If several target systems are managed using account definitions in a target system type, a separate account definition must be set up for each target system. When the identity is assigned both account definitions, subsequent script and process handling ensure that the identity obtains the user accounts in both target systems.
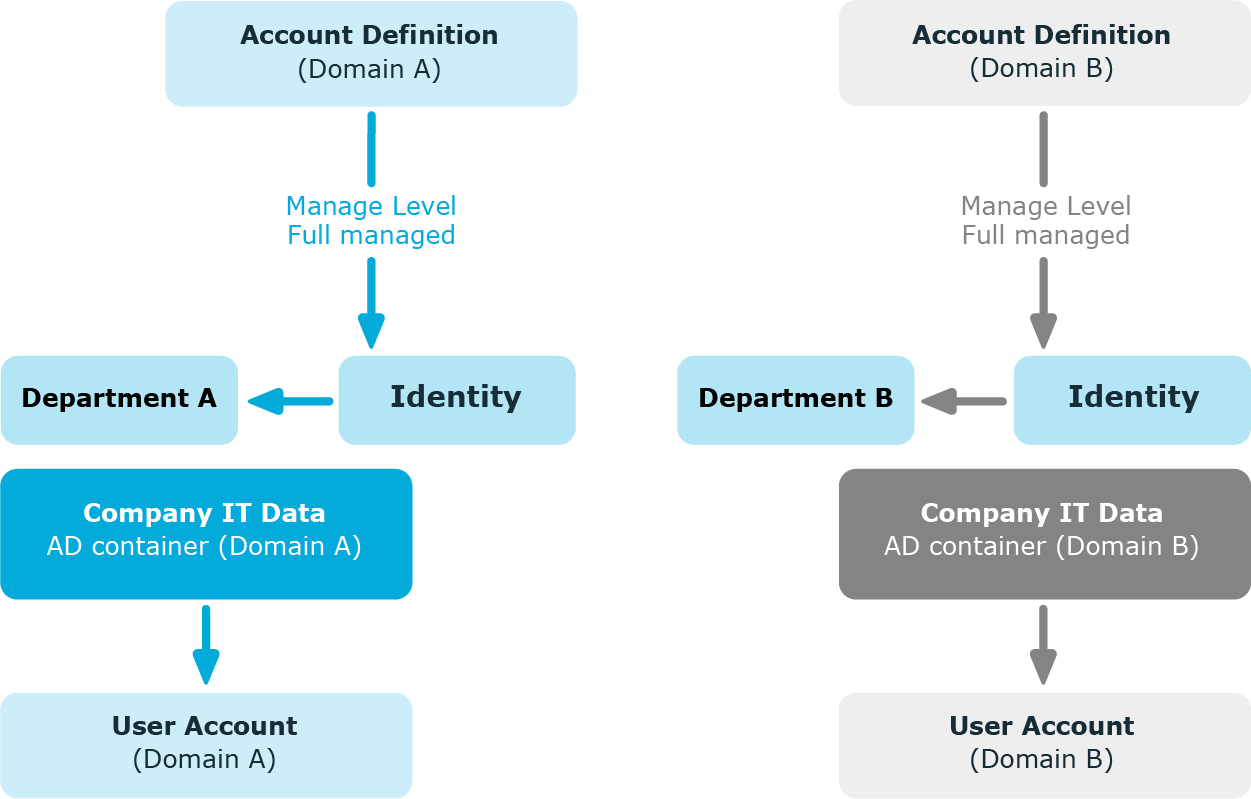
Example: Identities can have a user account only in one domain
There are two domains in an Active Directory environment. The identities can only have a user account in one of the domains. The department operational data is used to determine whether the user account is created in domain A or domain B.
Create an account definition A for domain A and an account definition B for domain B and assign them the Full managed manage level. This manage level uses the One Identity Manager default templates to determine the IT operating data. In the IT operating data mapping rule, specify the department property for both account definitions for finding the valid IT operating data.
If the identity belongs to department A, they receive (for example by dynamic assignment) the account definition A and as a result, a user account in domain A. If the identity belongs to department B, they are assigned the account definition B and they receive a user account in domain B.
Figure 3: Creating user accounts based on account definitions
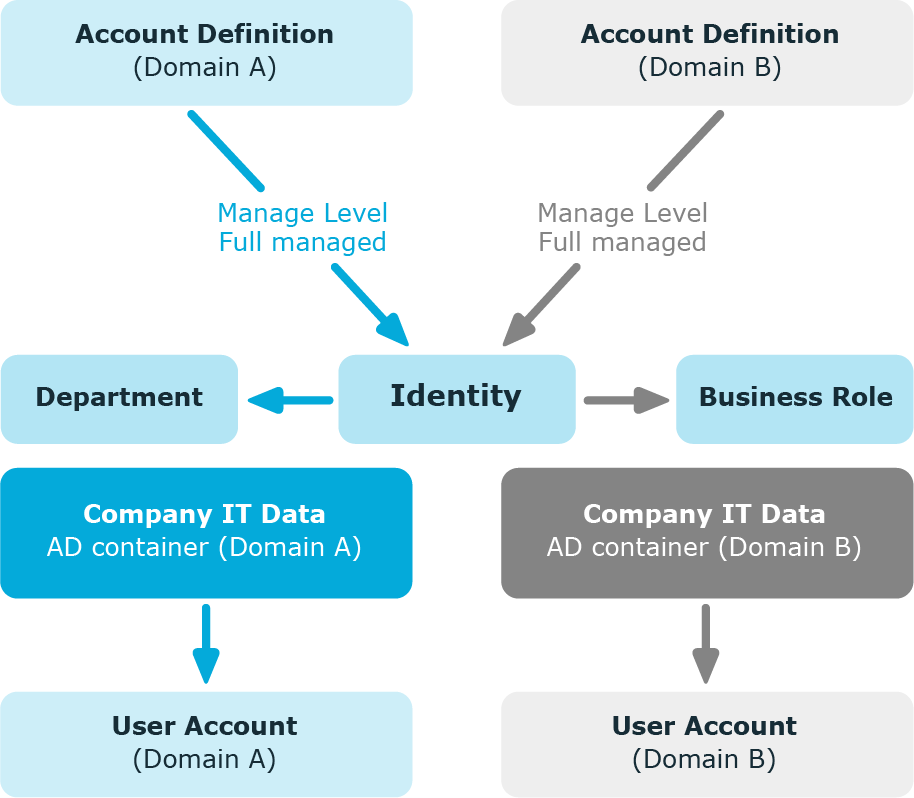
Example: Identities can have a user account in both domains
There are two domains in an Active Directory environment. The identities can have a user account in both of the domains. The user account in domain A is allocated IT operating data through the identity’s department. The user account in domain B is allocated IT operating data through the identity’s primary business role.
Create an account definition A for domain A and an account definition B for domain B and assign them the Full managed manage level. The Full managed manage level uses One Identity Manager default templates to determine the IT operating data. Specify the department property for account definition A in the IT operating data mapping rule for finding the valid IT operating data. Specify the property business role for account definition B in the IT operating data mapping rule for finding the valid IT operating data.
Figure 4: Creating user accounts based on account definitions
Automatic identity assignment is used to:
Through synchronization user accounts are initially loaded from the target system into One Identity Manager. Automatic assignment of user accounts to existing identities can take place by subsequently modifying scripts and processes. If necessary, new identities can be created based on existing user accounts to which they are then assigned. However, this is not the One Identity Manager default method. You can also use this procedure to create identity data from existing target system user accounts during synchronization.
If you run this procedure during working hours, automatic assignment of identities to user accounts takes place from that moment onwards. If you disable the procedure again later, the changes only affect user accounts added or updated after this point in time. Existing identity assignment to user accounts remain intact.
The criterion for automatically assigning identities to user accounts can be customized to meet the company’s needs. Identities can be directly assigned to existing user accounts as required, based on a suggestion list.
Run the following tasks to assign identities automatically.
-
In the Designer, set the configuration parameter for automatic assignment of identities to user accounts and select the required mode.
-
Define search criteria for the identity assignment.
-
If managed user accounts should arise through automatic identity assignment (Linked configured state), assign an account definition to the target system. Ensure that the manage level to be used is entered as the default manage level.
If no account definition is provided in the target system, the user accounts are only linked to the identity (Linked state). This is the case on initial synchronization, for example.
Related topics
In the One Identity Manager default installation, the automatic assignment of identities to user accounts is controlled by configuration parameters and therefore globally effective for a target system type. A distinction is made here between the synchronization and the default methods.
NOTE:
The following applies for synchronization:
- Automatic identity assignment takes effect if user accounts are added or updated.
The following applies outside synchronization:
- Automatic identity assignment takes effect if user accounts are added.
NOTE: The configuration parameters are included in the One Identity Manager modules and are available once the modules are installed.
Configuration parameters for automatic identity assignment:
Each configuration parameter has one of the permitted modes:
-
NO: There is no automatic assignment of an identity to the user account. This is the default value that is also displayed when the configuration parameter is not active.
-
SEARCH: If no identity is assigned to the user account, the system searches for the appropriate identity based on defined criteria and assigns the identities found to the user account. If an identity is not found, no new identity is added.
-
CREATE: If no identity is assigned to the user account, a new identity is always created, some properties are initialized, and the identity is assigned to the user account.
NOTE: This mode is not available for all target system types.
-
SEARCH AND CREATE: If no identity is assigned to the user account, the system searches for the appropriate identity based on defined criteria and assigns the identities found to the user account. If no identity is found, a new one is added, some of the properties are initialized, and the identity is assigned to the user account.
NOTE: This mode is not available for all target system types.
If a user account is linked to an identity through the current mode, the user account is given, through an internal process, the default manage level of the account definition entered in the user account's target system. You can change this manage level later.
NOTE:
In the default installation, after synchronizing, identities are automatically created for the user accounts. If an account definition for the target system is not known at the time of synchronization, user accounts are linked with identities. However, account definitions are not assigned. The user accounts are therefore in a Linked state.
To manage the user accounts using account definitions, assign an account definition and a manage level to these user accounts.
To manage user accounts through account definitions
-
Create an account definition.
-
Assign a user account in the Linked state to the account definition. The account definition's default manage level is applied to the user account.
-
In the Manager, select the category <target system type> > User accounts > Linked but not configured > <target system>.
-
Select the Assign account definition to linked accounts task.
-
In the Account definition menu, select the account definition.
-
Select the user accounts that contain the account definition.
-
Save the changes.
In the target system-dependent Insert/Update processes of the One Identity Manager default installation, the configuration parameters are evaluated and the implementation mode is determined. The names of the corresponding process steps are Search and Create Person for Account and Search and Create Person for Account (Fullsync). Process steps can be used as templates to put into effect the automatic identity assignment in different areas of a target system, such as, the separate domains of an Active Directory environment.
The criteria for identity assignments are defined for the target system. You specify which user account properties must match the identity’s properties such that the identity can be assigned to the user account. You can limit search criteria further by using format definitions.
The search criterion is written in XML notation to the Search criteria for automatic identity assignment column (AccountToPersonMatchingRule) in the target system table.
Search criteria are evaluated when identities are automatically assigned to user accounts. Furthermore, you can create a suggestion list for assignments of identities to user accounts based on the search criteria and make the assignment directly.
NOTE: Object definitions for user accounts that can have search criteria applied to them are predefined. For example, if you require other objects definitions that limit a preselection of user accounts, set up the respective custom object definitions in the Designer. For more information, see the One Identity Manager Configuration Guide.
Detailed information about this topic


