Certificate distribution policy
Group Policy supports the ability to distribute trusted certificates. Certificates in the "Trusted Root Certification Authorities" and "Intermediate Certification Authorities" group policies (located at <Policy_Object_Name>/Computer Configuration/Windows Settings/Security Settings/Public Key Policies/) are automatically copied to the UNIX host. After group policy has applied them, the certificates are located at /var/opt/quest/vas/certs/CA/ and are automatically copied into Keychain on macOS.
Refer to the following link for the procedure to add a trusted root certification authority to a Group Policy object: http://technet.microsoft.com/en-us/library/cc738131%28v=ws.10%29.aspx
Managing local file permissions
Managing local file permissions
Safeguard Authentication Services provides tools to help consolidate UNIX identity into a single entity in Active Directory. As part of this process, you may need to change permissions on local UNIX files and directories. The Ownership Alignment Tool (OAT) helps simplify this process by matching accounts and providing the ability to roll back changes.
The Ownership Alignment Tool
The Ownership Alignment Tool (OAT) provides a flexible solution for changing resource ownership to accommodate changes in users’ UID/GID, and changes to group membership before, during, or after migration to Active Directory.
OAT is a general-purpose tool that combines an automated solution with fine-grained control, reporting, error recovery, the ability to stop and restart bulk updates, and rollback capability. OAT provides the necessary flexibility to update file or directory ownerships in a production environment.
OAT features include:
-
Breaking a migration down into multiple projects.
-
Rollback and restore to a previous state.
-
Automated matching of UNIX and Windows identities.
OAT allows you to:
-
Match local UNIX/Linux users to their corresponding Active Directory user.
-
Resolve conflicts with existing users and groups.
OAT leverages the single, enterprise-wide identity based on the user's Active Directory identity. OAT maps multiple UNIX accounts to a single, authoritative, Active Directory-based identity:
Figure 1: Ownership Alignment Tool (OAT)
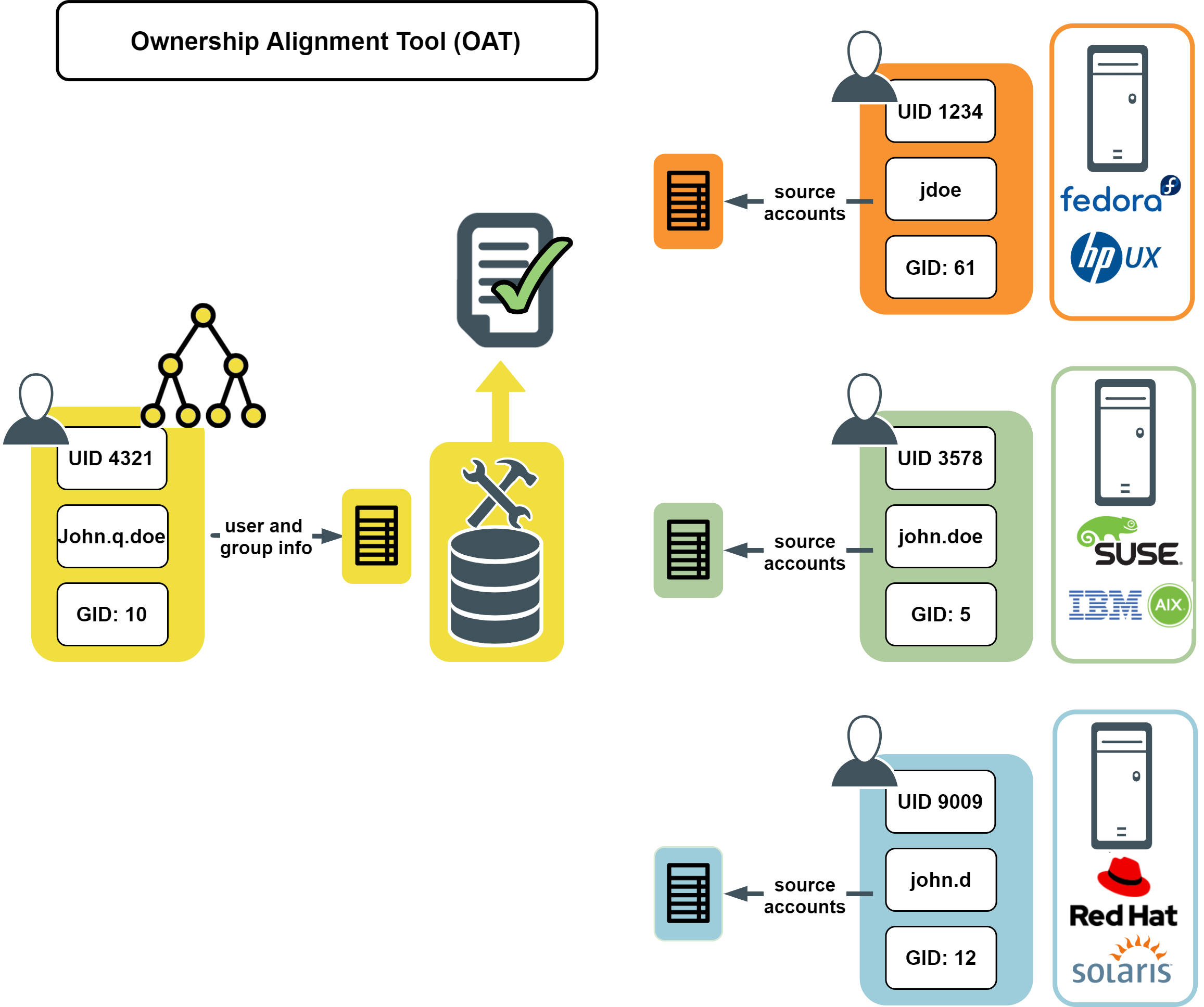
Using OAT
You use OAT to change the ownership of files and directories on UNIX hosts to reflect the UID and GID in Active Directory. This allows you to maintain user or group information exclusively in Active Directory.
Use one of the following ways to change file ownership:
You can run OAT any time after you have installed Safeguard Authentication Services. OAT makes scenarios such as mergers, acquisitions, and business unit restructuring much simpler. If you have been using override files and mapped users, you can simplify your Safeguard Authentication Services implementation by running OAT.
OAT allows you to maintain user information in Active Directory and simplify the footprint of information required on each UNIX host. To do this, set the UID (User ID) and GID (Group ID) of each file or directory on each host to that of the User ID and Group ID maintained in Active Directory. For example, suppose you have the following user information:
|
hosta |
jdoe |
100 |
files and/or directories on hosta have owner uid 100 |
|
hostb |
johnd |
1000 |
files and/or directories on hosta have owner uid 1000 |
|
hostc |
john |
10000 |
files and/or directories on hosta have owner uid 10000 |
And in Active Directory you have:
After running OAT, the UID associated with each file and/or directory on each host is 55555, as follows:
|
hosta |
100 |
55555 |
files and/or directories on hosta have owner uid 55555 |
|
hostb |
1000 |
55555 |
files and/or directories on hosta have owner uid 55555 |
|
hostc |
10000 |
55555 |
files and/or directories on hosta have owner uid 55555 |
Once you have changed the UID and GID to reflect the information now maintained in Active Directory, you can remove the /etc/passwd, /etc/shadow, and /etc/group information from each host. Safeguard Authentication Services allows proper permission handling of each file and directory.

