Replay encrypted audit trails from the command line
|

|
Caution:
Starting with SPS 5 F4, the way audit trails are encrypted has changed to make the encryption process more secure. Audit trails are now encrypted with AES-128-GCM and hashed with the SHA-512 method. This also means that in order to index and replay audit trails, you need to upgrade both your external indexers and your Safeguard Desktop Player. Earlier versions (and Audit Player) will not be able to handle audit trails (with or without encryption) recorded with SPS 5 F4 and later. |
The following describes how to replay an encrypted audit trail using the command line. Use this method if you want to import the private key only temporarily, or if you want to automate the process. To import the required certificates using the graphical interface of Safeguard Desktop Player, see Replay encrypted audit trails.
Prerequisites:
-
To replay encrypted audit trails, the private key of the certificate used to encrypt the audit trail must be available on the host running the Safeguard Desktop Player. On Microsoft Windows, the Safeguard Desktop Player can retrieve this certificate from Windows Certificate Store > Current User > Personal Certificate Store.
-
To validate digitally-signed audit trails, the respective certificates that issued the certificates used to sign the audit trail must be available and valid on the host running the Safeguard Desktop Player. (This is the certificate set at Policies > Audit policies > Enable signing on the SPS interface.) On Microsoft Windows, the Safeguard Desktop Player can validate this certificate from Windows Certificate Store > Local Computer > Trusted Root Certification Authorities. Note that in case of certificate chains, the whole chain must be imported in this Certificate Store.
-
To validate timestamped audit trails, the CA certificate of SPS must be available on the host running the Safeguard Desktop Player. (This is the CA certificate of SPS set at Basic Settings > Management > SSL Certificates > CA X.509 Certificate.) On Microsoft Windows, the Safeguard Desktop Player can retrieve this certificate from Windows Certificate Store > Local Computer > Trusted Root Certification Authorities.
The certificates and the private keys must be available as a file in PEM format, other formats are not supported. Note that on Microsoft Windows, you cannot import CA certificates from a shared drive. In this case, copy the certificate to a local folder and import it from there.
|

|
NOTE:
Certificates are used as a container and delivery mechanism. For encryption and decryption, only the keys are used. |
One Identity recommends using 2048-bit RSA keys (or stronger).
To replay an encrypted audit trail using the command line
Start a command prompt and navigate to the installation directory of Safeguard Desktop Player. By default, it is C:\Documents and Settings\<username>\Software\Safeguard\Safeguard Desktop Player\ on Microsoft Windows platforms, ~/SafeguardDesktopPlayer on Linux, and /Applications/Safeguard Desktop Player.app/Contents/Resources/ on MacOS.
-
-
If the private key is password-protected, execute the following command:
player --key <path\to\your\private-key.pem>:<password-to-the-private-key>
For example, if the private key file is C:\temp\my-key.pem and its password is secret, the command is player --key C:\temp\my-key.pem:secret
Otherwise, use the following command:
player --key <path\to\your\private-key.pem>
-
If the audit trail is timestamped or signed, you must have the proper certificate to validate the audit trail. Include the path to the certificate in the command line when starting the Safeguard Desktop Player:
player --cert <path\to\the\certificate.pem> --key <path\to\your\private-key.pem>:<password-to-the-private-key>
-
Open the encrypted audit trail. The Safeguard Desktop Player will attempt to decrypt it with the private key you provided. If decryption is successful, you can replay the audit trail. Alternatively, you can specify the audit trail to open from the command line, for example:
player --cert <path\to\the\certificate.pem> --key <path\to\your\private-key.pem>:<password-to-the-private-key> <path\to\audit-trail.zat>
Replay audit files in follow mode
|

|
Caution:
Starting with SPS 5 F4, the way audit trails are encrypted has changed to make the encryption process more secure. Audit trails are now encrypted with AES-128-GCM and hashed with the SHA-512 method. This also means that in order to index and replay audit trails, you need to upgrade both your external indexers and your Safeguard Desktop Player. Earlier versions (and Audit Player) will not be able to handle audit trails (with or without encryption) recorded with SPS 5 F4 and later. |
The following describes how to follow active connections in semi-real time.
Prerequisites:
To be able to follow active connections, you must be permitted to authorize the sessions of the relevant connection policy. For details on how you can configure that, see "Configuring four-eyes authorization" in the Administration Guide.
Every time you open an .srs file in Safeguard Desktop Player for replay, you are required to authenticate yourself to SPS through the user interface of Safeguard Desktop Player. To be able to access SPS and follow active sessions, you must have:
On Microsoft Windows, the Safeguard Desktop Player retrieves the SSL certificate from Windows Certificate Store > Local Computer > Trusted Root Certification Authorities.
On Linux or MacOS, import the SSL certificate to Safeguard Desktop Player by completing the following steps:
-
In SPS, navigate to Basic Settings > Management > SSL certificates.
-
Click the certificate in the CA X.509 certificate field.
-
In the pop-up window that comes up, click PEM. This will download the the CA's X.509 certificate in PEM format. The certificate must be available as a file in PEM format, other formats are not supported.
-
In Safeguard Desktop Player, click  at the top, on the right. Select Key/Certificate import.
at the top, on the right. Select Key/Certificate import.
-
Click  , then select the certificate PEM file that you downloaded from SPS.
, then select the certificate PEM file that you downloaded from SPS.
-
Click Load. The Safeguard Desktop Player displays the details of the certificate.
-
Click Import.
To follow active connections in semi-real time
-
On the web interface of SPS, go to Active Connections, and click  next to the connection you wish to monitor in semi-real time.
next to the connection you wish to monitor in semi-real time.
-
In the Safeguard Desktop Player application, click OPEN, and select the audit trail to replay.
Safeguard Desktop Player displays the sessions stored in the audit trail file.
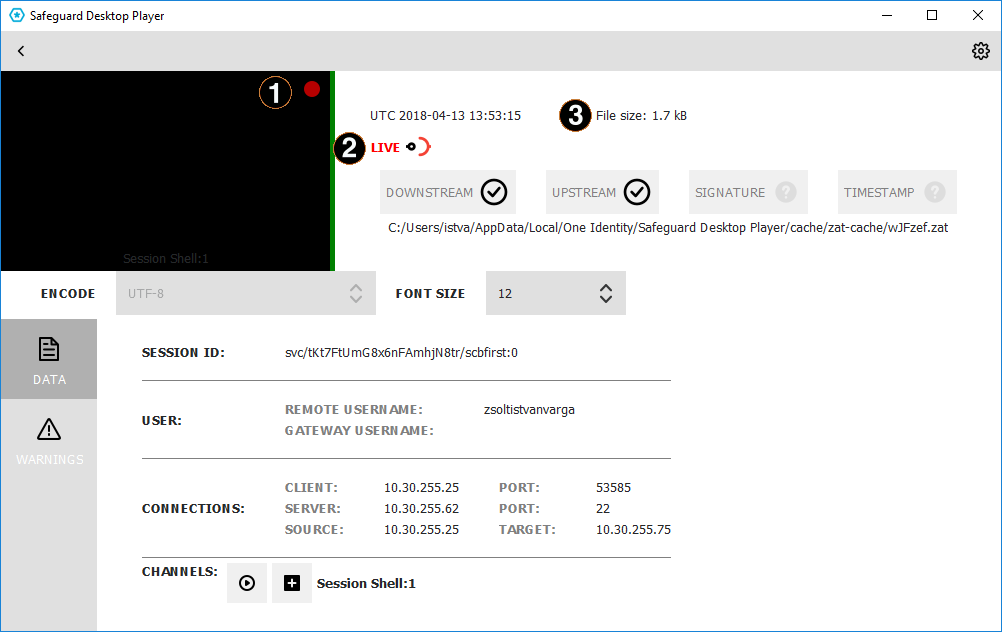
-
Red blinking light.
When the red blinking light is displayed, it indicates an ongoing, active connection. When neither the LIVE label and icon nor the red blinking light are displayed, it indicates that the connection has ended.
-
LIVE status indicator.
The indicator shows three different states:
-
 When it is completely red, it indicates that the connection is active and there is some user interaction on the client.
When it is completely red, it indicates that the connection is active and there is some user interaction on the client.
-
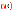 When the LIVE label is red but the icon is half red, half black, it indicates that the connection is active but there is no user interaction on the client.
When the LIVE label is red but the icon is half red, half black, it indicates that the connection is active but there is no user interaction on the client.
-
When neither the LIVE label and icon nor the red blinking light are displayed, it indicates that the connection has ended.
-
File size.
Displays the size of the .zat file loaded. In the case of an active, live connection, the size continuously increases.
-
Click the thumbnail to start replaying the audit file. Alternatively, click the  icon next to the channel you want to replay.
icon next to the channel you want to replay.
-
The replay window opens.
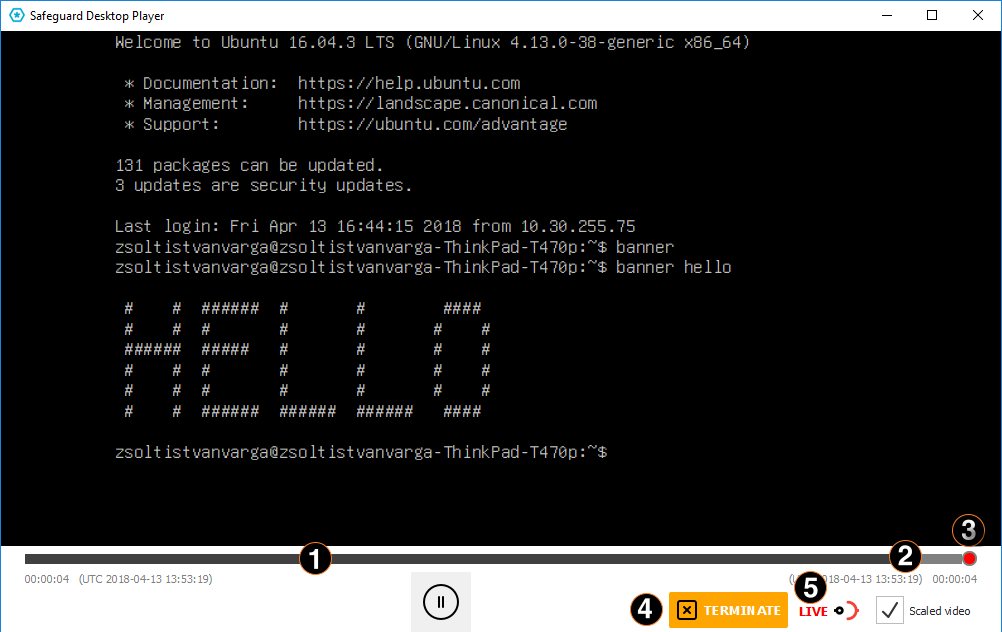
-
Blue progress bar.
Shows progress in the replay of the live session. When replay is paused (by hitting the Space key, clicking the Pausebutton or the video screen), the progress bar stops. It will only start progressing again, once replay is restarted (by hitting the Space key, clicking the Playbutton or the video screen).
-
Gray progress bar.
Shows progress in the loading and conversion of the audit trail file to video. The bar keeps progressing until the session is active. When the video is paused, the gray bar progresses further than the blue bar, indicating to the user that there are some parts of the video that they have not watched yet.
-
Red light.
When the red light is displayed, it indicates an ongoing, active connection. When both the LIVE label and icon, as well as the red light turn black, it indicates that the connection has ended.
-
Terminate.
Terminate the session you are monitoring if you notice some user action that poses a security risk.
-
LIVE status indicator.
The indicator shows three different states:
-
 When it is completely red, it indicates that the connection is active and there is some user interaction on the client.
When it is completely red, it indicates that the connection is active and there is some user interaction on the client.
-
 When the LIVE label is red but the icon is half red, half black, it indicates that the connection is active but there is no user interaction on the client.
When the LIVE label is red but the icon is half red, half black, it indicates that the connection is active but there is no user interaction on the client.
-
 When both the LIVE label and icon are black, it indicates that the connection has ended.
When both the LIVE label and icon are black, it indicates that the connection has ended.
|

|
TIP:
When you are replaying terminal-based audit trails (for example, SSH or TELNET), you can change the font size of the displayed text by holding down the Ctrl key and scrolling your mouse wheel. |
When the session ends, a  button is displayed. On clicking this button, the player reverts to "normal" replay mode, with options such as changing replay speed, or the seeker becoming available again.
button is displayed. On clicking this button, the player reverts to "normal" replay mode, with options such as changing replay speed, or the seeker becoming available again.
Search in the content of the current audit file
Safeguard Desktop Player allows you to search in the contents of the recorded audit trails, for example, in commands that the user executed in the session, or to find a specific text that was displayed on the screen.
You can also search in the contents of the audit trails for trails of graphical sessions created and indexed with SPS 6.0.
To search in the content of an audit file
-
In the Safeguard Desktop Player application, click OPEN, and select the audit trail to replay. If the audit trail is encrypted, see Replay encrypted audit trails.
Safeguard Desktop Player displays the sessions stored in the audit trail file.
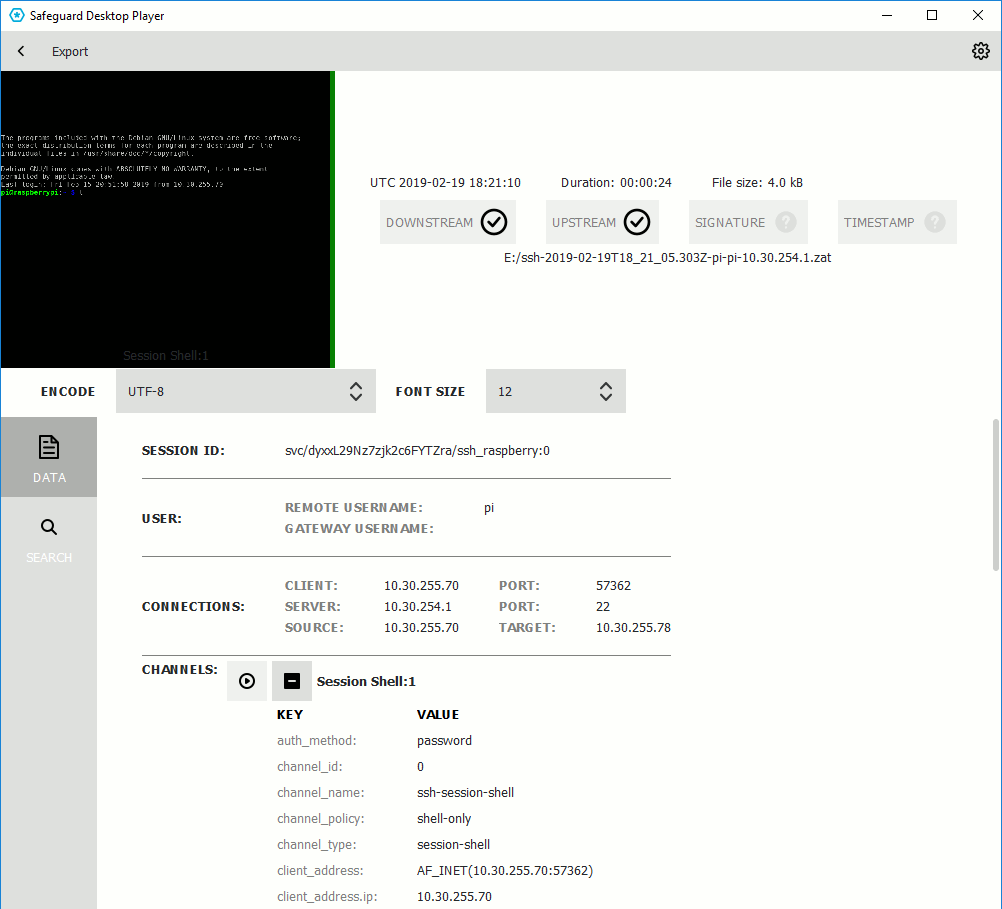
-
Click SEARCH and enter your search keywords into the Search in content field. Note that Safeguard Desktop Player creates the index of the content when opening the file, and searching is disabled until creating the index is finished. Depending on the length of the audit trail, this can take several minutes.
Safeguard Desktop Player displays the search results and highlights the periods of the audit trail when the search keywords were visible. For details on the search syntax, see Search query examples.
Click  to replay the audit trail. To search while replaying an audit trail, click the magnifying glass icon.
to replay the audit trail. To search while replaying an audit trail, click the magnifying glass icon.
The following sections provide examples for different search queries.
For details on how to use more complex keyphrases that are not covered in this guide, see the Apache Lucene documentation.
Searching for exact matches
By default, One Identity Safeguard for Privileged Sessions (SPS) searches for keywords as whole words and returns only exact matches. Note that if your search keywords include special characters, you must escape them with a backslash (\) character. For details on special characters, see Searching for special characters. The following characters are special characters: + - & | ! ( ) { } [ ] ^ " ~ * ? : \ /
Example: Searching for exact matches
| Search expression |
example |
| Matches |
example |
| Does not match |
examples
example.com
query-by-example
exam |
To search for an exact phrase, enclose the search keywords in double quotes.
| Search expression |
"example command" |
| Matches |
example command |
| Does not match |
example
command
example: command |
To search for a string that includes a backslash characters, for example, a Windows path, use two backslashes (\\).
| Search expression |
C\:\\Windows |
| Matches |
C:\Windows |
Combining search keywords
You can use boolean operators – AND, OR, NOT, and + (required), – to combine search keywords. More complex search expressions can also be constructed with parentheses. If you enter multiple keywords,
Example: Combining keywords in search
| Search expression |
keyword1 AND keyword2 |
| Matches |
(returns hits that contain both keywords) |
| Search expression |
keyword1 OR keyword2 |
| Matches |
(returns hits that contain at least one of the keywords) |
| Search expression |
"keyword1 keyword2" NOT "keyword2 keyword3" |
| Matches |
(returns hits that contain the first phrase, but not the second) |
| Search expression |
+keyword1 keyword2 |
| Matches |
(returns hits that contain keyword1, and may contain keyword2) |
To search for expressions that can be interpreted as boolean operators (for example: AND), use the following format: "AND".
Example: Using parentheses in search
Use parentheses to create more complex search expressions:
| Search expression |
(keyword1 OR keyword2) AND keyword3 |
| Matches |
(returns hits that contain either keyword1 and keyword3, or keyword2 and keyword3) |
Using wildcard searches
You can use the ? and * wildcards in your search expressions.
Example: Using wildcard ? in search
The ? (question mark) wildcard means exactly one arbitrary character. Note that it does not work for finding non-UTF-8 or multibyte characters. If you want to search for these characters, the expression ?? might work, or you can use the * wildcard instead.
You cannot use a * or ? symbol as the first character of a search.
| Search expression |
example? |
| Matches |
example1
examples
example? |
| Does not match |
example.com
example12
query-by-example |
| Search expression |
example?? |
| Matches |
example12 |
| Does not match |
example.com
example1
query-by-example |
Example: Using wildcard * in search
The * wildcard means 0 or more arbitrary characters. It finds non-UTF-8 and multibyte characters as well.
| Search expression |
example* |
| Matches |
example
examples
example.com |
| Does not match |
query-by-example
example* |
Example: Using combined wildcards in search
Wildcard characters can be combined.
| Search expression |
ex?mple* |
| Matches |
example1
examples
example.com
exemple.com
example12 |
| Does not match |
exmples
query-by-example |
Searching for special characters
To search for the special characters, for example, question mark (?), asterisk (*), backslash (\) or whitespace ( ) characters, you must prefix these characters with a backslash (\). Any character after a backslash is handled as character to be searched for. The following characters are special characters: + - & | ! ( ) { } [ ] ^ " ~ * ? : \ /
Example: Searching for special characters
To search for a special character, use a backslash (\).
| Search expression |
example\? |
| Matches |
example? |
| Does not match |
examples
example1 |
To search for a string that includes a backslash characters, for example, a Windows path, use two backslashes (\\).
| Search expression |
C\:\\Windows |
| Matches |
C:\Windows |
To search for a string that includes a slash character, for example, a UNIX path, you must escape the every slash with a backslash (\/).
| Search expression |
\/var\/log\/messages |
| Matches |
/var/log/messages |
| Search expression |
\(1\+1\)\:2 |
| Matches |
(1+1):2 |
Searching in commands and window titles
For terminal connections, use the command: prefix to search only in the commands (excluding screen content). For graphical connections, use the title: prefix to search only in the window titles (excluding screen content). To exclude search results that are commands or window titles, use the following format: keyword AND NOT title:[* TO *].
You can also combine these search filters with other expressions and wildcards, for example, title:properties AND gateway.
Example: Searching in commands and window titles
| Search expression |
command:"sudo su" |
| Matches |
sudo su as a terminal command |
| Does not match |
sudo su in general screen content |
| Search expression |
title:settings |
| Matches |
settings appearing in the title of an active window |
| Does not match |
settings in general screen content |
To find an expression in the screen content and exclude search results from the commands or window titles, see the following example.
| Search expression |
properties AND NOT title:[* TO *] |
| Matches |
properties appearing in the screen content, but not as a window title. |
| Does not match |
properties in window titles. |
You can also combine these search filters with other expressions and wildcards.
| Search expression |
title:properties AND gateway |
| Matches |
A screen where properties appears in the window title, and gateway in the screen content (or as part of the window title). |
| Does not match |
Screens where both properties and gateway appear, but properties is not in the window title. |
Searching for fuzzy matches
Fuzzy search uses the tilde ~ symbol at the end of a single keyword to find hits that contain words with similar spelling to the keyword.
Example: Searching for fuzzy matches
| Search expression |
roam~ |
| Matches |
roams
foam |
Proximity search
Proximity search uses the tilde ~ symbol at the end of a phrase to find keywords from the phrase that are within the specified distance from each other.
Example: Proximity search
| Search expression |
"keyword1 keyword2"~10 |
| Matches |
(returns hits that contain keyword1 and keyword2 within 10 words from each other) |
Adjusting the relevance of search terms
By default, every keyword or phrase of a search expression is treated as equal. Use the caret ^ symbol to make a keyword or expression more important than the others.
Example: Adjusting the relevance of search terms
| Search expression |
keyword1^4 keyword2 |
| Matches |
(returns hits that contain keyword1 and keyword2, but keyword1 is 4-times more relevant) |
| Search expression |
"keyword1 keyword2"^5 "keyword3 keyword4" |
| Matches |
(returns hits that contain keyword1 keyword2 and keyword3 keyword4, but keyword1 keyword2 is 5-times more relevant) |



 at the top, on the right. Select Key/Certificate import.
at the top, on the right. Select Key/Certificate import. , then select the certificate PEM file that you downloaded from SPS.
, then select the certificate PEM file that you downloaded from SPS. next to the connection you wish to monitor in semi-real time.
next to the connection you wish to monitor in semi-real time.
 When it is completely red, it indicates that the connection is active and there is some user interaction on the client.
When it is completely red, it indicates that the connection is active and there is some user interaction on the client. When the LIVE label is red but the icon is half red, half black, it indicates that the connection is active but there is no user interaction on the client.
When the LIVE label is red but the icon is half red, half black, it indicates that the connection is active but there is no user interaction on the client. icon next to the channel you want to replay.
icon next to the channel you want to replay.
 When both the LIVE label and icon are black, it indicates that the connection has ended.
When both the LIVE label and icon are black, it indicates that the connection has ended. button is displayed. On clicking this button, the player reverts to "normal" replay mode, with options such as changing replay speed, or the seeker becoming available again.
button is displayed. On clicking this button, the player reverts to "normal" replay mode, with options such as changing replay speed, or the seeker becoming available again.