An account definition specifies which rules are used to form the IT operating data and which default values will be used if no IT operating data can be found through the identity's primary roles.
Account definitions can be created for each target system of the appointed target system type, for example, the different domains of an Active Directory environment or the individual clients of an SAP R/3 system. An account definition is always valid for a target system. You can, however, define several account definitions for one target system. Which account definition will be used is decided when creating an identity's user account. To ensure that a Microsoft Exchange mailbox, for example, is not created until an Active Directory user account exists, you can define dependencies between account definitions.
The manage levels that may be used are specified in the account definition. You can create more than one manage level. The manage level determines the scope of the properties that an identity's user account can inherit. This allows an identity to have several user accounts in one target system, for example:
One Identity Manager supplies a default configuration for manage levels:
-
Unmanaged: User accounts with the Unmanaged manage level are linked to the identity but they do no inherit any further properties. When a new user account is added with this manage level and an identity is assigned, some of the identity's properties are transferred initially. If the identity properties are changed at a later date, the changes are not passed onto the user account.
-
Full managed: User accounts with the Full managed manage level inherit defined properties of the assigned identity. When a new user account is created with this manage level and an identity is assigned, the identity's properties are transferred in an initial state. If the identity properties are changed at a later date, the changes are passed onto the user account.
NOTE: The Full managed and Unmanaged manage levels are analyzed in templates. You can customize the supplied templates in the Designer.
You can define other manage levels depending on your requirements. You need to amend the templates to include manage level approaches.
A default manage level is defined for every account definition. This manage level is used to determined the valid IT operating data when a user account is created automatically. In the One Identity Manager default installation, the processes are checked at the start to see if the identity already has a user account in the target system that has an account definition. If no user account exists, a new user account is created with the account definition’s default manage level.
NOTE: If a user account already exists and is disabled, then it is re-enabled. You have to alter the user account manage level afterward in this case.
The effects on account definition inheritance of temporary disabling, permanent disabling, deletion, and security risk to identities is specified for each account definition.
-
As long as an account definition applies to an identity, this identity keeps its linked user accounts. You may want identities that are disabled or marked for deletion to inherit account definitions to ensure that all necessary permissions are made immediately available when the identity is reactivated at a later time.
-
If the account definition assignment no longer applies or is removed from the identity, the user account created through this account definition, is deleted.
-
User accounts marked as Outstanding will only be deleted if the QER | Person | User | DeleteOptions | DeleteOutstanding configuration parameter is set.
In addition, you can specify the effect of temporarily or permanently disabling, deleting, or the security risk of an identity on its user accounts and group memberships for each manage level.
-
Identity user accounts can be locked when they are disabled, deleted, or rated as a security risk so that permissions are immediately withdrawn. If the identity is reinstated at a later date, the user accounts are also reactivated.
-
You can also define group membership inheritance. Inheritance can be discontinued if desired when, for example, the identity’s user accounts are disabled and therefore cannot be members in groups. During this time, no inheritance processes should be calculated for this identity. Existing group memberships are deleted.
Related topics
Account definitions are assigned to company identities.
Indirect assignment is the default method for assigning account definitions to identities. Account definitions are assigned to departments, cost centers, locations, or roles. The identities are categorized into these departments, cost centers, locations, or roles depending on their function in the company and thus obtain their account definitions. To react quickly to special requests, you can assign individual account definitions directly to identities.
You can automatically assign special account definitions to all company identities. It is possible to assign account definitions to the IT Shop as requestable products. Department managers can then request user accounts from the Web Portal for their staff. It is also possible to add account definitions to system roles. These system roles can be assigned to identities through hierarchical roles or added directly to the IT Shop as products.
To create user accounts for an identity with the Full managed manage level, you need to know which IT operating data is required. The operating data required for each specific target system is defined with its business roles, departments, locations, or cost centers. An identity is assigned a primary business role, primary location, primary department, or primary cost center. The necessary IT operating data is ascertained from these assignments and used in creating the user accounts. Default values are used if valid IT operating data cannot be found over the primary roles.
The process sequence for automatically assigning IT operating data to the identity’s user account within the One Identity Manager should be made clearer with the help of the following diagram.
Figure 2: Mapping IT operating data to a user account
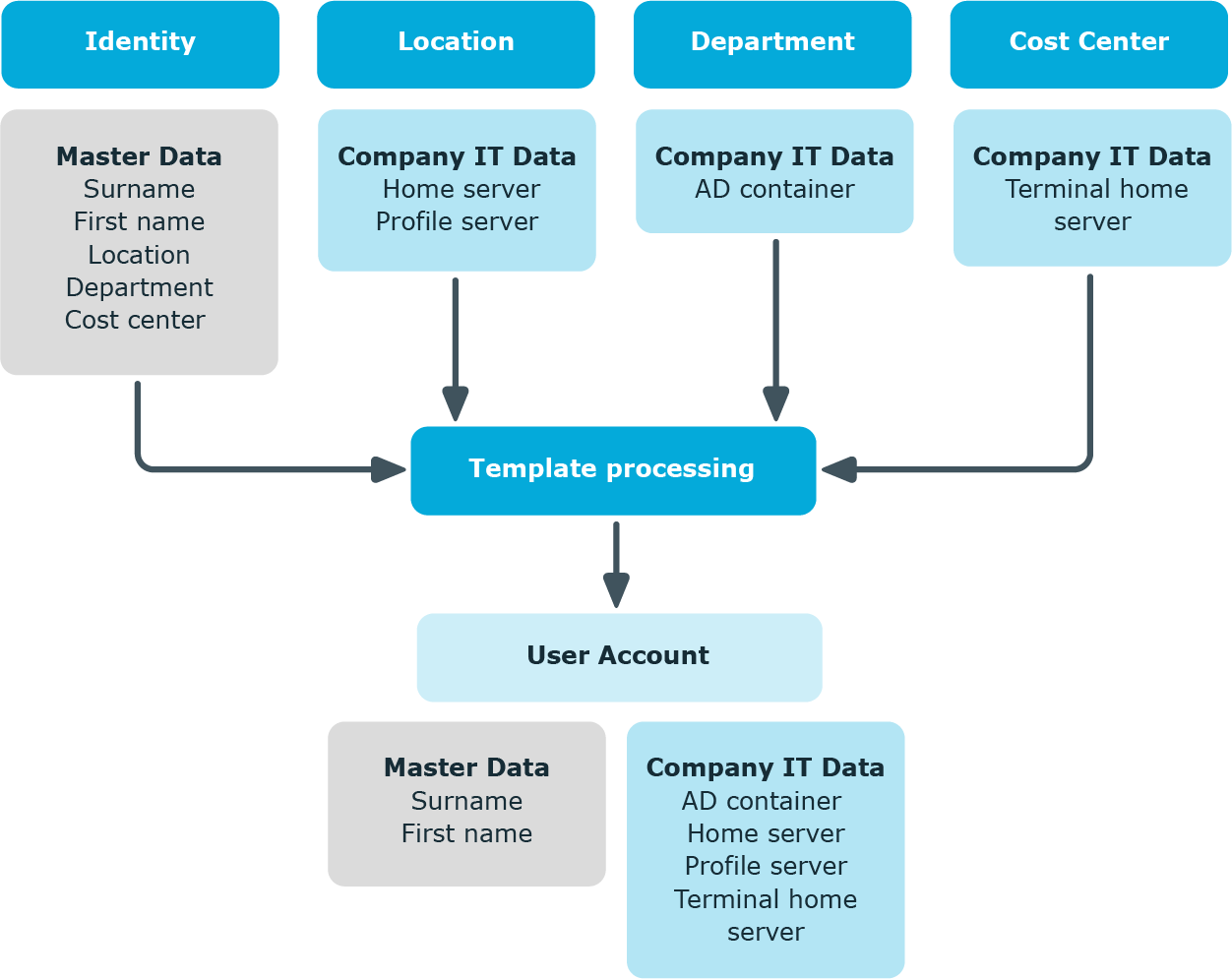
You can also specify IT operating data directly for a specific account definition.
Example:
Normally, each identity in department A obtains a default user account in the domain A. In addition, certain identities in department A obtain administrative user accounts in the domain A.
Create an account definition A for the default user account of the domain A and an account definition B for the administrative user account of domain A. In the IT operating data mapping rule for the account definitions A and B, specify the Department property in order to determine the valid IT operating data.
Specify the effective IT operating data of department A for the domain A. This IT operating data is used for standard user accounts. In addition, for department A, specify the effective IT operating data of account definition B. This IT operating data is used for administrative user accounts.
The IT operating data necessary in the One Identity Manager default configuration for automatically creating or changing identity user accounts and mailboxes in the target system is itemized in the following table.
NOTE: IT operating data is dependent on the target system and is contained in One Identity Manager modules. The data is not available until the modules are installed.
Table 1: Target system dependent IT operating data
|
Active Directory |
Container
Home server
Profile server
Terminal home server
Terminal profile server
Groups can be inherited
Identity type
Privileged user account |
|
Microsoft Exchange |
Mailbox database |
|
LDAP |
Container
Groups can be inherited
Identity type
Privileged user account |
|
Domino |
Server
Certificate
Template for mail file
Identity type |
|
SharePoint |
Authentication mode
Groups can be inherited
Roles can be inherited
Identity type
Privileged user account |
|
SharePoint Online |
Groups can be inherited
Roles can be inherited
Privileged user account.
Authentication mode |
|
Custom target systems |
Container (per target system)
Groups can be inherited
Identity type
Privileged user account |
|
Azure Active Directory |
Groups can be inherited
Administrator roles can be inherited
Subscriptions can be inherited
Disabled service plans can be inherited
Identity type
Privileged user account
Change password at next login |
|
Cloud target system |
Container (per target system)
Groups can be inherited
Identity type
Privileged user account |
|
Unix-based target system |
Login shell
Groups can be inherited
Identity type
Privileged user account |
|
Oracle E-Business Suite |
Identity type
Groups can be inherited
Privileged user account. |
|
SAP R/3 |
Identity type
Groups can be inherited
Roles can be inherited
Profiles can be inherited
Structural profiles can be inherited
Privileged user account. |
|
Exchange Online |
Groups can be inherited |
|
Privileged Account Management |
Authentication provider
Groups can be inherited
Identity type
Privileged user account |
|
Google Workspace |
Organization
Groups can be inherited
Products and SKUs can be inherited
Admin roles assignments can be inherited
Identity type
Privileged user account.
Change password at next login |
|
OneLogin |
Roles can be inherited
Identity type
Privileged user account.
Licensing state
OneLogin group |

