Introducing Privilege Manager for Unix
Introducing Privilege Manager for Unix
Privilege Manager for Unix protects the full power of root access from potential misuse or abuse. Privilege Manager for Unix helps you to define a security policy that stipulates who has access to which root function, as well as when and where individuals can perform those functions. It controls access to existing programs as well as any purpose-built utilities used for common system administration tasks. With Privilege Manager for Unix, you do not need to worry about someone - whether inadvertently or maliciously - deleting critical files, modifying file permissions or databases, reformatting disks, or damaging UNIX systems in more subtle ways.
Figure 1: Privilege Manager for Unix protection
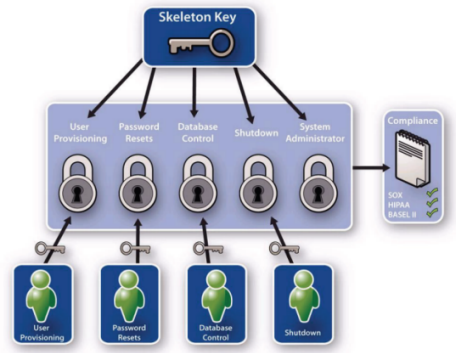
Within the UNIX world, common management tasks often require root access. Unfortunately, native root access is an all-or-nothing proposition. Consequently, as organizations add new users, fix printer queues, and perform other routine jobs on UNIX systems, the concern for control, compliance, and security grows. These routine tasks should not expose root passwords to those who don’t need them.
Privilege Manager for Unix also allows administrators to increase security as it protects sensitive data from network monitoring by encrypting root commands or sessions it controls. This capability includes control messages and input entered by users as they run commands through Privilege Manager for Unix.
What is Privilege Manager for Unix
Privilege Manager for Unix allows system administrators to safely share the power of root and other important accounts by partitioning them among users in a secure manner. System administrators can specify the circumstances under which users may run certain programs as root (or other privileged accounts).
The result is that you can safely assign the responsibility for such routine maintenance activities as adding user accounts and fixing line printer queues to the appropriate people without disclosing the root password. The full power of root is thus protected from potential misuse or abuse, reducing the risk of system administrator error or misuse (for example, modifying databases or file permissions, erasing disks, or more subtle damage).
Privilege Manager for Unix is capable of selectively recording all activities involving root, including all keyboard input and display output, if required. This indelible audit trail, combined with the safe partitioning of root functionality, provides an extremely secure means of sharing the power of root. A replay utility is provided to allow recorded sessions to be viewed at a later date. Privilege Manager for Unix can also require a checksum match before running any program, thereby guarding against virus or trojan horse attack on important accounts.
Additionally, Privilege Manager for Unix can provide an audit trail of:
-
all users running commands on a particular host
This may be required if, for example, the host is particularly sensitive, or because access to this host is chargeable.
-
for a particular user
This may be required if, for example, a temporary contractor has been provided with a login to a host, and the administrator needs to check which files the contractor has accessed.
Benefits of Privilege Manager for Unix
Privilege Manager for Unix is an important component of any heterogeneous organization's comprehensive compliance and identity management strategy. It perfectly complements UNIX identity integration initiatives using Authentication Services and compliance efforts enhanced through One Identity's Compliance Portal.
Some of the benefits that Privilege Manager for Unix brings to your organization are:
-
enhanced security through fine-grained, policy-based control of root access
-
compliance through compartmentalization of IT tasks that require root access
-
visibility and control through automated, secure keystroke logging
-
attainment of compliance and internal security standards through automated gathering of necessary data
-
prevention of unapproved UNIX root activity
How Privilege Manager for Unix protects
Privilege Manager for Unix protects your systems by:

