Complex Windows environments, which include Active Directory, can be mapped and synchronized in One Identity Manager. Administration of One Identity Manager objects such as users, contact groups, computers, and organizational units is possible using hierarchical domain structures in Active Directory.
One Identity Manager provides company employees with the user accounts required to allow you to use different mechanisms for connecting employees to their user accounts. You can also manage user accounts independently of employees and therefore set up administrator user accounts.
Administration of groups in One Identity Manager enables users to be supplied with necessary authorizations. You can set up organizational units in a hierarchical container structure in One Identity Manager. Organizational units (branches or departments) are used to logically organize objects such as users, groups, and computers. This makes it easier to manage objects.
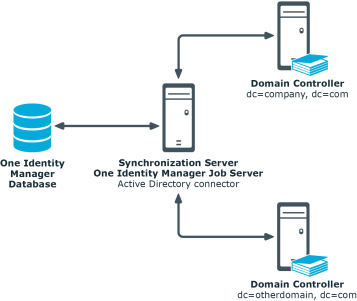
In One Identity Manager, the following servers play a role in managing Active Directory:
- Active Directory domain controller
Domain controller against which the Active Directory objects are synchronized. The synchronization server connects to this server in order to access the Active Directory objects.
- Synchronization server
The synchronization server for synchronizing data between One Identity Manager and Active Directory. The One Identity Manager Service with the Active Directory connector is installed on this server. The synchronization server connects to the Active Directory domain controller.
The Active Directory connector in One Identity Manager uses ADSI for communicating with a domain controller. The Active Directory connector is used for synchronization and provisioning Active Directory. The Active Directory connector communicates directly with a domain controller.
Figure 1: Architecture for synchronization
The following users are used in setting up and administration of Active Directory.
Table 1: Users
| Target system administrators |
Target system administrators must be assigned to the Target systems | Administrators application role.
Users with this application role:
-
Administer application roles for individual target system types.
-
Specify the target system manager.
-
Set up other application roles for target system managers if required.
-
Specify which application roles for target system managers are mutually exclusive.
-
Authorize other employees to be target system administrators.
-
Do not assume any administrative tasks within the target system. |
| Target system managers |
Target system managers must be assigned to the Target systems | Active Directory application role or a child application role.
Users with this application role:
-
Assume administrative tasks for the target system.
-
Create, change, or delete target system objects like user accounts or groups.
-
Edit password policies for the target system.
-
Prepare groups to add to the IT Shop.
-
Can add employees who have an other identity than the Primary identity.
-
Configure synchronization in the Synchronization Editor and define the mapping for comparing target systems and One Identity Manager.
-
Edit the synchronization's target system types and outstanding objects.
-
Authorize other employees within their area of responsibility as target system managers and create child application roles if required. |
| One Identity Manager administrators |
-
Create customized permissions groups for application roles for role-based login to administration tools in the Designer as required.
-
Create system users and permissions groups for non role-based login to administration tools in the Designer as required.
-
Enable or disable additional configuration parameters in the Designer as required.
-
Create custom processes in the Designer as required.
-
Create and configure schedules as required.
-
Create and configure password policies as required. |
| Administrators for the IT Shop |
Administrators must be assigned to the Request & Fulfillment | IT Shop | Administrators application role.
Users with this application role:
|
|
Product owner for the IT Shop |
Product owners must be assigned to the Request & Fulfillment | IT Shop | Product owners application role or a child application role.
Users with this application role:
- Approve through requests.
- Edit service items and service categories under their management.
|
| Administrators for organizations |
Administrators must be assigned to the Identity Management | Organizations | Administrators application role.
Users with this application role:
|
| Business roles administrators |
Administrators must be assigned to the Identity Management | Business roles | Administrators application role.
Users with this application role:
|
One Identity Manager supports synchronization with Active Directory, shipped with Windows Server 2012, Windows Server 2012 R2, Windows Server 2016, and Windows Server 2019.
To load Active Directory objects into the One Identity Manager database for the first time
- Prepare a user account with sufficient permissions for synchronizing in Active Directory.
-
One Identity Manager components for managing Active Directory environments are available if the TargetSystem | ADS configuration parameter is enabled.
- Install and configure a synchronization server and declare the server as a Job server in One Identity Manager.
- Create a synchronization project with the Synchronization Editor.
Detailed information about this topic

