Analyzing role memberships and identity assignments
The Overview of all assignments report is displayed for some objects, such as authorizations, compliance rules, or roles. The report finds all the roles, for example, departments, cost centers, locations, business roles, and IT Shop structures in which there are identities who own the selected base object. In this case, direct as well as indirect base object assignments are included.
Example:
-
If the report is created for a resource, all roles are determined in which there are identities with this resource.
-
If the report is created for a group or another system entitlement, all roles are determined in which there are identities with this group or system entitlement.
-
If the report is created for a compliance rule, all roles are determined in which there are identities who violate this compliance rule.
-
If the report is created for a department, all roles are determined in which identities of the selected department are also members.
-
If the report is created for a business role, all roles are determined in which identities of the selected business role are also members.
To display detailed information about assignments
-
To display the report, select the base object from the navigation or the result list and select the Overview of all assignments report.
-
Click the  Used by button in the report toolbar to select the role class for which you want to determine whether roles exist that contain identities with the selected base object.
Used by button in the report toolbar to select the role class for which you want to determine whether roles exist that contain identities with the selected base object.
All the roles of the selected role class are shown. The color coding of elements identifies the role in which there are identities with the selected base object. The meaning of the report control elements is explained in a separate legend. To access the legend, click the  icon in the report's toolbar.
icon in the report's toolbar.
-
Double-click a control to show all child roles belonging to the selected role.
-
By clicking the  button in a role's control, you display all identities in the role with the base object.
button in a role's control, you display all identities in the role with the base object.
-
Use the small arrow next to  to start a wizard that allows you to bookmark this list of identities for tracking. This creates a new business role to which the identities are assigned.
to start a wizard that allows you to bookmark this list of identities for tracking. This creates a new business role to which the identities are assigned.
Figure 13: Toolbar of the Overview of all assignments report.
Table 33: Meaning of icons in the report toolbar
|

|
Show the legend with the meaning of the report control elements |
|

|
Saves the current report view as a graphic. |
|
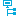
|
Selects the role class used to generate the report. |
|

|
Displays all roles or only the affected roles. |
Deactivating and deleting identities
How identities are handled, particularly in the case of permanent or partial withdrawal of an identity, varies between individual companies. There are companies that never delete identities, and only deactivate them when they leave the company.
Detailed information about this topic
Temporarily deactivating identities
NOTE: Identities that are temporarily deactivated can no longer log in to One Identity Manager.
The identity has temporarily left the company and is expected to return at a predefined date. The desired course of action could be to disable the user account and remove all group memberships. Or the user accounts could be deleted and restored on reentry even if it is with a new system identification number (SID).
Temporary deactivation of an identity is triggered by:
NOTE:
-
Configure the Lock accounts of identities that have left the company schedule in the Designer. This schedule checks the start date for deactivating and sets the Temporarily inactive option when it is reached.
-
In the Designer, configure the Enable temporarily disabled accounts schedule. This schedule monitors the end date of the inactive period and activates the identity with their user accounts when the period expires. Identity's user accounts that were disabled before the period of temporary absence are also re-enabled once the period has expired.
Related topics
Permanently deactivating identities
NOTE: Identities that are permanently deactivated can no longer log in to One Identity Manager.
Identities can be deactivated permanently when, for example, they leave the company. It might be necessary, to remove access to this identity's entitlements in connected target systems and their company resources.
Effects of permanent deactivating an identity are:
-
The identity cannot be assigned to identities as a manager.
-
The identity cannot be assigned to roles as a supervisor.
-
The identity cannot be assigned to attestation policies as an owner.
-
There is no inheritance of company resources through roles, if the additional No inheritance option is set for an identity.
-
The identity's user accounts are locked or deleted and then removed from group memberships.
Permanent deactivation of an identity is triggered by:
-
The Deactivate identity permanently task
This task ensures that the Permanently deactivates option is enabled and the leaving date and last working day are set to the current date.
-
The leaving date is reached
NOTE:
-
In the Designer, check the Lock accounts of identities that have left the company schedule. This schedule regularly checks the leaving date and sets the Permanently deactivated option on reaching the date.
-
The Re-enable identity task ensures that the identity is re-enabled.
-
The Denied certification status
If an identity's certification status is set to Denied manually or as a result of attestation, the identity is immediately deactivated permanently. If the identity's certification status is changed to Certified, the identity is activated again.
NOTE: This function is only available if the Attestation Module is installed.
Related topics
Used by button in the report toolbar to select the role class for which you want to determine whether roles exist that contain identities with the selected base object.
icon in the report's toolbar.
button in a role's control, you display all identities in the role with the base object.
to start a wizard that allows you to bookmark this list of identities for tracking. This creates a new business role to which the identities are assigned.



