Connecting to One Identity Safeguard for Privileged Sessions (SPS) locally or remotely using Secure Shell (SSH) allows you to access the console menu of SPS. The console menu provides access to the most basic configuration and management settings of SPS. It is mainly used for troubleshooting purposes, the primary interface of SPS is the web interface.
The console menu is accessible to the root user using the password set during completing the Welcome Wizard.
Figure 109: The console menu
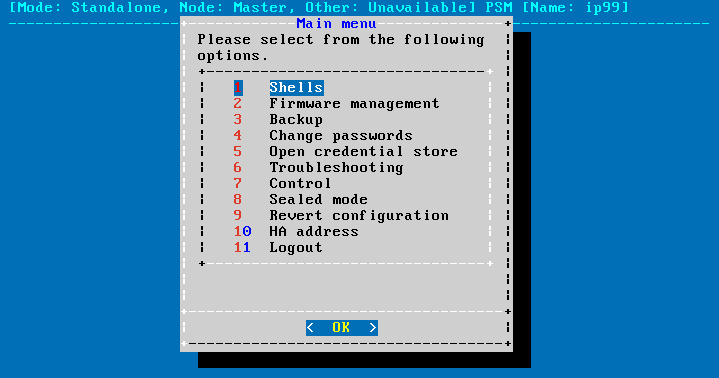
The console menu provides allows you to perform the following actions.
Access the local core and boot shells.
This is usually not recommended and only required in certain troubleshooting situations. Select the boot/core shell's keyboard layout for the local console. This will not affect the keyboard layout if you have accessed the shell via SSH.
The boot firmware boots up SPS, provides high availability support, and starts the core firmware. The core firmware, in turn, handles everything else: provides the web interface, manages the connections, and so on.
Select the active firmware, and delete unneeded firmwares.
Accessing the firmware management is useful if after an update the new firmware does not operate properly and the web interface is not available to activate the previous firmware.
Start backup processes.
For more information about backup processes, see Data and configuration backups.
Change the passwords of the root and admin users.
For details, see Changing the root password of One Identity Safeguard for Privileged Sessions (SPS).
Access the network-troubleshooting functions and display the available log files.
If the web interface is inaccessible, it can be the result of an internal locking error. To resolve this issue, delete the lock files. After deletion, they are archived, and included in the support bundle if they are not older than 30 days. To create a support bundle, if the web interface is inaccessible, select Create support bundle.
Reboot and shutdown the system.
For details, see Controlling One Identity Safeguard for Privileged Sessions (SPS): reboot, shutdown.
Enable and disable sealed mode.
For details, see Sealed mode.
Set the IP address of the HA interface.
For more information about assigning an IP address to the HA interface of a node, see Resolving an IP conflict between cluster nodes.
|

|
NOTE:
Note that logging in to the console menu automatically locks the SPS interface, meaning that users cannot access the web interface while the console menu is used. The console menu can be accessed only if there are no users accessing the web interface. The connection of web-interface users can be terminated to force access to the console menu. |
Exclusively for troubleshooting purposes, you can access the One Identity Safeguard for Privileged Sessions (SPS) host using SSH.
Completing the Welcome Wizard automatically disables SSH access to SPS. Re-enabling it allows you to connect remotely to the SPS host and login using the root user. The password of the root user is the one you provided in the Welcome Wizard. For details on how to change the root password from the web interface, see Changing the root password of One Identity Safeguard for Privileged Sessions (SPS).
The following encryption algorithms are configured on the local SSH service of SPS:
-
Key exchange (KEX) algorithms:
diffie-hellman-group-exchange-sha256
-
Ciphers:
aes256-ctr,aes128-ctr
-
Message authentication codes:
hmac-sha2-512,hmac-sha2-256
SSH access is, by default, protected against brute-force attacks: after 20 unsuccessful login attempts, the offending IP is blocked from accessing the SSH service for ten minutes.
You can turn off brute force protection by unselecting the Protect against brute-force attacks option for the SSH server.
To enable SSH access to the SPS host
-
Navigate to Basic Settings > Local Services > SSH server.
Figure 110: Basic Settings > Local Services > SSH server — Enabling remote SSH access to SPS
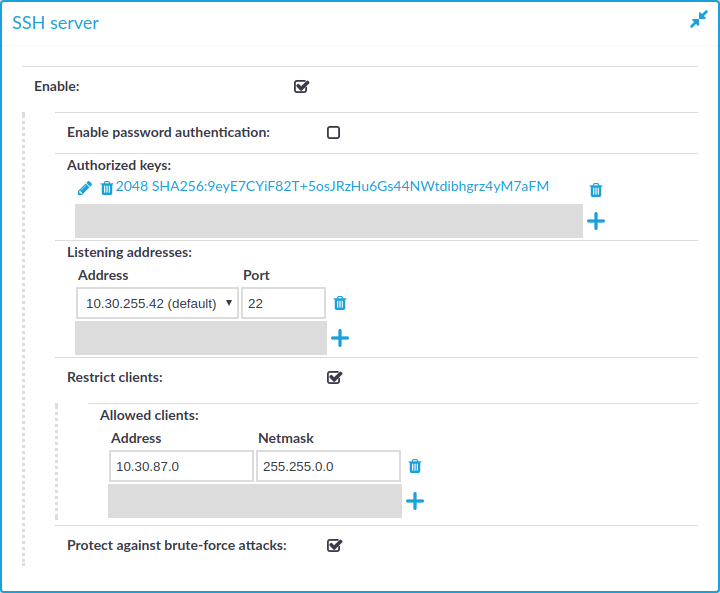
-
Select the Enable option.
|

|
NOTE:
Remote SSH access is automatically disabled if Sealed mode is enabled. For details, see Sealed mode. |
-
Choose the authentication method for the remote SSH connections.
-
To enable password-based authentication, select the Enable password authentication option.
-
To enable public-key authentication, click  in the Authorized keys field, click
in the Authorized keys field, click  and upload the public keys of the users who can access and manage SPS remotely via SSH.
and upload the public keys of the users who can access and manage SPS remotely via SSH.
One Identity recommends using 2048-bit RSA keys (or stronger).
-
Choose an address and a port for the SSH server in the Listening addresses section.
The available addresses correspond to the interface addresses configured in Basic Settings > Network > Interfaces. Only IPv4 addresses can be selected.
To add multiple addresses, click  .
.
-
(Optional) To permit SSH acces only from selected subnets or IP addresses, select Restrict clients, click  and enter the IP address and netmask of the allowed clients.
and enter the IP address and netmask of the allowed clients.
Use an IPv4 address.
To add multiple addresses, click  .
.
-
Click  .
.
The root password is required to access One Identity Safeguard for Privileged Sessions (SPS) locally, or remotely via an SSH connection. Note that the password of the root user can be changed from the console menu as well. For details, see Accessing the One Identity Safeguard for Privileged Sessions (SPS) console.
To change the root password of SPS
-
Navigate to Basic Settings > Management > Change root password.
Figure 111: Basic Settings > Management > Change root password — Changing the root password of SPS
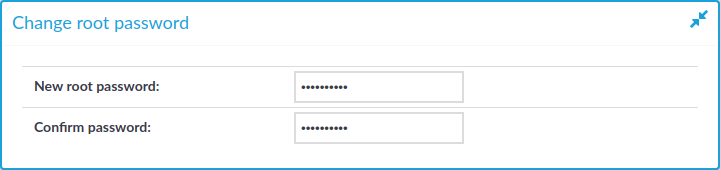
-
Enter the new password into the New root password and Confirm password fields.
|

|
NOTE:
One Identity Safeguard for Privileged Sessions (SPS) accepts passwords that are not longer than 150 characters. The following special characters can be used: !"#$%&'()*+,-./:;<=>?@[\]^-`{|} |
-
Click  .
.
In some cases, uploading large files over HTTP is not possible. In such cases, you can update the firmware using SSH.
|

|
Caution:
The recommended way to update the firmware is using the One Identity Safeguard for Privileged Sessions (SPS) web interface (see Upgrading One Identity Safeguard for Privileged Sessions (SPS)). Update the SPS firmware using SSH is only if you cannot update the firmware using the web interface. Note that updating using SSH may be removed from later versions of SPS. |
To update the firmware using SSH
-
Download the firmware file to your computer.
-
Log in to SPS remotely using SSH, and select Shells > Core shell from the console menu.
-
Copy the firmware to the SPS host, for example, into the /root/ directory.
If you are copying the firmware to SPS using SCP and you issue the copy command on the client side and not within the core firmware, the root directory of the core firmware is: /mnt/firmware/root
-
Install the firmware: /opt/scb/bin/firmwarectl install <path-to-firmware>
This command installs the firmware into the first empty slot, and returns the value of the slot where the firmware has been installed.
-
Check if you can upgrade to the new firmware, and resolve any errors before continuing: /opt/scb/bin/firmwarectl precheck <slot-number-of-the-firmware>
In the returned values, "exitcode": 0 means that the precheck has finished without any errors. "exitcode": 1 means that errors have occurred, and the contents of "output": [] gives you a clue as to what is causing the problem.
-
Activate the new firmware: /opt/scb/bin/firmwarectl activate <slot-number-of-the-firmware>
Using the /opt/scb/bin/firmwarectl list command, you can check whether activation has been successful. In the returned values, look for your slot number and the value of "active":, it should say true. For example:
...
"slot": 3,
"precheck": true,
"active": true,
"boot_link": "mnt/boot-firmware/slot3",
"core_link": "mnt/firmware/slot3",
"branch": "5.6",
"version": "5.6.0a",
"current": false,
...
-
Reboot SPS: xcbclient self xcb_do_reboot
-
If the upgrade is successful, delete any unused firmware: /opt/scb/bin/firmwarectl delete <slot-number-of-unused-firmware>
-
Delete the firmware file you uploaded to SPS, it is not needed anymore: rm -fv /root/<firmware-file-you-uploaded>





 in the Authorized keys field, click
in the Authorized keys field, click  and upload the public keys of the users who can access and manage SPS remotely via SSH.
and upload the public keys of the users who can access and manage SPS remotely via SSH. .
.