SAP authorizations are only checked on the basis of active SAP functions. When you enable the working copy, the changes are transferred to the function definition. An active function definition is added to a new working copy.
To transfer changes from a working copy to a function definition
-
In the Manager, select the Identity Audit > SAP functions > Function definition working copies category.
-
Select the function definition in the result list.
-
Select the Enable working copy task.
-
Confirm the security prompt with OK.
Related topics
SAP authorizations are verified on the basis of the SAP applications permitted for an SAP user account and the associated authorization objects. To determine whether potentially dangerous authorizations are assigned within the company, define SAP functions that group together the SAP applications and authorization objects to be checked. One Identity Manager compares all authorization objects assigned to single profiles with the authorization definition in the SAP function. This way, it determines all SAP roles and profiles that have exactly these authorization objects assigned via the sum of their single profiles.
The TargetSystem | SAPR3 | SAPRights | TestWithoutTCD configuration parameter is evaluated by authorization checks. The configuration parameter specifies whether SAP application are ignored and only authorization objects taken into account during the authorization check.
The TestWithoutTCD configuration parameter is not set (default)
The following rules apply to the authorization check:
An SAP role or SAP profile matches an SAP function when
-
It has at least one of the SAP applications defined in the SAP function.
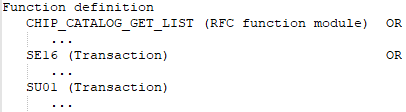
-
It has all the authorization objects of this SAP application that are defined in the SAP function.
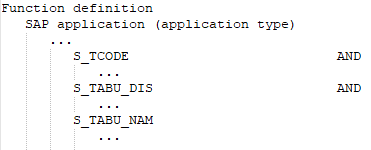
-
It has all the different function elements of an authorization object that are defined in the SAP function.
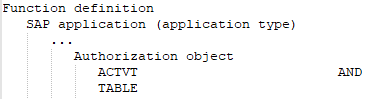
-
At least one or all of the values of one and the same function element defined in the SAP function are available.
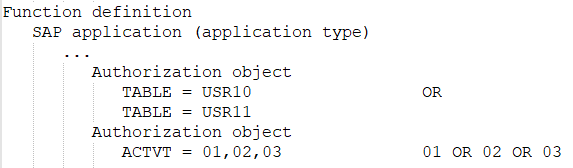
An SAP role matches an SAP function if an SAP profile of this SAP role matches the SAP function.
An SAP profile matches an SAP function if it contains at least one of the SAP applications defined in the SAP function. The SAP profile must have all this SAP application's authorization objects to do this. If a function element with different values is defined for an authorization object, the SAP profile matches the SAP function if it has at least one of these values.
The TestWithoutTCD configuration parameter is set
SAP applications are not taken into account during the authorization check. The following rules apply to the authorization check:
An SAP role or SAP profile matches an SAP function when
-
It has all the authorization objects of all SAP applications defined in the SAP function,
except for the authorization objects needed to identify the SAP applications.
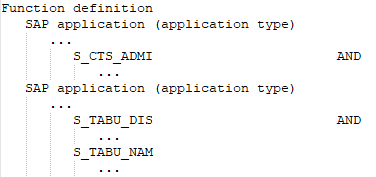
-
It has all the different function elements of an authorization object that are defined in the SAP function.
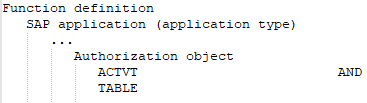
-
At least one or all of the values of one and the same function element defined in the SAP function are available.
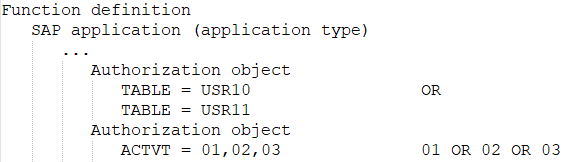
Only the authorization objects and their values are of interest for the authorization check. It is irrelevant to which SAP applications these authorization objects belong. That means the authorization objects that are only used to identify the applications are ignored. The following authorization objects and function elements are therefore disregarded:
-
External service: S_SERVICE with SRV_NAME and SRV_TYPE
-
TADIR object: S_START with AUTHOBJNAM, AUTHOBJTYP, and AUTHPGMID
-
RFC function module: S_RFC with RFC_NAME and RFC_TYPE
-
Transaction: S_TCODE with TCD
Examples of authorization checking
An SAP function is defined with the following SAP applications, authorization objects, and function elements.
Figure 3: Authorization definition with transactions
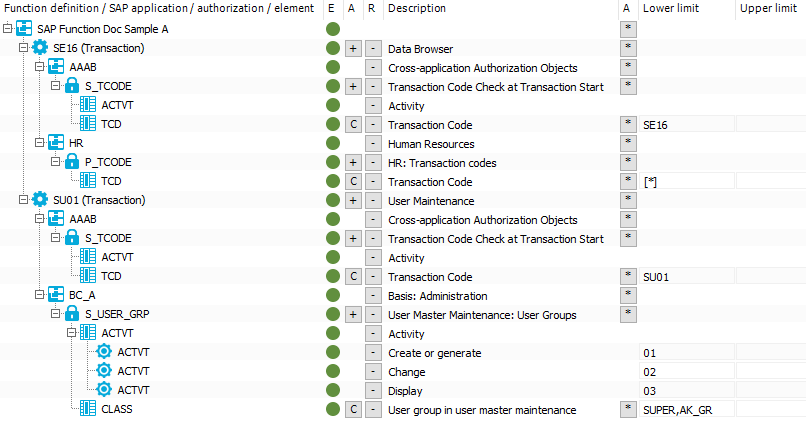
If the configuration parameter is not set, all SAP roles and SAP profiles with the authorizations found by the SAP function shown are listed here:
SAP application SE16 with:
Authorization object S_TCODE with
Function element ACTVT
AND
Function element TCD with the value SE16
AND
Authorization object P_TCODE with
Function element TCD with exactly the value *
OR
SAP application SU01 with:
Authorization object S_TCODE with
Function element ACTVT
AND
Function element TCD with at least the value SU01
AND
Authorization object S_USER_GRP with
Function element ACTVT with at least one of the values 01 OR 02 OR 03
AND
Function element CLASS with at least one of the values SUPER OR AK_GR
If the configuration parameter is set, all SAP roles and SAP profiles with the authorizations found by the SAP function are listed here:
Authorization object P_TCODE with
Function element TCD with exactly the value *
AND
Authorization object S_USER_GRP with
Function element ACTVT with at least one of the values 01 OR 02 OR 03
AND
Function element CLASS with at least one of the values SUPER OR AK_GR
The following function definition contains various SAP applications with different application types.
Figure 4: Authorization definition with different application types
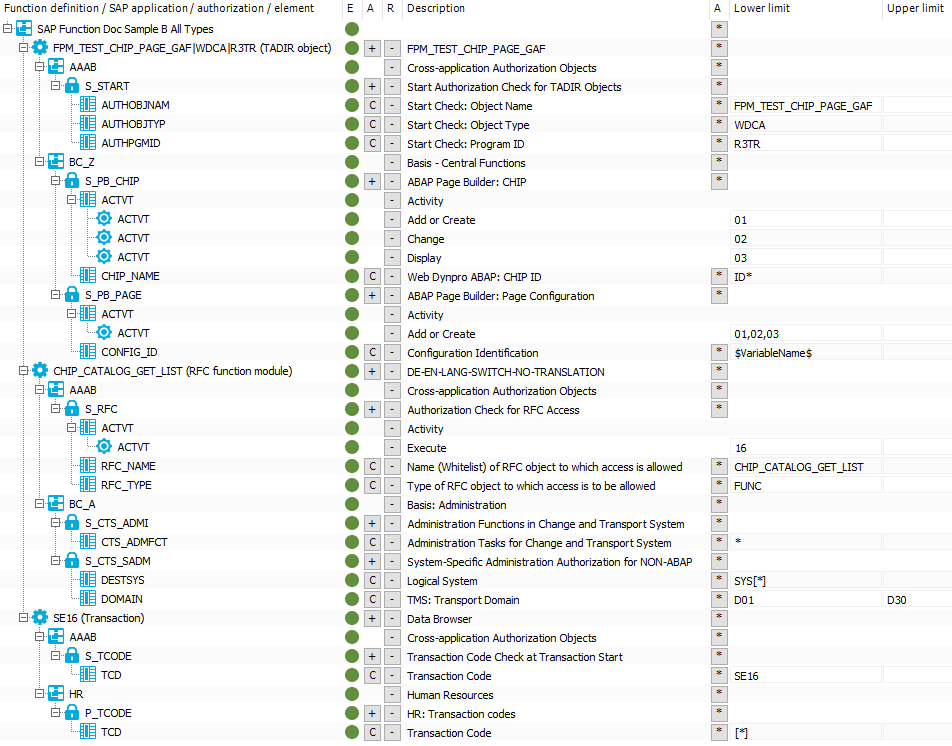
If the configuration parameter is set and without taking the SAP applications into account, the SAP function shown will determine all SAP roles and SAP profiles that have the following authorizations:
Authorization object S_PB_CHIP with
Function element ACTVT with at least one of the values 01 OR 02 OR 03
AND
Function element CHIP_NAME with an value that starts with ID
AND
Authorization object S_PB_PAGE with
Function element ACTVT with at least one of the values 01 OR 02 OR 03
AND
Function element CONFIG_ID with the instance that is specified as a value in the $VariableName$ variable
AND
Authorization object S_CTS_ADMI with
Function element CTS_ADMFCT with any value
AND
Authorization object S_CTS_SADM with
Function element DESTSYS with at least the value of exactly SYS*
AND
Function element DOMAIN with at least one value in a range from D01 to D30
AND
Authorization object P_TCODE with
Function element TCD with exactly the value *
If the configuration parameter is not set, the SAP function shown will determine all SAP roles and SAP profiles with the authorizations. The evaluation at the level of the function elements is identical to the evaluation when the configuration parameter is set and is therefore not shown again.
SAP application FPM_TEST_CHIP_PAGE_GAF with:
Authorization object S_START
AND
Authorization object S_PB_CHIP
AND
Authorization object S_PB_PAGE
OR
SAP application CHIP_CATALOG_GET_LIST with:
Authorization object S_RFC
AND
Authorization object S_CTS_ADMI
AND
Authorization object S_CTS_SADM
OR
SAP application SE16 with:
Authorization object S_TCODE
AND
Authorization object P_TCODE
Related topics
If you create an authorization definition, you need to think about which authorization combinations are not compliant. You can differentiate between two use cases:
-
Find all SAP roles and profiles with invalid combinations of authorizations.
Create an SAP function for authorizations that cannot occur together with an SAP role or an SAP profile. The authorization check identifies all SAP roles and profiles whose authorizations in total have this invalid combination of authorizations.
-
Find all identities that have obtain invalid combinations of authorizations through their SAP user accounts.
Create different SAP functions for authorizations that in combination are invalid. Create compliance rules that combine these SAP functions. The compliance check finds all identities that have such invalid authorization combinations over the sum of all authorizations of their SAP user accounts.
Example for use case 1
A company has changed its policies on compliant SAP authorizations. Now the new policies must be checked to see if existing authorizations comply. SAP roles and profiles with invalid combinations of authorizations must be identified so that they can be modified to meet the new requirements.
An SAP function is created for each invalid authorization combination.
Table 6: Example of an authorization definition
|
F-A |
TR1 |
AO2 |
ACTVT |
* |
|
TR1 |
AO2 |
Class |
* |
|
TR1 |
AO3 |
ACTVT |
02 |
|
TR1 |
S_TCODE |
TCD |
TR1 |
|
RF |
AO5 |
ACTVT |
* |
|
RF |
AO5 |
RLTYP |
R* |
|
RF |
S_RFC |
RFC_NAME |
RF |
|
F-B |
TR1 |
AO3 |
ACTVT |
* |
|
TR1 |
AO4 |
ACTVT |
02,03,07 |
|
TR1 |
AO4 |
Class |
DEF[*] |
|
TR1 |
S_TCODE |
TCD |
TR1 |
The following SAP profiles are available:
Table 7: Defined SAP profiles
|
P1 |
TR1 |
AO1 |
ACTVT |
* |
|
TR1 |
AO1 |
Class |
* |
|
TR1 |
AO3 |
ACTVT |
* |
|
TR1 |
AO4 |
ACTVT |
01, 02 |
|
TR1 |
AO4 |
Class |
DEF* |
|
TR1 |
S_TCODE |
TCD |
TR1 |
|
P2 |
TR1 |
AO2 |
ACTVT |
* |
|
TR1 |
AO2 |
Class |
* |
|
TR1 |
AO3 |
ACTVT |
01 |
|
TR1 |
S_TCODE |
TCD |
TR1 |
|
P3 |
TR1 |
AO3 |
ACTVT |
01, 02 |
|
TR1 |
AO4 |
Class |
* |
|
TR1 |
AO4 |
ACTVT |
03, 07 |
|
P4 |
RF |
AO5 |
ACTVT |
03 |
|
RF |
AO5 |
RLTYP |
* |
|
RF |
S_RFC |
RFC_NAME |
RF |
SAP profiles are found that match the SAP function during authorization checking.
Results of the authorization check: TestWithoutTCD is not set.
-
SAP function: F-A
SAP profile affected: P4
The profile P4 has all the authorization objects, fields, and values named in SAP application RF.
The profile P1 is missing authorization objects AO2, S_TCODE, AO5, and S_RFC. Therefore it does not match the SAP function.
The profile P2 is missing the value 02 for the authorization object AO3 as well as the authorization objects AO5 and S_RFC. Therefore it does not match the SAP function.
The profile P3 is missing authorization objects AO2, S_TCODE, AO5, and S_RFC. Therefore it does not match the SAP function.
-
SAP function: F-B
SAP profile affected: P1
The profile P1 has all the authorization objects and fields named in the SAP function and at least one of the values.
The profile P2 is missing authorization object AO4. Therefore it does not match the SAP function.
The profile P3 is missing authorization object S_TCODE. Therefore it does not match the SAP function.
Profile P4 is missing the authorization objects AO3, AO4, and S_TCODE. Therefore it does not match the SAP function.
If the TestWithoutTCD configuration parameter is set for authorization checking, then the SAP profiles P2 and P3 comply with the new guidelines and can continue to be used. The profiles P1 and P4 must be modified to comply with the new policies.
Results of the authorization check: TestWithoutTCD is set.
-
SAP function: F-A
The authorization objects S_TCODE and S_RFC are ignored during the check.
SAP profile affected: none
The profile P1 is missing authorization objects AO2 and AO5. Therefore it does not match the SAP function.
Profile P2 is missing authorization object AO5 and value 02 for authorization object AO3. Therefore it does not match the SAP function.
The profile P3 is missing authorization objects AO2 and AO5. Therefore it does not match the SAP function.
The profile P4 is missing authorization objects AO2 and AO3. Therefore it does not match the SAP function.
-
SAP function: F-B
The authorization object S_TCODE is ignored during the check.
SAP profiles affected: P1, P3
The profile P1 has all the authorization objects and fields named in the SAP function and at least one of the values.
The profile P3 has all the authorization objects and fields named in the SAP function and at least one of the values.
The profile P2 is missing authorization object AO4. Therefore it does not match the SAP function.
The profile P4 is missing authorization objects AO3 and AO4. Therefore it does not match the SAP function.
If the TestWithoutTCD configuration parameter is set for authorization checking, then the SAP profiles P2 and P4 comply with the new guidelines and can continue to be used. The P1 and P3 profiles must be adjusted.
Example for use case 2
SAP user accounts must be checked for guidelines violations. The following user accounts and identities are available:
-
User A with user account AC1 with the SAP profile P1
-
User B with user account AC2 with the SAP profiles P2 and P3
-
User C with user account AC3 with the SAP profile P2 and user account AC4 with the SAP profile P3
The SAP profiles have the following authorizations:
-
P1 with AO1 and AO2
-
P2 with AO1
-
P3 with AO2
An identity cannot have the two authorizations AO1 and AO2 at the same time. The SAP function SF-A is created for the check. A compliance rule CR-X finds all identities that match this SAP function.
Only the SAP profile P1 matches the SAP function. Therefore, the compliance rule finds a rule violation for just User A. To ensure that the combination of the SAP profiles P2 and P3 is also recognized as invalid, additional SAP functions and compliance rules must be created.
The SAP profiles P1 and P2 match the SAP function SF-B. The SAP profiles P1 and P3 match the SAP function SF-C. Thus, the compliance rule CR-Y can be used to determine all identities who are assigned the SAP profiles P1 or P2 and P3 though their user accounts and therefore have both authorizations AO1 and AO2.
Table 8: Result of the rule check
|
CR-X |
The identity has at least the SAP function SF-A. |
User A |
|
CR-Y |
The identity has at least the SAP function SF-B AND they have at least the SAP function SF-C. |
User A
User B
User C |
Related topics
A working copy is added to the database for every function definition. You can edit the working copies to change the function definitions. The changes are not passed on to the production function definition until the working copy is enabled. SAP authorizations are only checked on the basis of active function definitions.
NOTE: One Identity Manager users with the Identity & Access Governance | Identity Audit | Maintain SAP functions application role can edit existing working copies if they are entered as the manager in the main data.
To edit an existing function definition
-
In the Manager, select the Identity Audit > SAP functions > Function definitions category.
-
Select the function definition in the result list.
-
Select the Create working copy task.
The data from the existing working copy are overwritten with the data from the active function definition, after prompting. The working copy is opened and can be edited.
- OR -
In the Manager, select the Identity Audit > SAP functions > Function definition working copies category.
-
Select a working copy in the result list.
-
Select the Change main data task.
-
Edit the working copy's main data.
- Save the changes.
-
Select the Enable working copy task and confirm the security prompt with Yes.
The changes to the working copy are transferred to the active function definition.
Related topics









