NOTE: The structure of these database tables may change in future One Identity Safeguard for Privileged Sessions (SPS) versions.
Table 28: Columns of the skipped_connections table
| channel_id |
integer |
The ID of the channel. This value is actually a reference to the id column of the channels table. |
| id |
integer |
The unique ID number of the entry. |
| occasions |
integer |
|
This view collects data about the connections which used a usermapping policy. The view is defined as follows:
select
channels.id,
channels.scp_path,
channels.subsystem_name,
channels.protocol,
channels.originator_port,
channels.channel_policy,
channels.target_addr,
channels._archive_path,
channels._close_cleanup,
channels.dynamic_channel,
channels.environment,
channels.session_start,
channels.remote_username,
channels.local_port,
channels.four_eyes_authorizer,
channels.src_ip,
channels.session_end,
channels._archive_server,
channels.server_port,
channels.username,
channels._archive_date,
channels.server_ip,
channels.exec_cmd,
channels._archive_policy,
channels.four_eyes_description,
channels.connection_id,
channels._connection_channel_id,
channels.rule_num,
channels.target_port,
channels.src_port,
channels.originator_addr,
channels.auth_method,
channels.audit,
channels.local_ip,
channels.session_id,
channels.device_name,
channels.channel_type,
channels."connection",
channels.verdict,
channels.dst_port,
channels.dst_ip
from channels
where channels.remote_username is not null
and channels.username <> channels.remote_username;
The the usermapped_channels view has the following columns.
NOTE: The structure of these database tables may change in future One Identity Safeguard for Privileged Sessions (SPS) versions.
Table 29: Columns of the usermapped_channels table
| _archive_date |
date |
Archive date: The date when the connection was archived or cleaned up. |
| _archive_path |
text |
Archive path: The path where the audit trail was archived on the remote server. |
| _archive_policy |
text |
|
| _archive_server |
text |
Archive server: The hostname or IP address of the remote server where the audit trail was archived. |
| audit |
text |
Audit-trail: Name and ID of the audit file storing the traffic of the channel. If the session has an audit trail, a  icon is displayed. Note that a the following letters may appear on the download icon: icon is displayed. Note that a the following letters may appear on the download icon: |
| auth_method |
text |
Authentication method: The authentication method used in the connection. For example, password |
| channel_policy |
text |
Channel policy: The Channel policy applied to connection. The Channel policy lists the channels (for example, terminal session and SCP in SSH, or Drawing and Clipboard in RDP) that can be used in the connection, and also determines if the channel is audited or not. The Channel policy can also restrict access to each channel based on the IP address of the client or the server, a user list, user group, or a time policy. |
| channel_type |
text |
Channel type: Type of the channel. |
| _close_cleanup |
boolean |
|
| _connection_channel_id |
integer |
Unique connection ID: The unique identifier of the connection. |
| connection_id |
text |
Connection policy ID: The identifier of the connection policy. |
| connection |
text |
Connection policy: The connection policy that handled the client's connection request. |
| device_name |
text |
Device name: The name or ID of the shared device (redirect) used in the RDP connection. |
| dst_ip |
text |
Destination IP: The IP address of the server as requested by the client. |
| dst_port |
integer |
Destination port: The port number of the server as requested by the client. |
| dynamic_channel |
text |
Dynamic channel: The name or ID of the dynamic channel opened in the RDP session. |
| exec_cmd |
text |
Exec command: The command executed in a Session exec channel. |
| four_eyes_authorizer |
text |
Four-eyes authorizer: The username of the user who authorized the session. Available only if 4-eyes authorization is required for the channel. For details on 4-eyes authorization, see Configuring four-eyes authorization. |
| four_eyes_description |
text |
Four-eyes description: The description submitted by the authorizer of the session. |
| id |
integer |
|
| local_ip |
text |
Server-local IP: The IP address of SPS used in the server-side connection. |
| local_port |
integer |
Server-local port: The port number of SPS used in the server-side connection. |
| originator_addr |
text |
Port/X11 forward originator IP: The IP address of the host initiating the channel in Remote Forward and Local Forward channels. Note that this host is not necessarily the client or the server of the SSH connection. |
| originator_port |
integer |
Port/X11 forward originator port: The number of the forwarded port in Remote Forward and Local Forward channels. |
| protocol |
text |
Protocol: The protocol used in the connection (Citrix ICA, HTTP, RDP, SSH, Telnet, or VNC). |
| remote_username |
text |
Username on server: The username used to log in to the remote server. This username can differ from the client-side username if usermapping is used in the connection. For details on usermapping, see Configuring usermapping policies. |
| rule_num |
text |
Rule number: The number of the line in the Channel policy applied to the channel. |
| scp_path |
text |
SCP path: Name and path of the file copied via SCP. Available only for SCP sessions (Session exec SCP SSH channels) if the Log file transfers to database option is enabled in the Channel Policy of the connection. |
| server_ip |
text |
Server IP: The IP address of the server connected by SPS. |
| server_port |
integer |
Server port: The port number of the server connected by SPS. |
| session_end |
integer |
End time: Date when the channel was closed. |
| session_id |
text |
Session ID:
A globally unique string that identifies the session. This session ID has the following format: svc/<unique-random-hash>/<name-of-the-connection-policy>:<session-number-since-service-started>/<protocol>, for example, svc/5tmEaM7xdNi1oscgVWpbZx/ssh_console:1/ssh.
Log messages related to the session also contain this ID. For example: 2015-03-20T14:29:15+01:00 demo.example
zorp/scb_ssh[5594]: scb.audit(4):
(svc/5tmEaM7xdNi1oscgVWpbZx/ssh_console:0/ssh):
Closing connection; connection='ssh_console',
protocol='ssh', connection_id='409829754550c1c7a27e7d',
src_ip='10.40.0.28', src_port='39183',
server_ip='10.10.20.35', server_port='22',
gateway_username='', remote_username='example-username',
verdict='ZV_ACCEPT'
|
| session_start |
integer |
Start time: Date when the channel was started. |
| src_ip |
text |
Source IP: The IP address of the client. |
| src_port |
integer |
Source port: The port number of the client. |
| subsystem_name |
text |
Subsystem name: Name of the SSH subsystem used in the channel. |
| target_addr |
text |
Port-forward target IP: The traffic was forwarded to this IP address in Remote Forward and Local Forward channels. |
| target_port |
integer |
Port-forward target port: The traffic was forwarded to this port in Remote Forward and Local Forward channels. |
| username |
text |
Username: The username used in the session.
-
If the user performed inband gateway authentication in the connection, the field contains the username from the gateway authentication (gateway username).
-
Otherwise, the field contains the username used on the remote server. |
| verdict |
text |
Verdict: Indicates what SPS decided about the channel.
-
ACCEPT: Accepted.
-
ACCEPT-TERMINATED: Connection was accepted and established, but a content policy terminated the connection. For details on content policies, see Real-time content monitoring with Content Policies.
-
CONN-AUTH-FAIL: User authentication failed.
-
CONN-DENY: Connection rejected.
-
CONN-FAIL: Connection failed, that is, it was allowed to pass SPS but timed out on the server.
-
CONN-GW-AUTH-FAIL: Gatway authentication failed.
-
CONN-KEY-ERROR: Hostkey mismatch.
-
CONN-USER-MAPPING-FAIL: Usermapping failed.
-
DENY: Denied.
-
FOUR-EYES-DEFERRED: Waiting for remote username.
-
FOUR-EYES-ERROR: Internal error during four-eyes authorization.
-
FOUR-EYES-REJECT: Four-eyes authorization rejected.
-
FOUR-EYES-TIMEOUT: Four-eyes authorization timed out. |
To help you comply with the regulations of the Payment Card Industry Data Security Standard (PCI DSS), One Identity Safeguard for Privileged Sessions (SPS) can generate reports on the compliance status of SPS. Note that this is not a fully-featured compliance report: it is a tool to enhance and complement your compliance report by providing information available in SPS. The report corresponds with the document Payment Card Industry (PCI) Data Security Standard, Requirements and Security Assessment Procedures, Version 3.0, published by the PCI Security Standards Council.
For details on the contents of the report, see Contents of PCI DSS reports.
To create PCI DSS reports
-
Log in to the SPS web interface, and navigate to Reporting > Create & Manage Reports > Built-in reports > PCI DSS > Create report.
Figure 345: Reporting > Create & Manage Reports > Built-in reports > PCI DSS > Create report — Generating PCI DSS reports
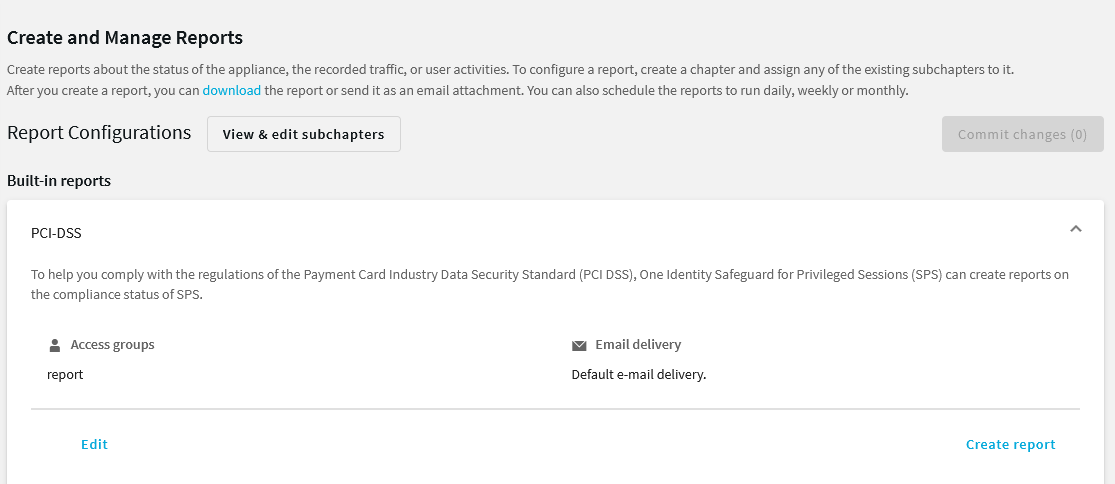
-
By default, members of the report group can access the custom reports through the SPS web interface. To change this, click Edit and enter the name of a different group into the Groups field.
NOTE: Members of the listed groups can access only these custom reports even if their groups do not have read access to the Reporting > Download reports page. However, only those reports will be listed, to which their group has access to.
-
By default, SPS sends out the reports in email to the address set in the Basic Settings > Management > Mail settings > Send reports to field.
NOTE: If this address is not set, the report is sent to the SPS administrator's email address.
-
To disable email sending, clear the Deliver in email option.
-
To email the reports to a different address, select Custom, and enter the email address where the reports should be sent. Click Add email to list multiple email addresses if needed.
-
Click Update report.
-
Click Create report.
The report will be automatically added in the list of reports (Reporting > Download reports), and also sent in an e-mail to the regular recipients of the report.

 icon is displayed. Note that a the following letters may appear on the download icon:
icon is displayed. Note that a the following letters may appear on the download icon:
