Installing ISAPI Agent
To install ISAPI Agent
- Under a local administrator account, run the DefenderISAPIAgent.exe file supplied with the Defender distribution package.
- Follow the steps in the wizard to complete the ISAPI Agent installation.
- On the completion page of the wizard, select the Start Defender ISAPI Agent Configuration tool check box to configure the agent.
For more information about available configuration settings, see Configuring ISAPI Agent.
Configuring ISAPI Agent
To configure ISAPI Agent
- On the computer where the ISAPI Agent is installed, run the Defender ISAPI Agent Configuration tool.
- In the dialog box that opens, specify the ISAPI Agent settings, and then click OK.
The dialog box looks similar to the following:
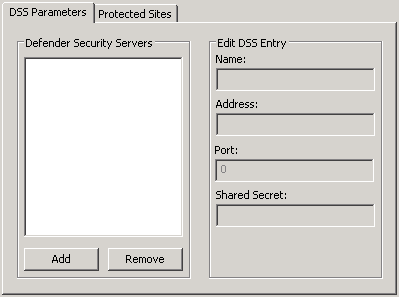
DSS Parameters tab
On this tab, specify the Defender Security Servers to which you want the ISAPI Agent to connect. You can use the following elements:
- Defender Security Servers Use this area to set up a list of the Defender Security Servers to which you want the ISAPI Agent to connect.
- Add Adds a new entry to the list. After adding a new entry, edit its properties in the Edit DSS Entry area.
- Remove Removes the selected entry from the list.
- Edit DSS Entry Use this area to specify or edit the name, address, port number, and shared secret of the Defender Security Server to which you want the ISAPI Agent to connect.
- Name Type the name of the Defender Security Server you want to use for user authentication.
- Address Type the IP address of the Defender Security Server.
- Port Type the communication port number configured on the access node you want the ISAPI Agent to use.
- Shared Secret Type the shared secret configured on the access node you want the ISAPI Agent to use.
Protected Sites tab
On this tab, select the check boxes next to the websites you want to protect with Defender. By default, Defender protects the whole website. If you want to protect only some parts of the website, use the default.acl file located in the ISAPI Agent installation folder. This file contains two sections where you can list parts that should and should not be protected. When specifying the website’s parts, use relative URLs.
Accessing Protected Website
To access protected website
- Using any supported browser, access the protected website. On the Login page, enter your user name and click Sign in.
- In the example below, users are required to authenticate themselves by entering their passcode. The authentication type depends on how the Defender policy has been configured. For example, if Defender is configured to use a token policy, the Enter Synchronous Response prompt will be displayed.
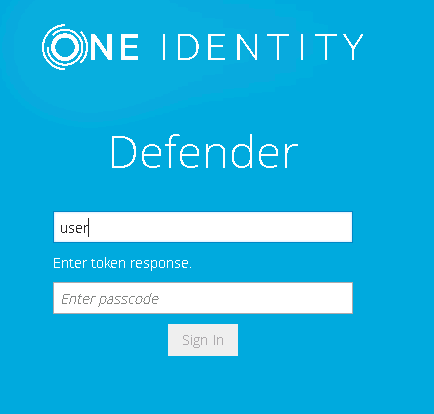
- If users have entered a valid response, they will be authenticated and permitted to access the website.
Securing Windows-based computers
You can configure Defender to authenticate users when they sign in to their Windows-based computers in your organization.
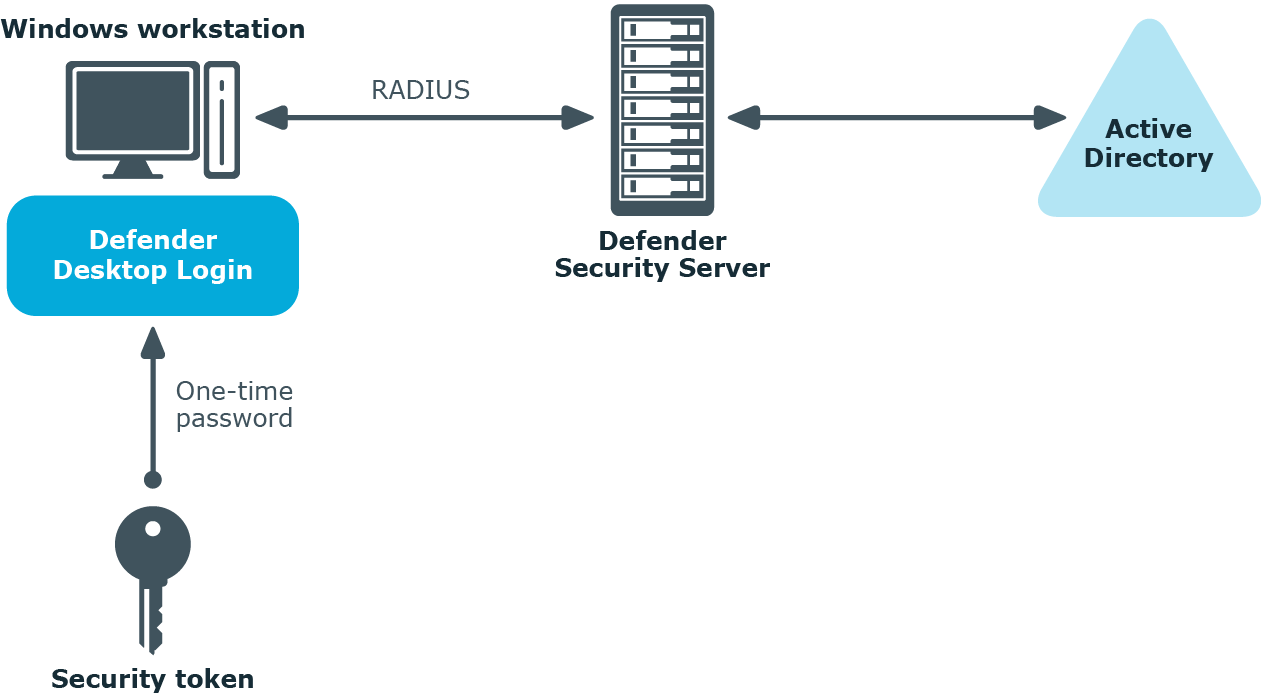
To secure Windows-based computers, in addition to the required Defender components you need to install and configure the component called the Defender Desktop Login on each computer you want to secure with Defender. For more information about installing and configuring the required Defender components, see Deploying Defender.