Specifying affected entitlements
In order to take entitlements into account in the rule, you must define at least one rule block that determines the affected entitlements for identities. Each rule block can contain more than one partial condition. The partial conditions are linked through the options all or at least one.
Figure 4: Rule block for affected entitlements
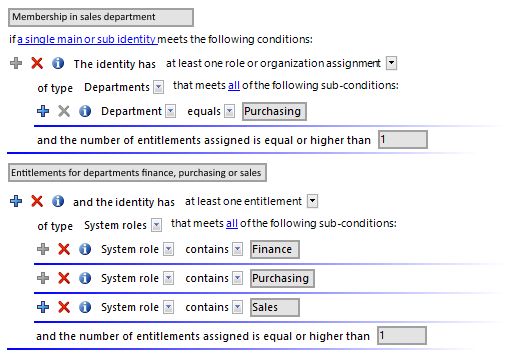
Use the following to options to limit the affected entitlements:
-
At least one entitlement
Define one entitlement per rule block.
Select the type of entitlement, such as a target system type or the Resource type, and define the partial condition.
Rules can be created for all the system entitlements displayed in the Unified Namespace. The rule conditions access the Unified Namespace database layers to do this.
-
At least one role or organization assignment
For each rule block, define the membership in a hierarchical role (application role, department, location, cost center, business role).
Select the type of role, such as Departments, and define the partial condition.
-
At least one function
Enter at least one SAP function to replace the rule.
This option can only be selected if the SAP R/3 Compliance Add-on Module module is installed. For more information, see the One Identity Manager Administration Guide for the SAP R/3 Compliance Add-on.
-
Number of entitlements
You specify how many entitlements the identity must have to violate the rule.
By default, a rule violation is identified, if one affected identity is assigned at least one object that fulfills the condition of the rule block. You can increase this number. The value 0 is not valid.
Define the partial conditions as follows:
-
Properties: Properties of the objects, such as Distinguished name or Resource type.
-
Assignments in other objects: Assignments of objects to other objects, for example, the assignment of a department as primary department of various identities.
-
Memberships: Memberships of entitlements in hierarchical roles and IT Shop structures. Assignments to identities or workdesks if the System roles permissions type has been selected.
Assignments of company resources to the roles, such as DepartmentHasADSGroup.
-
Permissions controls: Permissions controls defined for the selected target system.
NOTE: permissions controls are only created for custom target systems.
-
Has extended property Extended properties assigned to the objects.
-
Has extended property in group: Extended properties from the selected extended property group that are assigned to the objects.
-
Has extended property in range: Extended properties assigned to the objects and for which a range of values is defined. The rule verifies the correct value.
-
SQL Clause: Freely defined SQL condition (WHERE clause). For more information about the WHERE clause wizard, see the One Identity Manager User Guide for One Identity Manager Tools User Interface.
Related topics
A simple rule example
The following examples show how rules can be created with the help of the Rule Editor and the effects of each option.
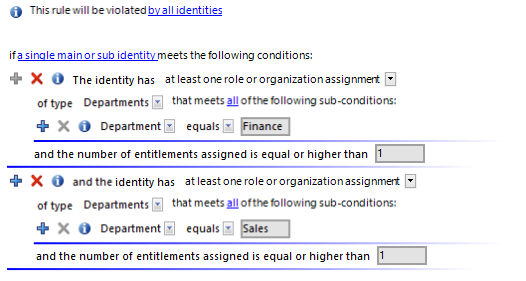
Example 1
Identities from department A may not belong to department B at the same time.
Define:
-
The by all identities and the combination of main and sub identities in the rule block for the affected identities
-
Two rule blocks for the affected entitlements with the option at least one role or organization assignment.
Figure 5: Rule condition for example 1
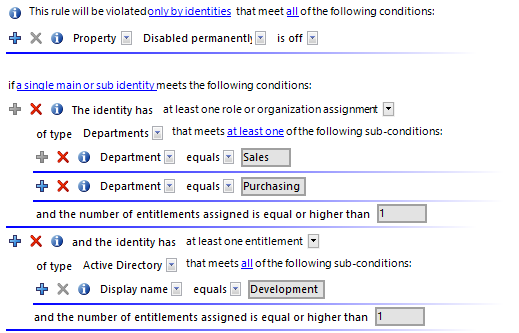
Example 2
Identities from the department A or department B are not permitted to access the Active Directory group xyz. This rule is only checked for identities who are activated.
Define:
-
The by all identities, all, and a single main or sub identity options in the rule block for the affected identities.
-
Two rule blocks for the affected entitlements with the options:
-
at least one role or organization assignment and
-
at least one entitlement.
Figure 6: Rule condition for example 2
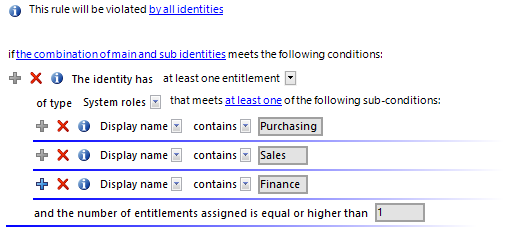
Example 3
All permitted entitlements are assigned to persons through system roles. One identity can have a maximum of two system roles. If an identity has subidentities, the rule is also violated if the entitlements of main and sub identities result together in a rule violation.
There are three system roles: Package for department A, Package for department B, Package for department C
One identity has two subidentities. The main identity (HI) and the two subidentities (SI1 and SI2) are each assigned a system role.
HI: Package for department A
SI1: Package for department B
SI2: Package for department C
Define:
-
The by all identities and the combination of main and sub identities in the rule block for the affected identities
-
One rule block for the affected entitlements with the option at least one entitlement of type System roles that fulfills at least one of the following partial conditions
-
Three partial conditions: System role is equal Package for department [A|B|C]
-
The number of entitlements assigned is larger or equal to 3.
Because the main identity has all three system roles due to its subidentities, the main identity violates this (and only this) rule.
Rule conditions in advanced mode
There are two ways of defining rule conditions, the simple definition and advanced mode. The simple definition is used as default to create rule conditions with the Rule Editor. For more information, see Basics for using the Rule Editor.
In advanced mode, identity's properties are defined in the rule condition that lead to a rule violation. The assignments are determined directly via the respective tables, which contain the selected objects (for example, PersonHasSAPGRoup or Person).
To use advanced mode
-
In the Designer, set the QER | ComplianceCheck | SimpleMode | NonSimpleAllowed configuration parameter.
On the main data form for a rule, the options Rule for cyclical testing and risk assessment in IT Shop and Rule only for cyclical testing are displayed.
-
Set Rule only for cyclical testing.
-
Confirm the security prompt with Yes.
The filter designer is displayed.
NOTE:
-
You cannot return to the simple definition once a rule condition has been entered in advanced mode!
-
Rules in advanced mode are not taken into account by rule checks in the IT Shop request approval processes. No IT Shop properties can be defined for these rules. The IT Shop properties tab does not appear on the main data form for this rule.
Figure 7: Advanced mode condition
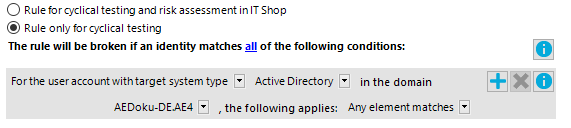
Rule conditions in advanced mode are based on the Identities base object (Person table). The completed database query is put together internally:
Select Firstname, Lastname from Person where <Rule condition> order by 1,2
NOTE: If you select the For the account with the target system type or For the entitlement with target system type condition type in the filter designer, only columns that are mapped in Unified Namespace and for which the Display in the filter designer column property is enabled can be selected.
For more information about using the filter designer, see the One Identity Manager User Guide for One Identity Manager Tools User Interface.
Table 22: Permitted condition types
|
Property |
Properties of identities. The permitted properties menu is already limited to the most important identity properties. |
|
For the account with the target system type |
Identity’s user account. Valid user account properties depend on which target system is selected. |
|
For entitlements with the target system type |
Identity target system group. Valid group properties depend on which target system is selected. |
|
SQL Query |
Free choice of SQL query (WHERE clause). To use the WHERE clause wizard, click  . . |
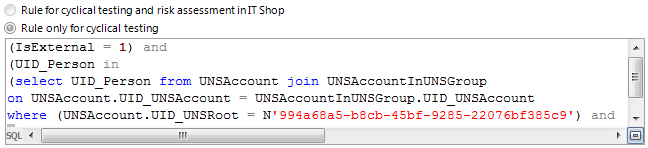
Rule condition as SQL query
You can formulate rule conditions directly in advanced mode as an SQL query.
To formulate a rule condition directly as an SQL query
-
In the Designer, set the QER | ComplianceCheck | PlainSQL configuration parameter.
-
Select Rule only for cyclical testing.
-
Select the Enable SQL definition task for the working copy.
NOTE: Rule conditions can only be formulated through an SQL query if the QER | ComplianceCheck | SimpleMode configuration parameter is not set and the QER | ComplianceCheck | PlainSQL configuration parameter is set.
Figure 8: Direct SQL query input






 .
.