Signing in to a Windows-based computer
To sign in to a Windows-based computer protected by GrIDsure
- At the Windows sign-in screen, enter your user name and password.
Make sure you leave the Passcode text box empty.
- Press ENTER.
If you are using the GrIDsure token for the first time, you may be prompted to configure your GrIDsure Personal Identification Pattern (PIP). For more information, see How to configure and use your Personal Identification Pattern (PIP).
- When prompted, use the matrix of cells to type your PIP in the Use your GrIDsure PIP text box.
- Press ENTER to sign in to Windows.
Authenticating on a Web site protected by GrIDsure
To authenticate on a Web site by using the GrIDsure token
- In your Web browser, enter the address of the Web site you want to access.
If the Web site is protected with the GrIDsure personal identification system, the following page opens:
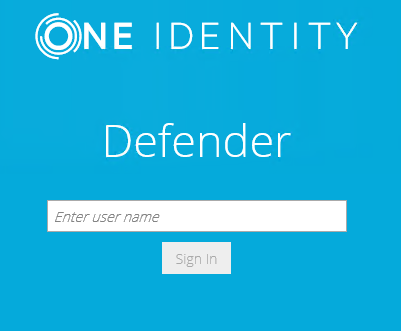
- Type your user name, and then click Sign In.
The page prompts you to enter your Windows password:
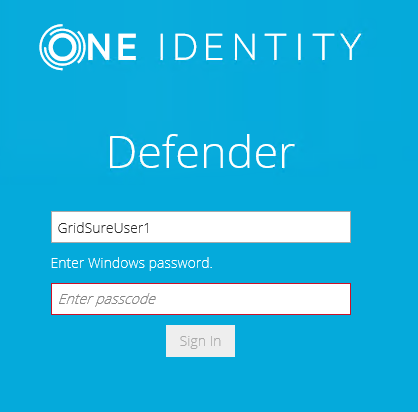
Note that the page that opens may look differently if you have two or more different types of Defender Soft Token assigned:

In this case, click the Use GrIDsure button.
- Type your Windows password, and then click Sign In.
If this is the first time you authenticate using the GrIDsure token, you may be prompted to configure your GrIDsure Personal Identification Pattern (PIP). For more information, see How to configure and use your Personal Identification Pattern (PIP).
- You are now prompted to authenticate using your GrIDsure PIP. Type the numbers located in the cells you chose when configuring your GrIDsure PIP:
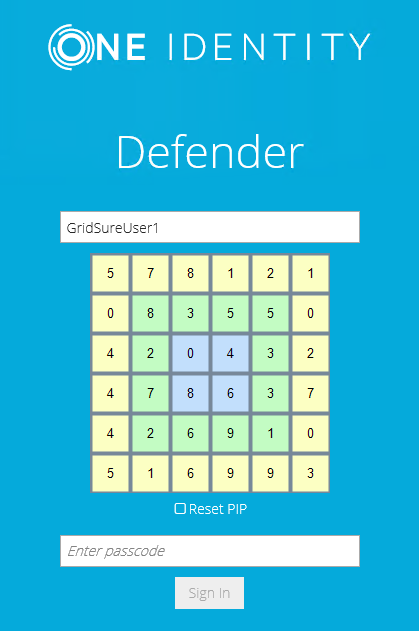
In the Enter passcode text box, type your PIP, and then click Sign In to access the protected Web site.
You can select the Reset PIP check box to reset your current PIP after you sign in.
How to configure and use your Personal Identification Pattern (PIP)
To authenticate with the GrIDsure token, you need to use a special code which is called the GrIDsure Personal Identification Pattern (PIP).
When you access a resource protected with the GrIDsure personal identification system for the first time, you are prompted to configure your PIP. In this case, a matrix of cells similar to the following displays:
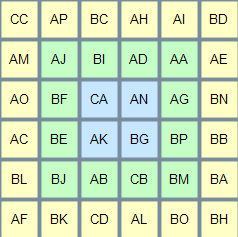
In this matrix, choose the cells you want to use for authentication, and then, in the Configure your GrIDsure PIP text box, type the codes contained in the cells you have chosen. Do not leave blank spaces between the codes.
For example, if you choose the first four cells in the first row of the matrix above, in the Configure your GrIDsure PIP text box, type CCAPBCAH (without spaces), and then press ENTER or click the Login button.
From now on, each time you authenticate with your GrIDsure token, you must use the codes displayed in the matrix cells you have chosen when configuring your PIP. These codes will be different each time the matrix of cells displays.
For example, next time the matrix may look as follows:
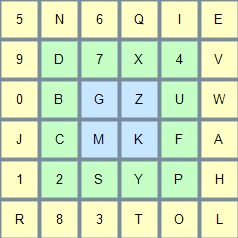
In this case, use the Use your GrIDsure PIP text box to type 5N6Q, and then press ENTER or click the Login button.
SMS token
To use the SMS token, you need to have an SMS-capable device that accepts SMS messages sent by Defender to your mobile phone number. For more information, contact your system administrator.
When you access a resource protected by Defender, you are prompted to enter your user name and password. You may also be prompted to enter your Defender PIN. Defender receives your request, generates a one-time password (OTP) and automatically sends it to your mobile phone number as an SMS message. You should receive your OTP within seconds. Then, you need to enter your PIN and the OTP at the prompt. If the entered PIN and OTP are correct, you are granted access to the protected resource.
NOTE: Defender uses two SMS providers with each having a different purpose. 2SMS is used during authentication and Telesign is used during sending information over e-mail after token creation process.






