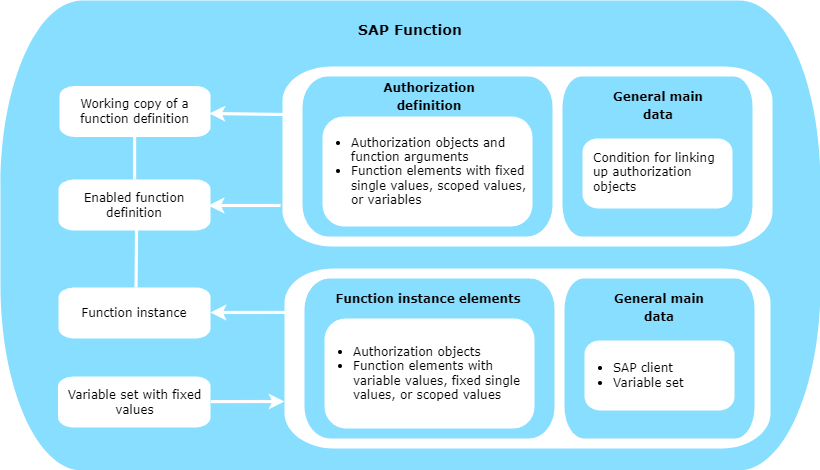
The SAP function structure
Create function definitions, function instances, and variable sets for SAP functions. You can use an SAP function for different instances. To do this, use variables in the function definition. Fixed variable values are grouped in variable sets and used in the function instances.
A function definition contains the authorization definition as well as general main data. An authorization definition contains at least one authorization object. Each authorization object consists of at least one function element (activity or authorization field) with fixed values. These are given as single values or as upper and lower limits. Function elements can be listed more than once per authorization object.
Figure 3: SAP function elements
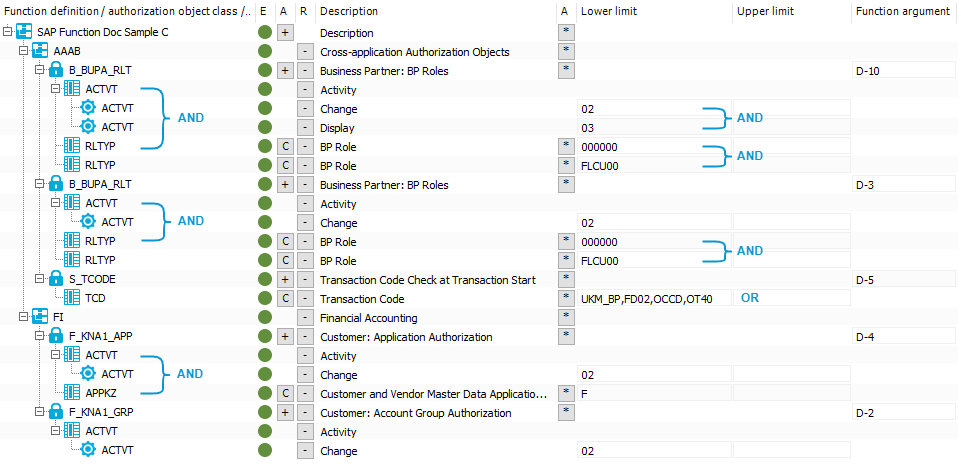
Combining authorization objects and function elements
All authorization objects, function elements, and values from the authorization definition are logically combined together for the authorization check. The following rules apply:
-
All different function elements that belong to an authorization object are AND-ed together (AND).
-
Different values of one and the same function element can be AND-ed as well as OR-ed together (OR).
-
Function arguments can be either AND-ed or OR-ed together.
The following rules apply to function arguments:
-
Each function argument is permitted for use in an authorization definition for just one authorization object.
-
Each authorization object is assigned to exactly one function argument with its function elements and values.
-
An authorization object can be used multiple times with different values within an authorization definition. An new function argument is created for each instance.
Figure 4: Combining function elements and values together
The SAP function stores the combined function arguments in a condition. You can also use brackets in this condition to group function arguments.
Figure 5: Condition with combined function arguments
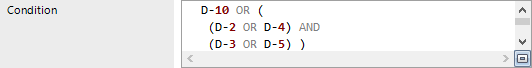
For example, the function definition in these figures determines SAP roles with the following authorizations:
Ignoring SAP applications
The TargetSystem | SAPR3 | SAPRights | TestWithoutTCD configuration parameter is evaluated by authorization checks. The configuration parameter specifies whether the authorization check ignores the authorization objects required to identify SAP applications.
IMPORTANT: The TargetSystem | SAPR3 | SAPRights | TestWithoutTCD configuration parameter will be deleted in a future version of One Identity Manager and cannot be set anymore in version 9.3.
When updating the One Identity Manager database from a version older than 9.3 to version 9.3, the configuration parameter setting is transferred without alteration. This functionality stays the same. However, the configuration parameter can neither be set nor cleared in the current One Identity Manager version.
To change the processing logic of the authorization definition, change the logical expression that is entered as a condition in each function definition.
Conditions in existing function definitions from versions older than 9.3 are calculated when the One Identity Manager database is updated. This takes the configuration parameter setting into account.
The configuration parameter is not set (default)
Behavior in version 9.3:
Behavior when transferring function definitions from versions older than 9.3:
-
Create a function argument for each authorization object in a function definition. The properties of the authorization objects determine the names of the function arguments.
You can rename the function arguments as required in the Manager.
-
There is a generated condition. In the condition, group all the function arguments that belong to an SAP application inside a pair of brackets and AND them with each other. All brackets are OR-ed together.
The configuration parameter is set
Behavior in version 9.3:
Behavior transferring function definitions from versions older than 9.3:
-
Create a function argument for each authorization object in a function definition. The properties of the authorization objects determine the names of the function arguments.
You can rename the function arguments as required in the Manager.
-
There is a generated condition. All function arguments AND-ed in the condition.
Examples of SAP functions
If you create an authorization definition, you need to think about which authorization combinations are not compliant. You can differentiate between two use cases:
-
Are there SAP roles or user accounts with invalid authorization combinations?
Create an SAP function for authorizations that cannot occur together with an SAP role or an SAP user account. The authorization check identifies all SAP roles and user accounts where the sum total of their authorizations have this invalid combination of authorizations.
-
Are there identities that own invalid authorization combinations through their SAP user accounts?
-
Create a compliance rule that checks whether there are identities with SAP user accounts that match the SAP functions.
-
Create different SAP functions for authorizations that in combination are invalid. Create compliance rules that combine these SAP functions. The compliance check finds all identities that have such invalid authorization combinations over the sum of all authorizations of their SAP user accounts.



