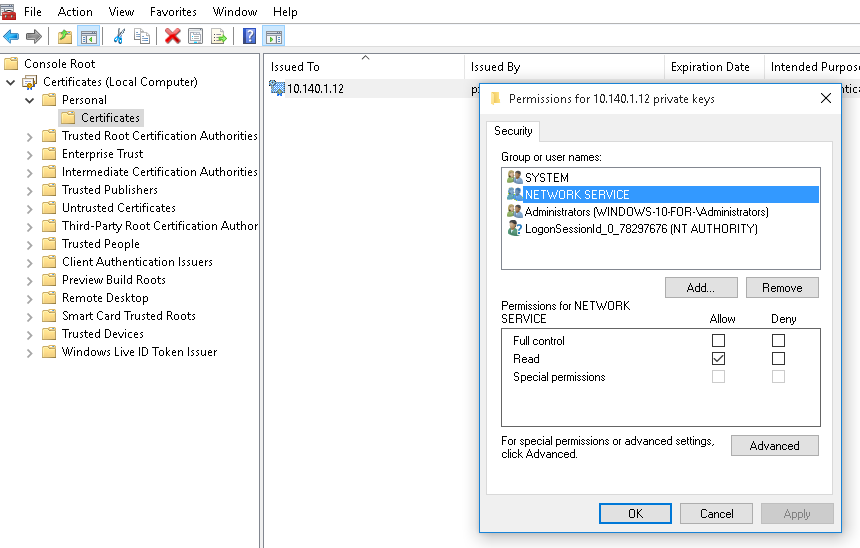
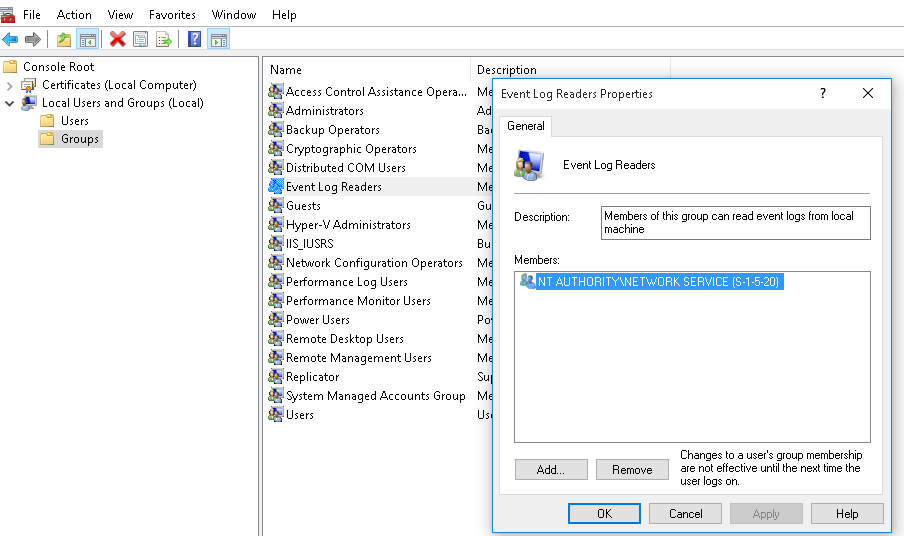
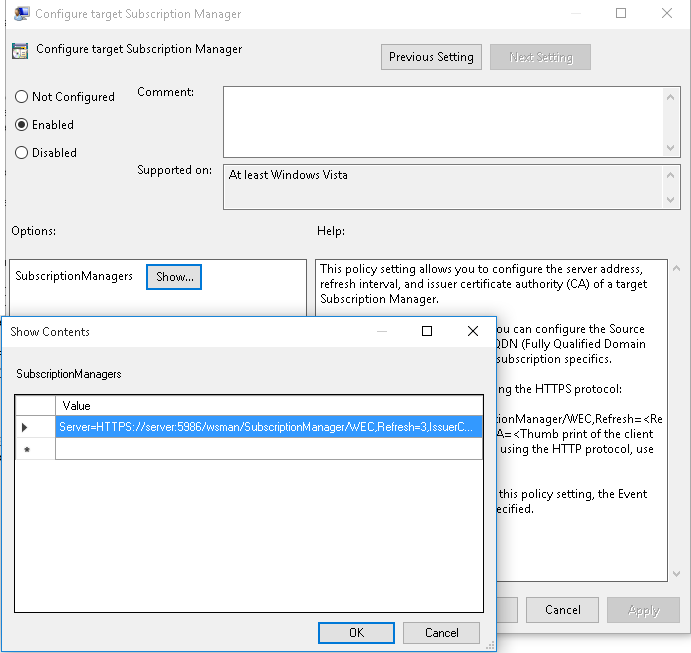
NOTE: Perform the procedure described in this section only if you want to use certificate-based authentication between Windows Event Forwarding (WEF) and Windows Event Collector (WEC).
When the Windows-based host and WEC start communicating for the first time, they authenticate each other by exchanging and verifying each other's certificates. The process begins with the Windows host requesting and verifying the WEC tool's certificates. After successful verification, the Windows host sends its own certificates for verification to WEC.
NOTE: If the Windows host fails to authenticate the WEC tool's certificates for some reason, check the Windows event logs for details.
For details on which event logs to look at, see Troubleshooting Windows Event Collector.
The example described in this section uses OpenSSL for certificate generation. Note, however, that you can generate certificates using the Windows Public Key Infrastructure (PKI).
|
|
Caution:
The examples in this section illustrate the creation of certificates with a default value of 365 days for expiration. However, most deployments remain operational for several years, so refreshing your certificates every 365 days is unnecessary. To avoid refreshing your certificates every year, One Identity recommends that you setup your host certificates with an expiration time longer than the default value of 365 days (as seen in the examples). |
To generate the SSL certificates for WEC, complete the following steps:
NOTE: The following configuration example works only if you have a functioning DNS server in your network. If you want to test WEC without a properly working DNS server, instead of host names, work with IP addresses in certificates and configurations. For an example configuration, see Creating certificates/Collecting Windows EventLog without installing extra software on Windows.
To generate SSL certificates for Windows Event Collector
-
Create two certificate template files for both the server and the clients.
NOTE: The templates shown here are examples only. Not all elements of the example *opts.cnf files are mandatory, for example, you do not need to define two DNS instances.
The contents of server-certopts.cnf:
[req] default_bits = 4096 default_md = sha256 req_extensions = req_ext keyUsage = keyEncipherment,dataEncipherment basicConstraints = CA:FALSE distinguished_name = dn [ req_ext ] subjectAltName = @alt_names extendedKeyUsage = serverAuth,clientAuth [ alt_names ] DNS.1 = <1st DNS hostname of server (preferably FQDN)> ... DNS.<N> = <Nth DNS hostname of server (preferably FQDN)> IP.1 = <1st IP of server> ... IP.<N> = <Nth IP of server> [dn]
Example: Contents of server-certopts.cnf
[req] default_bits = 4096 default_md = sha256 req_extensions = req_ext keyUsage = keyEncipherment,dataEncipherment basicConstraints = CA:FALSE distinguished_name = dn [ req_ext ] subjectAltName = @alt_names extendedKeyUsage = serverAuth,clientAuth [ alt_names ] DNS.1 = windowseventcollector.widgits DNS.2 = wec.widgits IP.1 = 10.64.10.2 [dn]
The contents of client-certopts.cnf:
[req] default_bits = 4096 default_md = sha256 req_extensions = req_ext keyUsage = keyEncipherment,dataEncipherment basicConstraints = CA:FALSE distinguished_name = dn [ req_ext ] subjectAltName = @alt_names extendedKeyUsage = serverAuth,clientAuth [ alt_names ] DNS.1 = <1st DNS hostname of client (preferably FQDN)> ... DNS.<N> = <Nth DNS hostname of client (preferably FQDN)> IP.1 = <1st IP of client> ... IP.<N> = <Nth IP of client> [dn]
Example: Contents of client-certopts.cnf
[req] default_bits = 4096 default_md = sha256 req_extensions = req_ext keyUsage = keyEncipherment,dataEncipherment basicConstraints = CA:FALSE distinguished_name = dn [ req_ext ] subjectAltName = @alt_names extendedKeyUsage = serverAuth,clientAuth [ alt_names ] DNS.1 = windowsclient01.widgits DNS.2 = client01.widgits IP.1 = 10.64.10.11 [dn]
-
Generate the certificate authority (CA):
$ openssl genrsa -out ca.key 4096 $ openssl req -x509 -new -nodes -key ca.key -days 3650 -out ca.crt -subj '<subject name for CA cert (must be formatted as /type0=value0/type1=value1/type2=..., characters may be escaped by \ (backslash), no spaces are skipped)>'
Example: Generating certificate authority (CA)
$ openssl genrsa -out ca.key 4096 $ openssl req -x509 -new -nodes -key ca.key -days 3650 -out ca.crt -subj '/C=AU/ST=Victoria/L=Melbourne/O=Internet Widgits Pty Ltd/OU=Operations/CN=Operations Root CA'
Place a copy of the ca.crt file in a directory of your choice. Take a note of the directory because you need to reference it in the cadir option of the WEC configuration file. For more information, see Configuring Windows Event Collector.
-
Save the thumbprint of the CA:
$ openssl x509 -in ca.crt -fingerprint -sha1 -noout | sed -e 's/\://g'
You will need the fingerprint to configure the event source computers that send log messages to Windows Event Collector. For details, see Configuring certificate-based authentication on event source computers.
-
Create the server certificate:
NOTE: The Common Name must be the FQDN (or IP address) of the Windows Event Collector server.
$ openssl req -new -newkey rsa:4096 -nodes -out server.csr -keyout server.key -subj '<subject name for server cert (must be formatted as /type0=value0/type1=value1/type2=..., characters may be escaped by \ (backslash), no spaces are skipped)>' $ openssl x509 -req -in server.csr -out server.crt -CA ca.crt -CAkey ca.key -CAcreateserial -extfile server-certopts.cnf -extensions req_ext -days 365
Example: Creating the server certificate
$ openssl req -new -newkey rsa:4096 -nodes -out server.csr -keyout server.key -subj '/C=AU/ST=Victoria/L=Melbourne/O=Internet Widgits Pty Ltd/OU=Operations/CN=windowseventcollector.widgits' $ openssl x509 -req -in server.csr -out server.crt -CA ca.crt -CAkey ca.key -CAcreateserial -extfile server-certopts.cnf -extensions req_ext -days 365
-
Create the certificates for the clients:
NOTE: The Common Name must be the FQDN (or IP address) of the client.
$ openssl req -new -newkey rsa:4096 -nodes -out client.csr -keyout client.key -subj '<subject name for client cert (must be formatted as /type0=value0/type1=value1/type2=..., characters may be escaped by \ (backslash), no spaces are skipped)>' $ openssl x509 -req -in client.csr -out client.crt -CA ca.crt -CAkey ca.key -CAcreateserial -extfile client-certopts.cnf -extensions req_ext -days 365
Example: Creating the certificates for the clients
$ openssl req -new -newkey rsa:4096 -nodes -out client.csr -keyout client.key -subj '/C=AU/ST=Victoria/L=Melbourne/O=Internet Widgits Pty Ltd/OU=Operations/CN=windowsclient01.widgits' $ openssl x509 -req -in client.csr -out client.crt -CA ca.crt -CAkey ca.key -CAcreateserial -extfile client-certopts.cnf -extensions req_ext -days 365
-
Export the certificates of the clients to the format recognized by the Windows Certificate Manager tool.
$ openssl pkcs12 -export -inkey client.key -in client.crt -certfile ca.crt -out client.p12