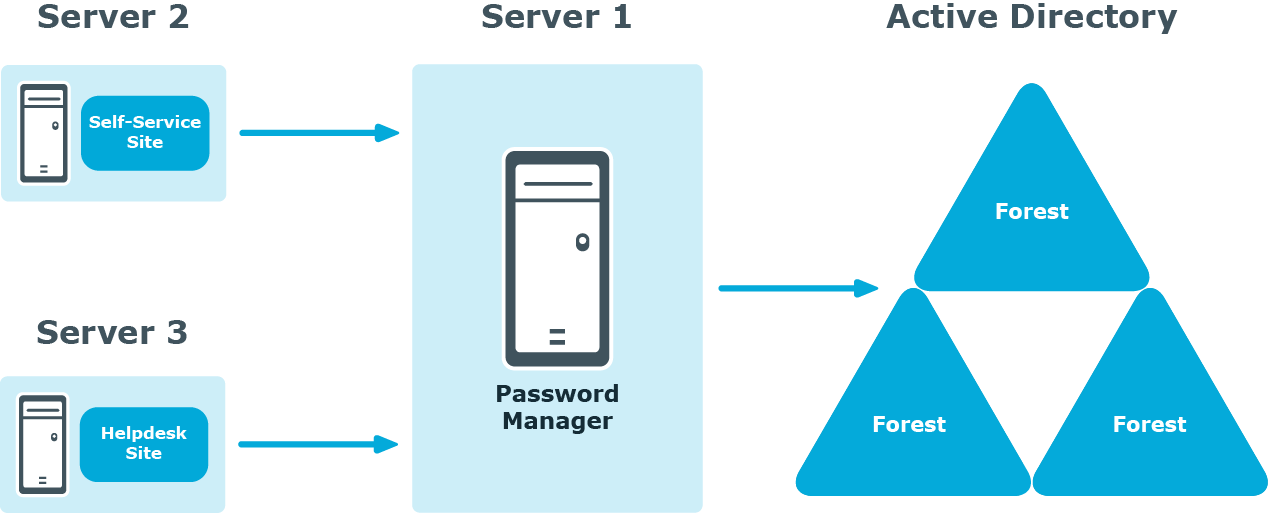
In this scenario, you install the Password Manager Self-Service Site, Helpdesk Site, or both on a standalone server.
NOTE:The Administration Site cannot be installed separately from the Password Manager Service.
You can use this scenario to deploy Password Manager in an environment with a perimeter network. Installation of the Password Manager Self-Service Site in the perimeter network enhances the security of your environment while preventing access to your internal network.
When deploying Password Manager in an environment with the perimeter network, it is recommended to do a full installation of Password Manager in the internal corporate network, and then install the Self-Service Site in the perimeter network.
When you use this installation scenario, only one port should be open in the firewall between the corporate network and the perimeter network (by default, port number 8081 for the Password Manager Self-Service Site).
Realm deployment
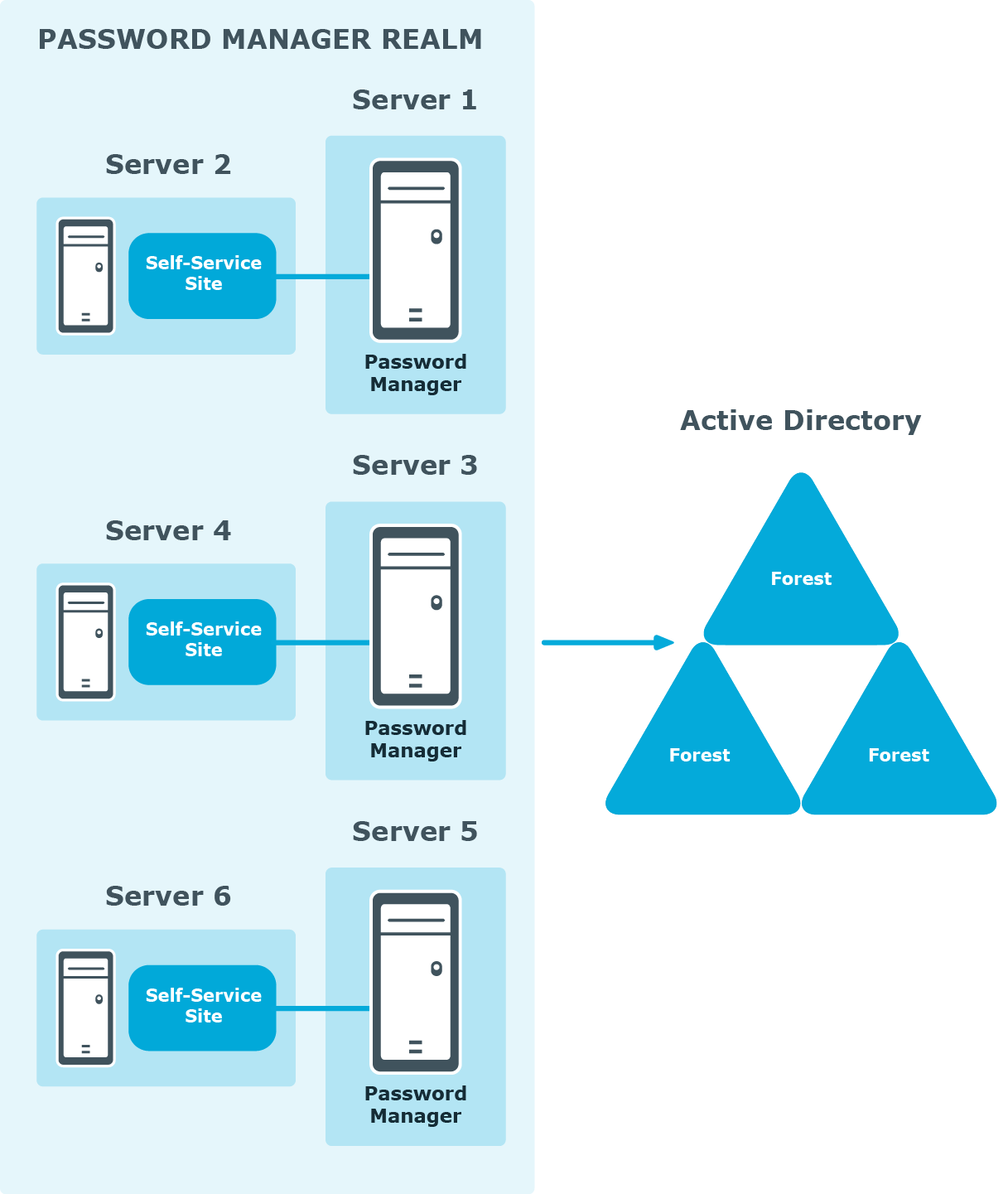
In this scenario, you install several Password Manager Services on separate servers. If all the instances of Password Manager share the same configuration (management policies, general settings, password policies, encryption algorithm, encryption key length, hashing algorithm, attribute for storing configuration data, and realm affinity ID), they are referred to as a realm.
The realm provides for high availability of the service, load balancing, and fault tolerance.
For Password Manager Service instances installed on separate servers, you can use a load balancer to enhance service availability.
To create the Password Manager realm, you need to create replicas of an existing instance by exporting settings from this instance and importing the settings to a new instance.
For more information on how to create realms, see Import/Export Configuration Settings.
Multiple Realm Deployment
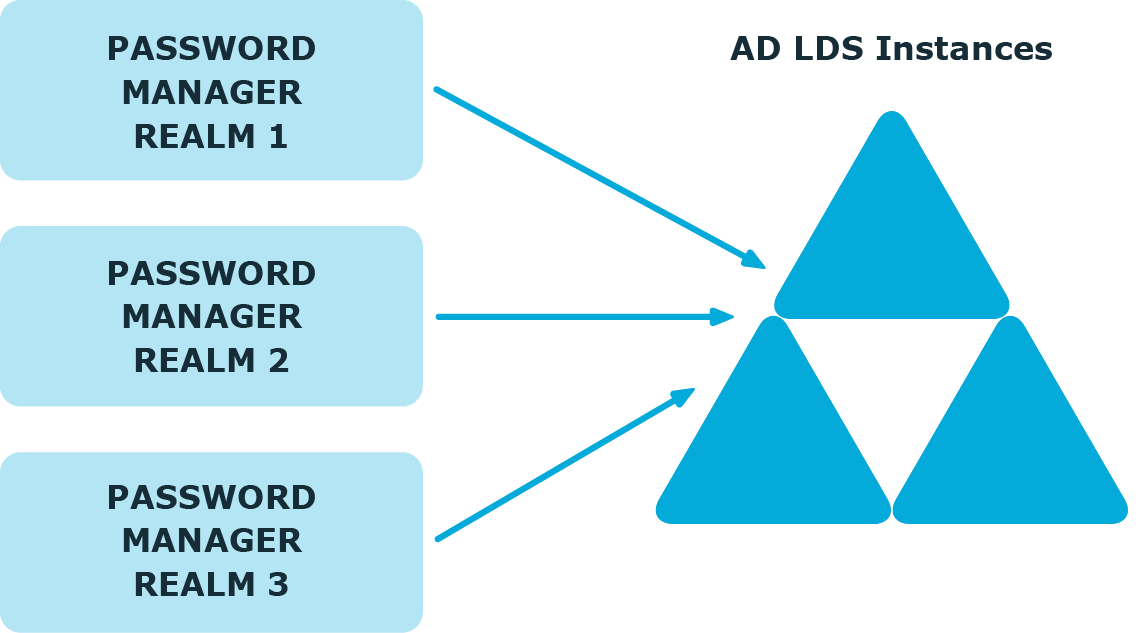
In this scenario, you deploy several Password Manager realms in your environment. You can use this scenario in complex environment, when several Password Manager configurations are required.
For example, a service provider can deploy two Password Manager realms, one realm to service company A, and the other - company B.
You can also use this scenario for a test deployment of Password Manager. In this case, the first realm is a production deployment of Password Manager, and the second realm can be used for testing purposes.
Password Manager in a perimeter network
When deploying Password Manager in a perimeter network (also known as a DMZ), One Identity recommends to install the Password Manager Service and the sites in a corporate network at first (that is,use the Full installation option in the Password Manager setup), and then install only the Self-Service and Helpdesk sites in the perimeter network.
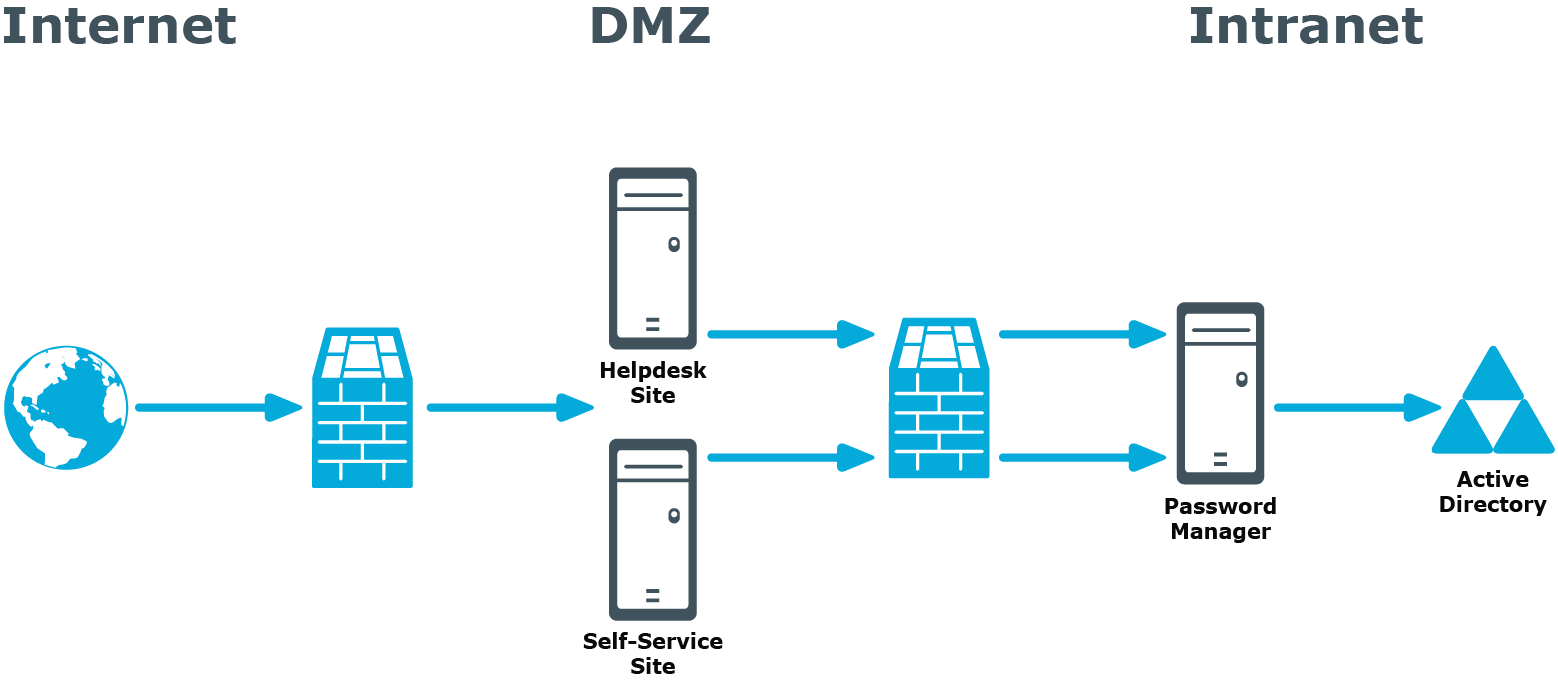
When you use this installation scenario, only one port should be open in the firewall between the corporate network and the perimeter network (by default, port number 8081 is used).
For more information on installing the Self-Service and Helpdesk Site separately from the Password Manager Service, see Installing Password Manager Self-Service, and Helpdesk Sites on a Standalone Server.




