The following sections describe configuration settings available only for the ICA protocol. Use the following policies to control who, when, and how can access the ICA connection.
NOTE: As an experimental feature, IPv6 addresses can be configured for ICA connections.
-
ICA connections: For details, see Setting up ICA connections.
-
Channel Policy: The channel policy determines which ICA channels (for example clipboard, file-sharing, and so on) can be used in the connection, and whether they are audited or not. The different channels may be available only under certain restrictions, as set in the channel policy. For details, see Creating and editing channel policies.
-
ICA settings: ICA settings determine the parameters of the connection on the protocol level, including timeout value and display parameters. For details, see Creating and editing protocol-level ICA settings.
-
Deployment scenarios: These describe the available One Identity Safeguard for Privileged Sessions (SPS) deployment scenarios in a Citrix environment. For details, see One Identity Safeguard for Privileged Sessions (SPS) deployment scenarios in a Citrix environment


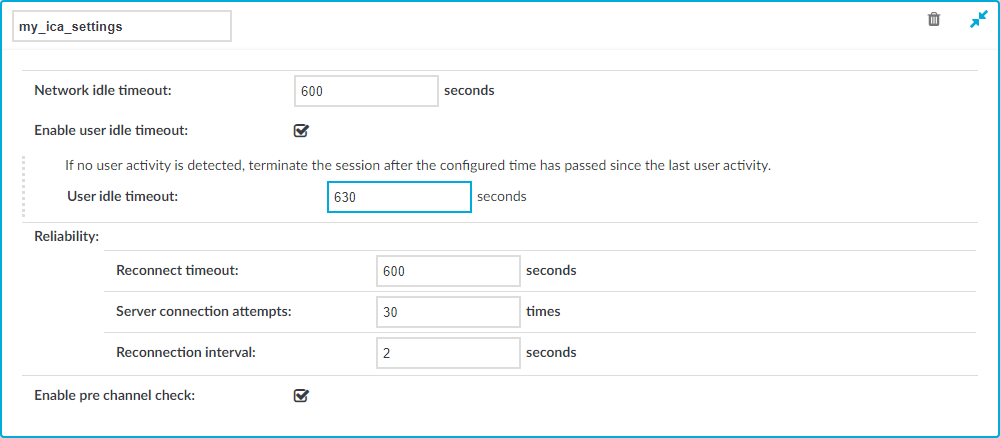
 to create an ICA setting profile. Enter a name for the profile (for example ica_special).
to create an ICA setting profile. Enter a name for the profile (for example ica_special). to display the parameters of the ICA connection.
to display the parameters of the ICA connection. .
.