The main feature of One Identity Manager is to map identities together with the main data and permissions available to them in different target systems. To achieve this, information about user accounts and permissions can be read from the target system into the One Identity Manager database and linked to identities. This provides an overview of the permissions for each identity in all of the connected target systems. One Identity Manager offers the option of managing user accounts and their permissions. You can provision modifications in the target systems. Identities are supplied with the necessary permissions in the connected target systems according to their function in the company. Regular synchronization keeps data consistent between target systems and the One Identity Manager database.
Because requirements vary between companies, One Identity Manager offers different methods for supplying user accounts to identities. One Identity Manager supports the following methods for linking identities and their user accounts:
-
Identities can automatically obtain their user accounts through One Identity Manager account definitions.
-
When user accounts are inserted in One Identity Manager, they can be automatically assigned to an existing identity or a new identity can be created if necessary.
-
Identity and user account data in One Identity Manager can be manually entered and assigned to each other.
Detailed information about this topic
The requirements of a company’s user administration are often different not only in the existing target system types, but also in the individual target systems of a target system type.
Requirements for user account administration might be, for example:
Target system type Active Directory with Microsoft Exchange
-
In domain A, a user account should be automatically created for each internal identity. The information for the container and home server are based on the department and the location of the person. Each user account in the domain is automatically allocated a Microsoft Exchange mailbox.
-
In domain B, the user accounts are administrated independently of the identity data. Microsoft Exchange mailboxes can only be allocated by requesting them in the IT shop.
Target system type HCL Domino
Target system type SAP R/3
-
All members of the personnel department are automatically allocated a user account in an SAP Client 101.
-
The members of the purchasing department are automatically allocated a user account in the SAP Client 102 the moment they are assigned the appropriate role.
-
The user accounts for the SAP Client 103 are allocated exclusively through a request process.
One Identity Manager uses different mechanisms to assign user accounts to identities.
Initial assignment of user accounts
The user accounts are initially read into One Identity Manager from a target system through synchronization. In doing so, the existing identities can automatically be assigned to the user accounts. New identities can be created and assigned to user accounts if necessary. The criteria for these automatic assignments are defined on a company-specific basis. The extent of the attributes an identity inherits on their user account through account definitions can be changed after checking the user accounts. The loss of user accounts through system changes can therefore be avoided. User account verification can be carried out manually or by using scripts.
Assigning user accounts during work hours
One Identity Manager uses special account definitions for allocating user accounts to identities during working hours. Account definitions can be created for each target system of the appointed target system type, for example, the different domains of an Active Directory environment or the individual clients of an SAP R/3 system. A priority is applied to the account definitions in order to ensure that a Microsoft Exchange mailbox, for instance, is only created when an Active Directory user account is available.
An identity can obtain a user account though the integrated inheritance mechanism by either direct assignment of account definitions to an identity, or by assignment of account definitions to departments, cost centers, locations, or business roles. All company identities can be allocated special account definitions independent of their affiliation to the departments, cost centers, locations, or business roles. It is possible to assign account definitions to the One Identity Manager as requestable items in the IT Shop. A department manager can then request user accounts from the Web Portal for his staff.
Handling of user accounts and identities during disabling
The handling of identity data, particularly during long-term or temporary absence of an identity, is dealt with differently in each company. Some companies never delete identity data, but just disable it when the identity leaves the company. Other companies delete the identity data but only after they are sure that all the user accounts have been deleted.
The requirements of a company’s user administration are often different not only in the existing target system types, but also in the individual target systems of a target system type. Even within a target system, there may be different rules for different user groups. For example, different rules for allocating user accounts can apply in the individual domains within an Active Directory environment.
A requirement could look like the following, for example:
-
In domain A, user accounts are administrated independently of identities.
-
In domain B, user accounts are linked to an identity. However, identity main data should not be transferred to the user accounts.
-
In domain C, a user account is automatically created for each internal identity. The information for the container, home server, and profile server are based on the identity's department and location.
In order to fulfill the individual requirements of user administration, users can be divided into categories:
-
Unlinked: The user account is not linked to an identity.
-
Linked: The user account is linked to an identity.
-
Linked configured (linked with configuration of the connection): The user accounts are linked to the identity. The effect of the link and the scope of the identity’s inherited properties on the user accounts can be configured through an account definition and its manage levels.
-
One Identity Manager supplies a default configuration with the manage levels:
-
Unmanaged: The user accounts are assigned to the identity, but do not have any further properties of that identity.
-
Full managed: The user accounts have an assignment to the identity and inherit the properties of the identities.
The following visual is designed to make user account transitions clearer. It shows the standard mechanisms for managing identities and user accounts integrated in One Identity Manager.
Figure 1: Transition states for a user account
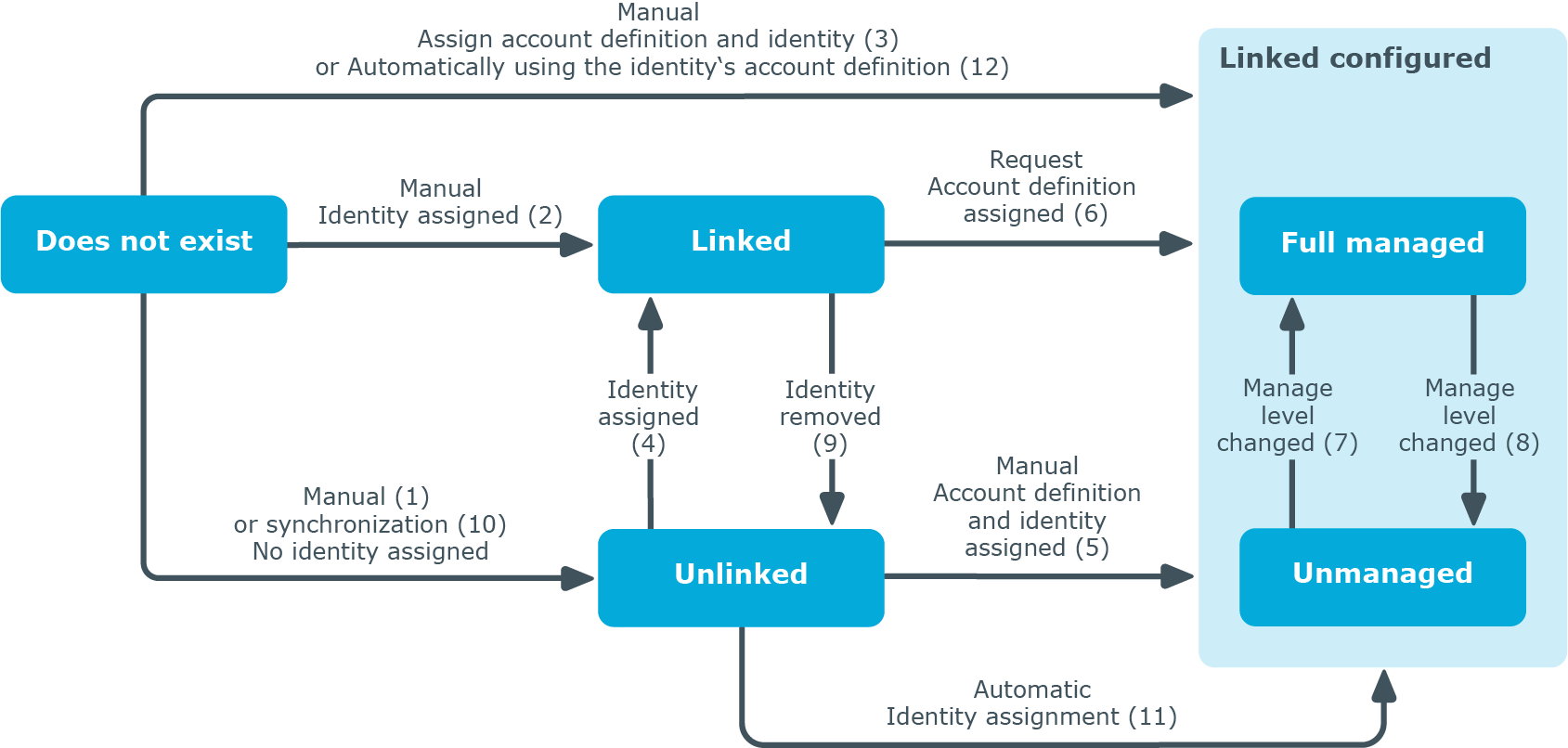
Manually adding a user account
-
Case 1: To manage a user account independently of identities, the user account is added manually and not assigned to an identity. The user account is not linked to an identity and therefore has the Unlinked state.
-
Case 2: If the user account is already linked to an identity when inserted manually, the user account changes its state to Linked.
-
Case 3: If an identity is already assigned when the user account is added and an account definition is assigned at the same time, the user account changes its state to Linked configured. Depending on the manage level used, the state becomes Linked configured: Unmanaged or Linked configured: Full managed.
Editing an existing user account
-
Case 4: If an existing user account is manually assigned to an identity, the user account changes its state from Unlinked to Linked.
-
Case 5: If an existing user account is manually assigned to an identity and an account definition is assigned at the same time, the user account changes its state from Unlinked to Linked configured. Depending on the manage level used, the state becomes Linked configured: Unmanaged or Linked configured: Full managed.
-
Case 6: When One Identity Manager goes live, you can create IT Shop requests for existing user accounts, which are linked with identities (Linked state). This assigns an account definition and the user account changes its state to Linked configured. Depending on the manage level used, the state becomes Linked configured: Unmanaged or Linked configured: Full managed.
Changing the manage level
Removing identity assignments
NOTE: The identity entry cannot be removed from user accounts with a state of Linked configured as long as the identity owns an account definition.
Handling user accounts during synchronization
-
Case 10: When a database is synchronized with a target system, the user accounts are always added without an associated identity and therefore, have an initial state of Unlinked. An identity can be assigned afterward. This can be done manually or through automated identity assignment using process handling.
Assigning identities automatically to existing user accounts
-
Case 11: One Identity Manager can automatically assign identities to user accounts in an Unlinked state. If the target system is assigned an account definition, this account definition is automatically assigned to the identities. Depending on the manage level used, the state becomes Linked configured: Unmanaged or Linked configured: Full managed. Automatic identity assignment can follow on from adding or updating user accounts through synchronization or through manually adding a user account. For more information, see Assigning identities automatically to user accounts.
Automatically creating user account through account definitions
-
Case 12: Account definitions are implemented to automatically assign user accounts to identities during normal working hours. If an identity does not have a user account in the target system, a new user account is created. This is done by assigning account definitions to an identity using the integrated inheritance mechanism followed by process handling. The manage level is modified to suit the default manage level and the user account has the Linked configured state. Depending on the manage level used, the state becomes Linked configured: Unmanaged or Linked configured: Full managed. For more information, see Account definitions and manage levels.
Removing user accounts
-
When an account definition assignment is removed from an identity, the associated user account is deleted.
-
Use the user account's Remove account definition task to reset the user account to Linked status. This removes the account definition from both the user account and the identity. The user account remains but is not managed by the account definition anymore. The task only removes account definitions that are directly assigned (XOrigin=1).
One Identity Manager has account definitions for automatically allocating user accounts to identities. You can create account definitions for every target system. If an identity does not yet have a user account in a target system, a new user account is created. This is done by assigning account definitions to an identity.
The data for the user accounts in the respective target system comes from the basic identity main data. The identities must have a central user account. The assignment of the IT operating data to the identity’s user account is controlled through the primary assignment of the identity to a location, a department, a cost center, or a business role. Processing is done through templates. There are predefined templates for determining the data required for user accounts included in the default installation. You can customize templates as required.

