New features between SPS 5.1 and 5.11 - integration and plugins
Join to Starling
You can now join SPS to One Identity Starling. One Identity Starling helps to combine products from the One Identity line to create a secure and customizable cloud service. For details on One Identity Starling, see Starling - Technical Documentation.
For more information, see "Joining to One Identity Starling" in the Administration Guide.
SIEM forwarder
You can now forward the log messages and events related to what happens in the privileged sessions to an external SIEM, such as Splunk or Arcsight, or other third-party systems that enable you to search, analyze, and visualize the forwarded data. SPS can send these events as industry-standard RFC3164 syslog messages, with the data formatted either as JSON or in Common Event Format (CEF).
For more information, see "Using the universal SIEM forwarder" in the Administration Guide.
Enhancements to Credential Store plugin for One Identity Safeguard for Privileged Passwords
The Credential Store plugin for One Identity Safeguard for Privileged Passwords now supports connecting to a cluster of One Identity Safeguard servers. In addition, it is now possible to resolve the IP addresses of target servers to hostnames, and to expand domain names to full domain names when not provided in their FQDN form. For details, see How to connect One Identity Safeguard for Privileged Passwords with One Identity Safeguard for Privileged Sessions.
Integrate with One Identity Total Privileged Access Management (TPAM)
An official plugin is now available that allows using TPAM as an external credential store.
For more information, see DEPRECATED How to connect One Identity TPAM with One Identity Safeguard for Privileged Sessions.
- The Duo Multi-Factor Authentication plugin has been updated for Duo Client version 3.3.0.
- A new Credential Store plugin is available for Safeguard for Privileged Passwords.
- A new Log Adapter plugin is available for SSHD application logs.
Improved Splunk integration
Forwarding data from SPS to Splunk has been greatly simplified, now you can configure SPS on the web interface to do so. Also, the amount of data forwarded to Splunk has been optimized. For details, "Using the Splunk forwarder" in the Administration Guide.
Figure 5: Basic Settings > Management > Splunk forwarder — Sending session data to Splunk
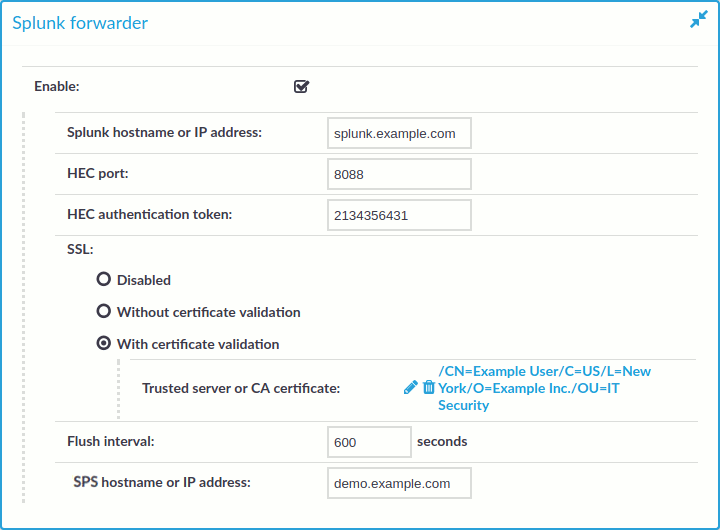
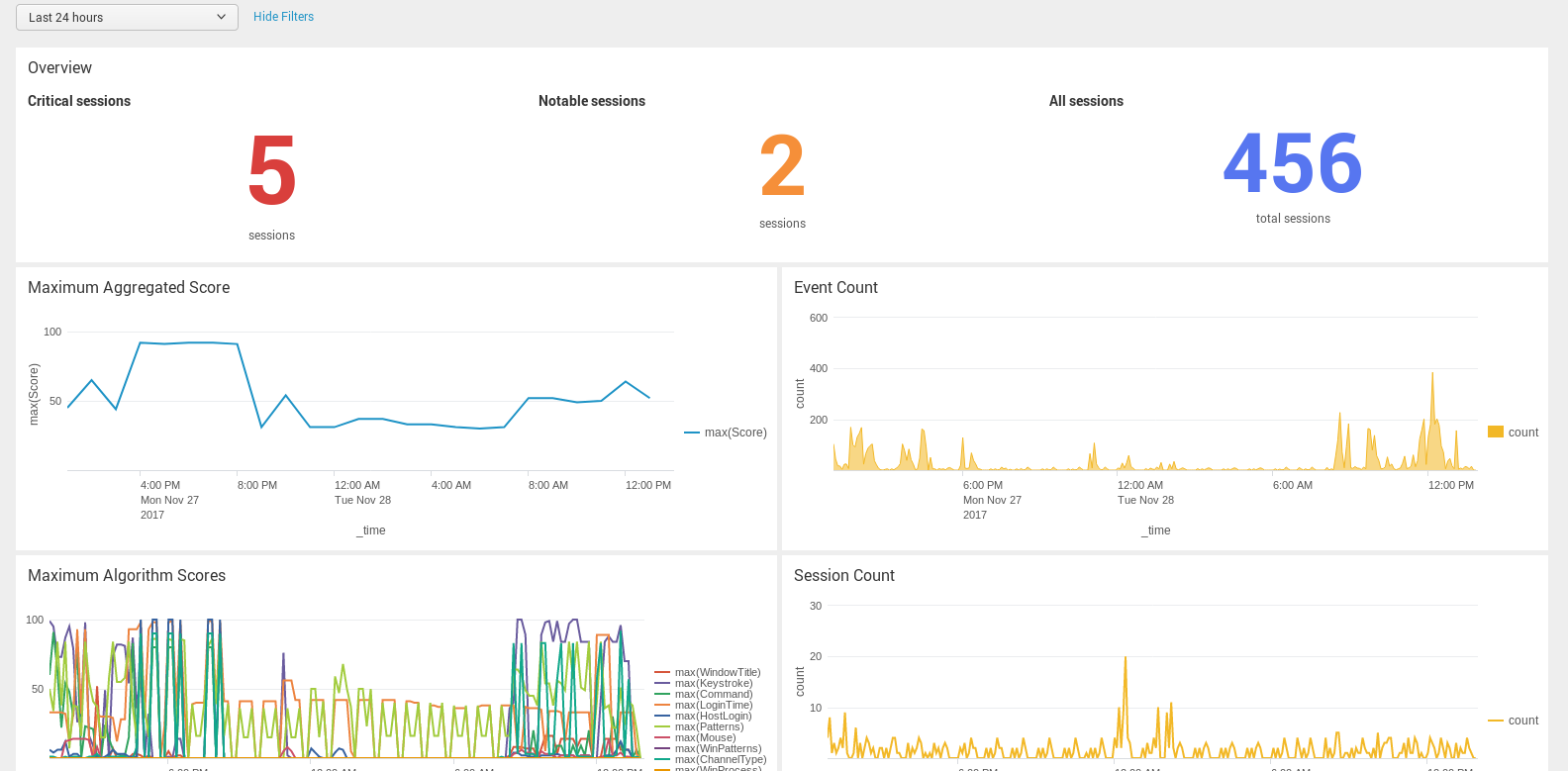
Figure 6: The One Identity Safeguard for Privileged Sessions App for Splunk
New Authentication and Authorization plugins
SPS acts as a central authentication gateway, enforcing strong authentication before users access sensitive IT assets. SPS can integrate with remote user directories to resolve the group memberships of users who access nonpublic information. Credentials for accessing information systems can be retrieved transparently from SPS's local credential store or a third-party password management system. This method protects the confidentiality of passwords as users can never access them. When used together with a multi-factor authentication provider, SPS directs all connections to the authentication tool, and upon successful authentication, it permits the user to access the information system.
SPS can interact with your third-party multi-factor authentication account and can automatically request strong multi-factor authentication for your privileged users who are accessing the servers and services protected by PSM. When used together with a third-party multi-factor authentication, SPS directs all connections to the tool, and upon successful authentication, it permits the user to access the information system.
The integration adds an additional security layer to the gateway authentication performed on SPS.
Multi-factor authentication plugins are available for the following products:
-
Duo
For an overview, see: Duo Multi-Factor Authentication - Overview
For detailed tutorial and configuration instructions, see: Duo Multi-Factor Authentication - Tutorial
-
inWebo
For an overview, see: inWebo Multi-Factor Authentication - Overview
For detailed tutorial and configuration instructions, see: inWebo Multi-Factor Authentication - Tutorial
-
Okta
For an overview, see: Okta Multi-Factor Authentication - Overview
For detailed tutorial and configuration instructions, see: Okta Multi-Factor Authentication - Tutorial
-
RSA
For an overview, see: RSA Multi-Factor Authentication - Overview
For detailed tutorial and configuration instructions, see: DEPRECATED RSA Multi-Factor Authentication - Tutorial
-
Starling
For an overview, see: Starling Two-Factor Authentication - Overview
For detailed tutorial and configuration instructions, see: Starling Two-Factor Authentication- Tutorial
-
YubiKey
For an overview, see: YubiKey Multi-Factor Authentication - Overview
For detailed tutorial and configuration instructions, see: YubiKey Multi-Factor Authentication - Tutorial
Other changes
-
Plugin configuration files in debug bundle: When creating debug bundles for troubleshooting purposes (for details, see "Collecting logs and system information for error reporting" in the Administration Guide), SPS now includes the configuration files of any plugins installed. Note that depending on the plugin, these configuration files can contain sensitive information, such as passwords or API keys. In this case, edit the plugin-related files in the plugins directory of the debug bundle and delete the sensitive information.
New documents
-
The Creating custom Authentication and Authorization plugins document is now publicly available. This document describes how to create custom Authentication and Authorization plugins.
-
The Creating custom Credential Store plugins document is now publicly available. This document describes how to create custom Credential Store plugins.
-
The documentation of the Safeguard for Privileged Sessions Plugin Software Development Kit (Plugin SDK) is now publicly available at https://oneidentity.github.io/safeguard-sessions-plugin-sdk/. The Plugin SDK provides base classes and services to enable rapid development of Python 3 plugins for the Safeguard for Privileged Sessions (SPS) product. SPS plugins released in the future will use this SDK.
New features between SPS 5.1 and 5.11 - indexing
Indexing sessions in near real-time
You now have the option to configure connection policies with near real-time indexing priority, meaning that you can start indexing sessions while they are still ongoing. This requires that you configure your indexers with the appropriate settings and capabilities. For details, see "Configuring the internal indexer" in the Administration Guide and "Configuring the external indexer" in the Administration Guide.
HSM support in external indexers
The external indexers now support using Hardware Security Modules to process encrypted audit trails. For details, see "Configuring a hardware security module (HSM) or smart card to integrate with external indexer" in the Administration Guide.
Lightweight indexing
One Identity Safeguard for Privileged Sessions is capable of analyzing the contents of the sessions it monitors to provide help analytics and speed up forensics investigations. This process is called indexing.
You can now select the depth of indexing: lightweight and full indexing.
Lightweight indexing is now enabled by default in case of a newly installed SPS or when you add new connection policies. If indexing was enabled for a connection policy it is converted to full indexing automatically during the upgrade.
Lightweight indexing is significantly faster than full indexing, but it extracts only the executed commands and the window titles that appear on the screen. It does not index any other screen content (for example, text that is displayed in a terminal or that appears in an RDP window).
For more information, see "Configuring the internal indexer" in the Administration Guide.
Performance improvements in indexing graphical sessions
To make the text displayed in graphical sessions (for example, RDP) SPS uses optical character recognition. The way this is done has been greatly optimized. Depending on the exact scenario and the contents of the session, this can significantly decrease the time required to index the audit trails.
Other changes
- When using a hardware security module (HSM) or smart card to integrate with an external indexer, the chroot is not used anymore, the solutions provided by RedHat/CentOS can be used. For more information, see "Configuring a hardware security module (HSM) or smart card to integrate with external indexer" in the Administration Guide.
-
It is now possible to change the accuracy level of the Optical Character Recognition (OCR) analysis of graphical sessions. The accuracy level remains unchanged for existing indexer policies but the new default is the "balanced" setting that offers much improved performance with a minimal trade-off in accuracy.
For details, see "Configuring the internal indexer" in the Administration Guide.
New features between SPS 5.1 and 5.11 - Safeguard Desktop Player
Safeguard Desktop Player replays audit trails of X11 sessions
The Safeguard Desktop Player application can now replay audit trails that contain graphical X11 sessions (the contents of the X11 Forward channel of the SSH protocol).
For further details, see "Replay X11 sessions" in the Safeguard Desktop Player User Guide.
Install the Safeguard Desktop Player application on Mac
It is now possible to install the Safeguard Desktop Player application on Mac.
For more information, see "Install Safeguard Desktop Player on Mac" in the Safeguard Desktop Player User Guide.
Follow active connections in Safeguard Desktop Player
It is now possible to follow active connections in semi-real time using Safeguard Desktop Player. In case you notice some user action that poses a security risk, you have the option to terminate the session you are monitoring. For detailed information, see "Replay audit files in follow mode" in the Safeguard Desktop Player User Guide
Audit trail encryption improvements
|
|
Caution:
One Identity Safeguard for Privileged Sessions (SPS) 5 F4 and later versions use a new encryption algorithm to encrypt the recorded audit trails (AES128-GCM). This change has the following effects:
|
You can now manually re-encrypt your audit trails with a new encryption key. This is useful if you want to share encrypted audit trails with third parties — the data remains encrypted, but you do not have to share your encryption keys. For details, see "Sharing an encrypted audit trail" in the Safeguard Desktop Player User Guide.
New features between SPS 5.1 and 5.11 - Protocols
Security settings of TLS sessions
You can now uniformly set the TLS security settings of HTTP, RDP, Telnet, and VNC connections, including the permitted ciphers and TLS versions on the <Protocol> Control > Settings pages.
To ensure the security of your sessions, SSL encryption is not supported anymore, only TLS 1.0 and later.
Using GSSAPI in SSH connections
You can now use an Authentication Policy with GSSAPI and a Usermapping Policy in SSH connections. When an SSH Connection Policy uses an Authentication Policy with GSSAPI, and a Usermapping Policy, then SPS stores the user principal as the Gateway username, and the username used on the target as the Server username.
Note that this change has the following side effect: when using an Authentication Policy with GSSAPI, earlier versions of SPS used the client-username@REALM username to authenticate on the target server. Starting with version 5.9.0, it uses the client-username as username. Configure your servers accordingly, or "Configuring usermapping policies" in the Administration Guide.
Session cookies in HTTP auditing
SPS can now distinguish the audited HTTP requests and responses based on the session cookies of web applications. For details, see "Creating and editing protocol-level HTTP settings" in the Administration Guide.
Authenticate HTTP/HTTPS connections on the SPS gateway
SPS now provides a way to authenticate non-transparent HTTP/HTTPS connections on SPS to local and external backends (LDAP, Microsoft Active Directory, RADIUS). The client must support proxy authentication.
For more information, see "Creating a new HTTP authentication policy" in the Administration Guide.
Credential store support for TN3270 protocol
SPS can now be configured to check out passwords from the built-in or external credential stores, such as One Identity Safeguard for Privileged Passwords, and play them in during a connection using the TN3270 protocol.

