Programming a VIP credential for a user
Before programming a VIP credential, make sure you enable the use of VIP credentials in Defender. For more information, see Enabling the use of VIP credentials.
In this step, you program and assign a VIP credential to the user you want. You can reassign an existing VIP credential from one user to another or assign a new VIP credential as required.
To program a VIP credential for a user
- On the computer on which the Defender Administration Console is installed, open the Active Directory Users and Computers tool (dsa.msc).
- Locate and double-click the required user object.
- In the dialog box that opens, click the Defender tab.
- Under the Tokens list, click the Program button, and then complete the wizard that starts.
For more information about the wizard steps and options, see Defender Token Programming Wizard reference.
After you complete the wizard, a new VIP credential entry appears in the Tokens list on the Defender tab.
Configuring YubiKey
You can allow users to authenticate via Defender by using one-time passwords generated with the YubiKey hardware token. Defender supports the YubiKey token programmed to work either in the Yubico OTP or OATH-HOTP mode.
See the following sections for instructions on enabling the use of the YubiKey token programmed in one of these modes:
Yubico OTP mode
When the YubiKey tokens you have purchased are in the Yubico OTP mode, to enable their use with Defender, you need to specify the client ID and API key provided with the tokens in the Defender Administration Console, and then configure self-service settings on the Defender Management Portal to enable users to self-register their YubiKey tokens on the Defender Self-Service Portal.
When a user registers the YubiKey on the Defender Self-Service Portal, the corresponding token object is automatically created in Active Directory.
To enable the use of YubiKey working in Yubico OTP mode
- In the Defender Administration Console, specify the client ID and API key provided to you with the YubiKey tokens:
- On the computer where the Defender Administration Console is installed, open the Active Directory Users and Computers tool (dsa.msc).
- In the left pane of the ADUC tool, expand the appropriate domain node, and click to select the Defender container.
- On the menu bar, select Defender | YubiCloud Client Configuration.
- In the dialog box that opens, type the client ID and API key provided to you with the YubiKey tokens.
- Click the Test button, and follow the on-screen instructions to ensure the supplied client ID and API key are valid. If the test completes successfully, click OK to save the client ID and API key.
- Configure the Defender Self-Service Portal to enable the registration of YubiKey tokens for the users:
- Open the Defender Management Portal. For more information, see Opening the portal.
- In the left pane, click the Self-Service Settings tab.
- In the right pane, on the General tab, use the Permissions area to add Active Directory groups and enable their members to register their YubiKey tokens via the Defender Self-Service Portal.
For the descriptions of elements you can use on the Self-Service Settings tab, see Configuring self-service for users.
OATH-HOTP mode
When the YubiKey tokens you have purchased are in the OATH-HOTP mode, to enable their use with Defender you need to import the YubiKey token objects into Active Directory by using the .txt import file (also known as the key file) containing token object definitions. Then, you can assign the imported token objects to users as necessary.
Normally, the .txt import file is provided together with the YubiKey tokens. Before importing token objects, you need to modify the .txt import file so that Defender can read its contents.
To enable the use of YubiKey working in OATH-HOTP mode
- Change the file name extension of the .txt import file to .csv.
- Open the .csv file in Microsoft Excel. The .csv file looks similar to the following:
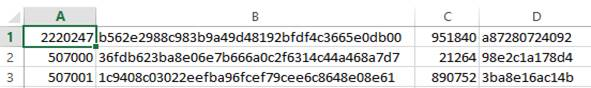
The columns in the file contain the following:
- A YubiKey serial number.
- B 160-bit secret set
- C Moving factor seed value.
- D Configuration password. Contains zeros if configuration password is not set.
- Delete column D.
- Save the .csv file. Now the file is ready for import.
- Import token objects from the .csv file into Active Directory. For instructions, see Importing hardware token objects.
- Assign the imported YubiKey token objects to users as necessary. For instructions, see Assigning a hardware token object to a user.
