Data Governance Edition reports
One Identity Manager Data Governance Edition includes reports to help you identify, summarize, and analyze resource and account access and activity throughout your organization. The reports detailed in this section refer specifically to those that help you to secure the unstructured NTFS and SharePoint data within your enterprise and implement data ownership.
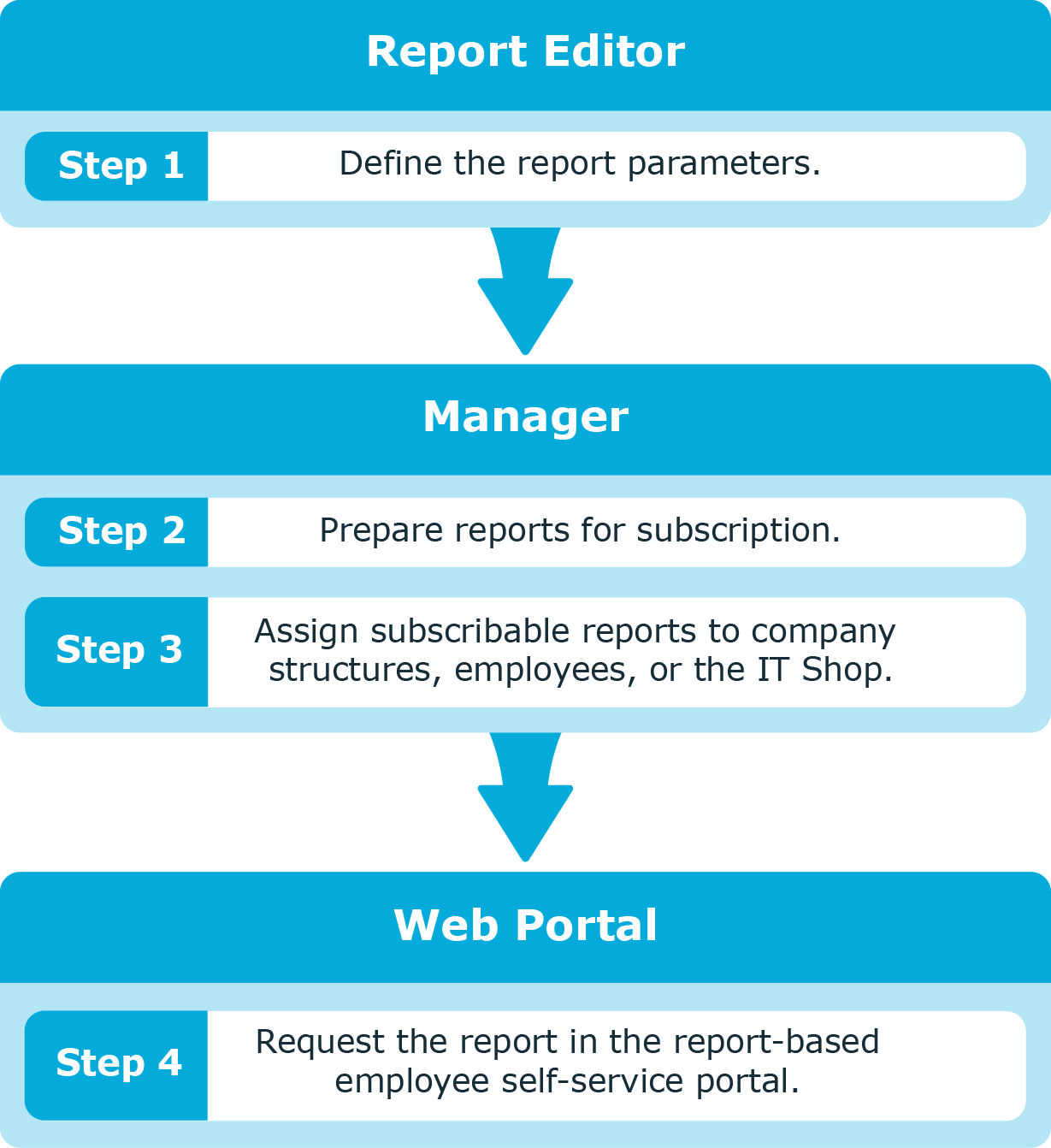
The following components function together to provide the reports and information to administrators and ultimately the business owners, compliance officers, and managers, through the web portal.
- Report Editor
From here, you can create and edit reports. During report creation, you specify which parameters are visible and can be overwritten and which are pre-populated from the data source.
Note: Data Governance Edition reports are pre-defined default reports delivered with One Identity Manager, and as such, they cannot be edited. However, if they do not suit your needs, you can create a report based on the default by copying it, and entering the required parameters in the Edit report dialog.
For details on working with the Report Editor, see Reports in One Identity Manager in the One Identity Manager Configuration Guide.
- Manager
From here, you prepare reports for subscription, customize the report parameters (specify the parameters that are available and can be overwritten by web portal users), setup email notifications, and publish reports to the IT Shop.
For details on making reports available within the web portal, see the One Identity Manager Report Subscriptions Administration Guide.
- Web Portal
From here, employees can request access to and view subscribed Data Governance Edition reports that pertain to resources, accounts, and group membership.
Web portal users can customize the report to suit their needs. For details on accessing and viewing reports within the IT Shop, see Report Subscriptions in the One Identity Manager Web Portal User Guide.
Important: In order to process Data Governance Edition report requests from the web portal, a One Identity Manager service (job server) must be running as an account that is able to access the Data Governance server (that is, either a Data Governance service account or an account mapped to an employee with the Data Governance | Administrators or Data Governance | Access Managers application role).
The job servers that host these One Identity Manager services must be marked in the database with the Data Governance connector flag using the job server editor in the Designer application. (Specifically, in the Designer, select Base Data | Installation | Job server | Server functions.)
Figure 3: Reporting workflow
The following reports are provided to help you in your data governance endeavors:
Data ownership reports (requires resource activity collection)
Access reports
Activity reports (requires resource activity collection)
Group membership reports
Rights and identities report
Through ongoing data governance activities, the assignment of ownership to unstructured data will, over time, improve the overall health of your network.
This report displays all the resources on Windows File Servers, SharePoint farms, supported NAS devices and Cloud managed hosts, their location (network path), and where the current data owners (those that have been assigned a business owner) differ from the perceived owner. Perceived owner is calculated on historical resource activity or security information for the selected resource.
This is a companion report to the “perceived owner calculation” feature in the Manager where you can compute if the current perceived owner is different than the designated business owner. For more information, see Calculating perceived owner.. This report is useful for continuous compliance by identifying cases where the perceived owner should be designated the business owner due to changed responsibilities.
Compliance officers and administrators can run this report for the entire enterprise to ensure that the data is owned by the appropriate user — the user who understands the content and can attest to the list of authorized users. This should be consistently monitored to ensure that the proper user has control over the resources.

