Partition root safely
The ability to partition system administration actions without compromising the security of the root account is an extremely powerful one. Privilege Manager for Unix allows you, the system administrator, to set policies to determine whether and when a user request to run a program is accepted or rejected.
Through Privilege Manager for Unix, each user can request that a specific program is run on a specific machine as root (or as another important account such as oracle or admin). Privilege Manager for Unix evaluates the request; if accepted, it runs the program, locally or across a network, on behalf of the user.
With Privilege Manager for Unix, Helpdesk personnel can replace passwords for users or reinstate user accounts. Project members can clear a jammed line printer queue, kill hung programs, or reboot certain machines. Administration staff can print or delete resource usage logs or start backups.
Through partitioning, Privilege Manager for Unix allows different users to perform the root actions for which they are responsible, but prevents them from performing actions for which they do not have authorization.
Privilege Manager for Unix lets you specify:
-
which users can perform a particular task
-
which tasks can be run through the system
-
when the user can perform the task
-
which machine can perform a task
-
from which machine the user may initiate a request to perform the task
-
whether another user’s permission (in the form of a password) is required before the task is started
-
decisions to be made by a program that you supply, which Privilege Manager for Unix calls to determine if a request should be accepted or rejected
-
many other miscellaneous properties of requests
Create an indelible audit trail
Privilege Manager for Unix can record all activity which passes through it, down to the keystroke level. The power to accurately log root and other account activities in a safe environment allows you to implement a secure system administration regime with an indelible audit trail. You always know exactly what is happening in root, as well as who did it, when it happened and where.
Since root can modify any file, you must ensure that Privilege Manager for Unix logs are indelible. You can configure Privilege Manager for Unix to receive user requests from the submitting machine, run tasks on the execution machine, and log all activities on a third, very secure machine. See the illustration in How Privilege Manager for Unix works.
You can make the machine containing the log files physically inaccessible to users and isolated from remote login over the network. In addition, you can print the logs to hard copy on a secure printer or recorded to a WORM drive.
You can also assign this secure machine a root password which is unknown to the person who has physical access to it, but known to someone else without physical access. Two people would have to conspire to subvert system security.
You may use these and other techniques to achieve a high degree of security around Privilege Manager for Unix itself, as well as the logs of root activity that it creates.
Encryption
You can encrypt all communication among Privilege Manager for Unix programs, and between the user and the application being run to guard against network snooping or spoofing.
Privilege Manager for Unix supports the following encryption algorithms:
-
AES
-
Kerberos
-
TripleDES and DES
Set the encryption method in the /etc/opt/quest/qpm4u/pm.settings file. For more details, see the encryption setting in PM settings variables.
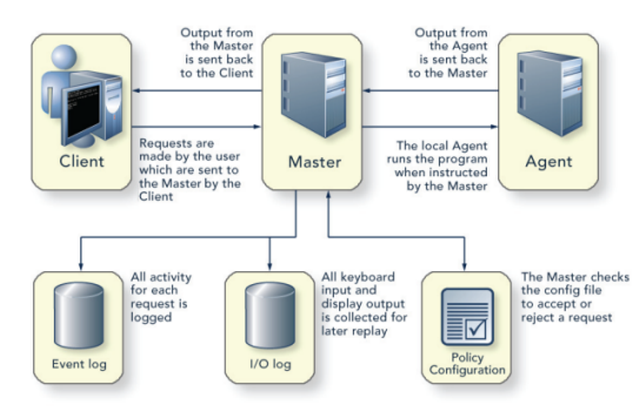
How Privilege Manager for Unix works
The three main Privilege Manager for Unix components are:
-
The Client: The client is effectively the user who runs a command from their local machine by simply performing commands as root using the pmrun prefix.
-
The Policy Server: The policy server checks all commands with the policy file to ensure that the user is allowed to run the command, it then passes the command on to the agent for action. The policy server also logs the output result (that is, whether the command was successfully actioned or not), whether you enable keystroke logging or not.
If you enable keystroke logging, it creates a much more detailed set of log files. The input/output log stores everything from keystrokes to input and output data. The event log purely records all of the requests made and their result.
-
The Agent: The agent performs the commands which are issued from the policy server and passes the result back to the client.
Figure 2: Privilege Manager for Unix components
Privilege Manager for Unix comprises four main programs:
-
pmrun
-
pmmasterd
-
pmlocald
-
pmtunneld
Users submit their requests to run certain programs through Privilege Manager for Unix using pmrun. For each request, the user may specify a program name and optionally a host on which the program will run.
The configuration file policy server master daemon (pmmasterd) examines each user request and either accepts or rejects it based upon information in the Privilege Manager for Unix configuration file. You can have multiple pmmasterd daemons on the network to avoid having a single point of failure.
All Privilege Manager for Unix administrative tools, including the configuration commands are located in the /opt/quest/sbin directory.

