Security Analytics Engine Overview
Security Analytics Engine Overview
Topics:
Introduction to the Security Analytics Engine
Introduction to the Security Analytics Engine
The Security Analytics Engine is used by applications for adaptive authorization. By using risk policies, an application is able to customize their authorization requirements to better minimize the risk of a malicious user gaining access to the application.
In some instances, a legitimate user will receive a risk score that blocks their access to an application (for example, due to a business trip outside their normal geographic location). In these cases, the user can contact a help desk operator to get a temporary override.
How the Security Analytics Engine works
How the Security Analytics Engine works
When a user attempts to access an application which uses the Security Analytics Engine, a customizable risk policy evaluates the risk of allowing the user access. Each risk policy is made up of conditions and modifiers which have assigned scores. For each access attempt, these conditions and their associated modifiers are evaluated individually, and a single risk score is then calculated using all the condition scores.
For example, a user could log in to an application using an abnormal browser while also using a weak method of authentication. The risk policies allow you to take these two types of behavior into account by letting you apply modifiers to conditions in cases where additional circumstances may affect the risk from a triggered condition. The conditions are assigned a condition score and the modifiers are then able to increase or lessen that condition score if they are triggered at the same time. So in this case, by triggering both the abnormal browser condition and its associated weak authentication modifier, the configured condition score is further increased due to the modifier.
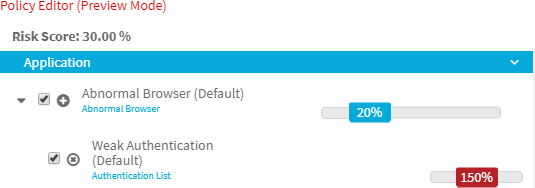
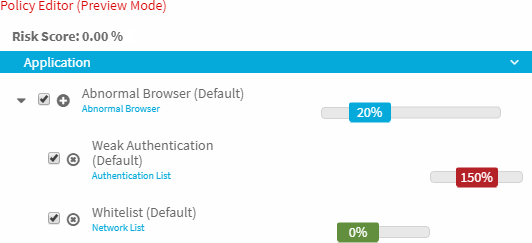
A condition can also have no impact on a risk score when triggered if there is a modifier applied which is configured to cancel out the condition score. If the user using an abnormal browser is also on a configured whitelist, the whitelist modifier could be applied to have a zeroing effect on both the condition it is associated with and any other modifiers that are also triggered. Assuming no other conditions are triggered, this example would cause a risk score of 0 for the access attempt.
The Security Analytics Engine also allows you to include conditions without modifiers associated with them. For example, the earlier access attempts probably would not be as much of a security threat as someone that logs in from an IP address that is associated with malware. Configuring a risk policy to give the highest risk score to potential malware infected access attempts means that even if the user appears on a whitelist being used as a modifier to negate a different condition they would still receive the highest risk score.
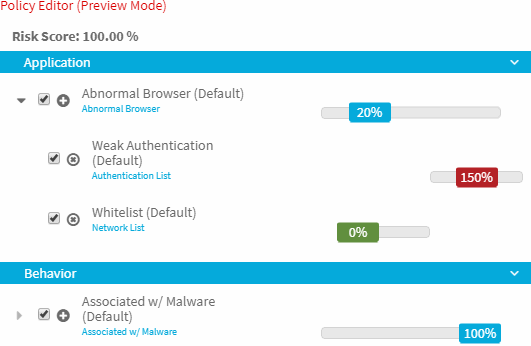
The risk score that is calculated for each access attempt is then sent to the application which uses the risk score to determine whether to allow access, request additional authentication information from the user before allowing access, or deny access. A user may also contact a help desk operator for further assistance if they are unable to access an application due to a high risk score.
Launch the Administration web site
When the Security Analytics Engine is bundled with another product (for example, Cloud Access Manager), the Security Analytics Engine should be accessed through the parent product. See the documentation associated with the main product for information on accessing the Security Analytics Engine.
