Using One Identity Password Policies
With Password Manager, you can create custom password policies that extend the system password policy rules.
To create and manage One Identity password policies, you need to add a domain connection on the Password Policies tab of the Administration site. When adding the domain connection, you specify the domain to which password policies will be applied and the credentials that will be used to access the domain.
After you have added the domain connection, you can create password policies for this domain. For each password policy, you can specify a name, a set of policy rules, and a scope.
|

|
NOTE: Password policy rules are applied and displayed on the Self-Service site when users change or reset passwords only after you have added the domain connection and created policies for the corresponding domain. |
Using Fine-Grained Password Policies
By default, existing fine-grained password policies are applied to users from fine-grained password policies’ scopes. But to be able to manage fine-grained password policies and to have the Self-Service site display the password policy rules when users reset or change passwords, you need to add a domain connection on the Password Policies tab of the Administration site.
When adding the domain connection, you specify the domain to which password policies will be applied and the credentials that will be used to access the domain.
|

|
NOTE: The default domain password policy is applied to users from the policy scope, but the policy itself is not displayed in the policy list on the Administration site. |
|

|
NOTE: Creating a new Windows fine-grained password policies, does not contain a Policy Scope by default. Hence, by clicking Edit on the newly created Windows fine-grained password policies and configuring the required Policy Scope in the Password Policy Properties window, one can view these policies for the configured users in the Self service site. |
Applying Multiple Password Policies
If a user is found in the scopes of a default domain password policy, a fine-grained password policy, and a One Identity password policy, the applicable policy is selected in the following algorithm. The default domain policy is ignored. The rules from the fine-grained and One Identity policies are merged with the strictest value selected for each rule.
If a user is found in the scopes of several fine-grained password policies, the applicable policy is selected automatically in Active Directory.
If a user is found in the scopes of several One Identity password policies, then the policy with the highest priority is applied to the user. Note that priority can be changed for policies with the same scope.
Using Password Policy Manager
Password Policy Manager is a separate component of Password Manager that allows enforcing One Identity password policy rules when users change or reset passwords by means other than the Self-Service site.
For example, you have configured a One Identity password policy for users from domain “My Domain.” When users from this domain change or reset passwords on the Self-Service site (the user on the left in the diagram below), the configured One Identity password policy is applied, and corresponding policy rules are displayed. This happens because Password Policy Manager is always available with the Password Manager service. But when users try to change or reset passwords by pressing CTRL+ALT+DELETE, for example (the user on the right in the diagram below), the configured One Identity password policy will not be enforced.
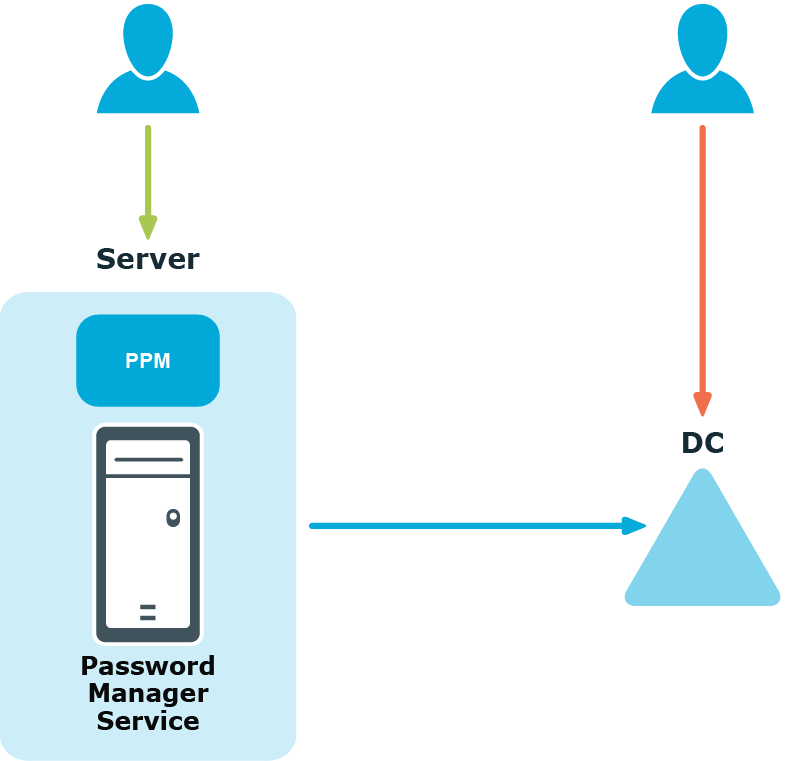
To enforce the configured One Identity password policy in cases when users change or reset passwords not via the Self-Service site, you must install Password Policy Manager on all domain controllers in the domain. In the case when Password Policy Manager is installed on domain controllers in the managed domain, when the same users change or reset password by pressing CTRL+ALT+DELETE, the One Identity password policy will be applied.
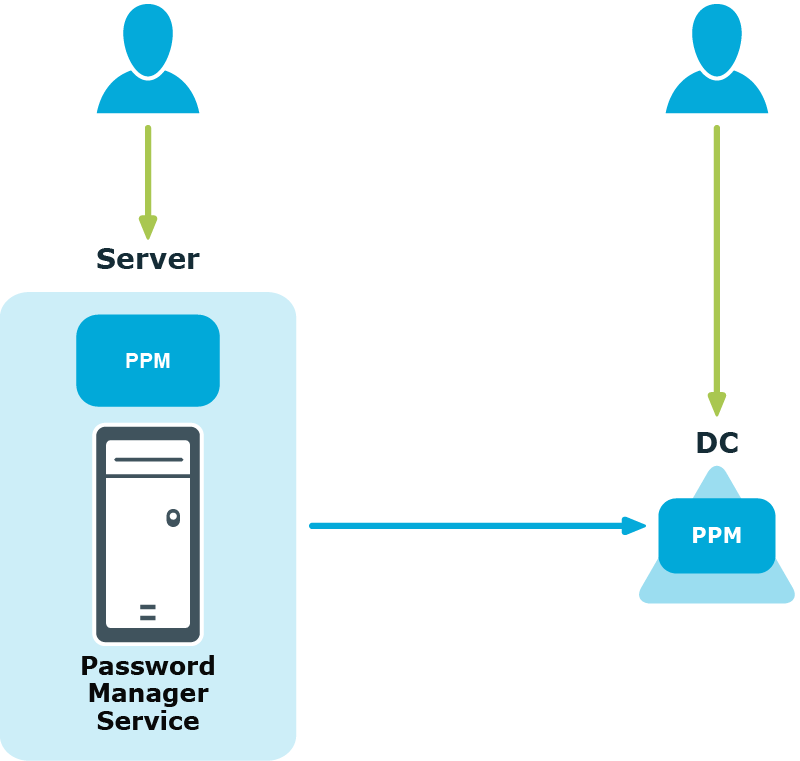
Therefore, if users from your managed domain change or reset their password on the Self-Service site only, you do not need to install Password Policy Manager on all domain controllers in the domain. But if you want to ensure that password policies are enforced when users change or reset passwords by means other than the Self-Service site, you must install Password Policy Manager on all domain controllers in the domain.
For more information on how to install Password Policy Manager, see Installing Password Policy Manager.



