Privilege Manager for Unix can configure central logging for I/O and event logs using the iologhost and eventloghost policy variables.
pmmasterd uses port number 12345 by default to communicate with the log server.
A host that is configured as a centralized log server must have the client's keyword added to the pm.settings file to specify which policy servers may forward their I/O and event log information to this log server.
Figure 9: Configuring central logging for I/O and event Logs
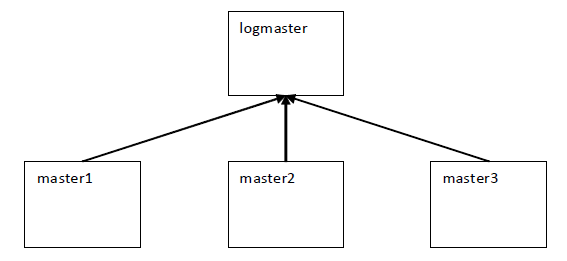
In this example, master1, master2, master3, and logmaster are all Privilege Manager for Unix policy servers (pmmasterd).
logmaster is configured as the centralized log host for I/O and event logs for master1, master2 and master3. To send I/O and event log information to logmaster, the policy must include the following statements:
iologhost = "logmaster";
eventloghost = "logmaster";
If for any reason (such as a system outage) the logs cannot be forwarded to the central logging host (logmaster in the above example), log files are stored locally on the authenticating policy server (master1, master2, or master3 in the above example). The location of the log files is specified by the tmplogdir policy variable, which defaults to var/opt/quest/qpm4u/iolog/queue.
The pm.settings file for logmaster must include the clients keyword. For example:
clients master1 master2 master3
Related Topics
PM settings variables
tmplogdir
An effective strategy for controlling the size of the log file in Privilege Manager for Unix is to limit the amount of information sent to the logs. Instead of logging keystrokes for every command, you might construct a policy that only captures keystrokes for sensitive commands.
You can use policy variables to limit the information sent to the log files.
Table 22: Size-controlling logging variables
|
iolog_encrypt |
boolean |
Enables I/O logs encryption; default is "true".
Log files are encrypted with AES; view them with pmreplay. |
|
iolog_errmax |
integer |
Limits the amount of text logged for stderr for each command. |
|
iolog_opmax |
integer |
Limits the amount of text logged for stdout for each command. For example, if iolog_opmax is set to 500 and you enter the following command: cat filename1
it only logs the first 500 bytes of output produced by this command. |
|
logomit |
list |
Specifies the names of variables to omit when logging to an event log (no default). Use this to reduce the amount of disk space used by event logs. |
|
logstderr |
boolean |
Specifies if error output is logged; default is "true". |
|
logstdin |
boolean |
Specifies whether input is logged; default is "true". |
|
logstdout |
boolean |
Specifies whether output is logged; default is "true". |
Using command line tools, you can list events and replay log files directly from the primary policy server using the pmlogsearch, pmreplay, and pmremlog commands.
pmlogsearch
pmlogsearch is a simple search utility based on common criteria. Run pmlogsearch on the primary server to query the logs on all servers in the policy group. pmlogsearch provides a summary report on events and keystroke logs matching at least one criteria. pmlog provides a more detailed report on events than pmlogsearch.
Hostnames may appear in the event logs and keystroke log files in either fully qualified format (myhost.mycompany.com) or in short name format (myhost), depending on how hostnames are resolved and the use of the short name setting in the pm.settings file. To ensure that either format is matched, use the short host name format with an asterisk wildcard (myhost*) when specifying a hostname search criteria.
For more information about the syntax and usage of the pmlogsearch command, see pmlogsearch.
pmlogsearch performs a search across all policy servers in the policy group and returns a list of events (and associated keystroke log file names) for requests matching the specified criteria. You specify search criteria using the following options (you must specify at least one search option):
Table 23: Search criteria options
|
--after "YYYY/MM/DD hh:mm:ss" |
Search for sessions initiated after the specified date and time. |
|
--before "YYYY/MM/DD hh:mm:ss" |
Search for sessions initiated before the specified date and time. |
|
--host hostname |
Search for sessions that run on the specified host. |
|
--result accept|reject |
Return only events with the indicated result. |
|
--text keyword |
Search for sessions containing the specified text. |
|
--user username |
Search for sessions by the specified requesting user. |
The following pmlogsearch options support the use of wildcards, such as * and ?:
To match one or more characters, you can use wild card characters (such as ? and *) with the --host, --text, and --user options; but you must enclose arguments with wild cards in quotes to prevent the shell from interpreting the wild cards.
If there is a keystroke log associated with the event, it displays the log host and pathname along with the rest of the event information.
The following example lists two events with keystroke (IO) logs:
# pmlogsearch --user sally
Search matches 2 events
2013/03/16 10:40:02 : Accept : sally@qpmsrv1.example.com
Request: sally@qpmsrv1.example.com : id
Executed: root@qpmsrv1.example.com : id
IO Log: qpmsrv1.example.com:/opt/quest/qpm4u/iologs/demo/sally/id_20120316_1040_ESpL6L
2013/03/16 09:56:22 : Accept : sally@qpmsrv2.example.com
Request: sally@qpmsrv2.example.com : id
Executed: root@qpmsrv2.example.com : id
IO Log: qpmsrv2.example.com:/opt/quest/qpm4u/iologs/demo/sally/id_20120316_0956_mrVu4I
pmreplay
You can use the pmreplay command to replay a keystroke log file if it resides on the local policy server.
To replay the log, run:
# pmreplay <path_to_keystroke_log>
For example, the following command replays the first ls -l /etc log from the previous example:
# pmreplay /opt/quest/qpm4u/iologs/demo/sally/id_20120316_1040_ESpL6L
pmremlog
If the keystroke log resides on a remote policy server, you can use the pmremlog command with the -h <remote_host> and -p pmreplay options to remotely replay a keystroke log file. You specify the path argument to the remote pmreplay after the -- flag.
For example, enter the following command all on one line:
# pmremlog -h qpmsrv2 -p pmreplay -- /opt/quest/qpm4u/iologs/demo/sally/id_20120316_0956_mrVu4I
Host names may appear in the event logs and keystroke log files in either fully qualified format (myhost.mycompany.com) or in short-name format (myhost), depending on how host names are resolved and the use of the shortnames setting in the pm.settings file. To ensure that either format is matched, when you specify a host name search criteria, use the short-host name format with an asterisk wild card (For example, myhost*).
You can list the events that are logged when you run a command, whether accepted or rejected by the policy server.
Keystroke logs are related to events. When you run a command, , such as pmrun whoami, the policy server either accepts or rejects the command based on the policy. When the policy server accepts the command, it creates an event and a corresponding keystroke log. If it rejects the event, it does not create a keystroke log. In order to view a keystroke log, you must first list events to find a particular keystroke log.
The pmlog command displays event log entries, such as events by date and time, host, user, run user, command, and result.
To display a list of events from the command line on the policy server
-
From the command line, enter:
# pmlog --after "2011/05/06 00:00:00" --user "tuser"
pmlog provides direct and flexible access to the event logs on the local policy server and is capable of complex queries.
If you run a command, you might see output similar to the following which indicates the policy server has successfully accepted or rejected commands:
Accept 2011/05/11 13:20:04 tuser@ myhost.example.com -> root@ myhost.example.com
whoami
Command finished with exit status 0
Accept 2011/05/11 14:05:58 tuser@ myhost.example.com -> root@ myhost.example.com
whoami
Command finished with exit status 0
Reject 2011/05/11 14:06:17 tuser@ myhost.example.com
Fakecmd
The following pmlog options support the use of wildcards, such as * and ?:
-
--user
-
--runuser
-
--reqhost
-
--runhost
-
--masterhost
You can also use the pmremlog command on the primary policy server to run pmlog on secondary policy servers. For example:
# pmremlog -h polsrv2 -p pmlog -- --user myuser --command sh
Related Topics
pmlog
pmremlog

