Introduction
To provide end-users located on another network with access to your applications, you can configure Cloud Access Manager to federate with an Identity Provider (IDP) running on the end-user network. The IDP authenticates users against its local directory and sends an assertion to Cloud Access Manager (the Service Provider) to vouch for the user’s authenticity.
Topics:
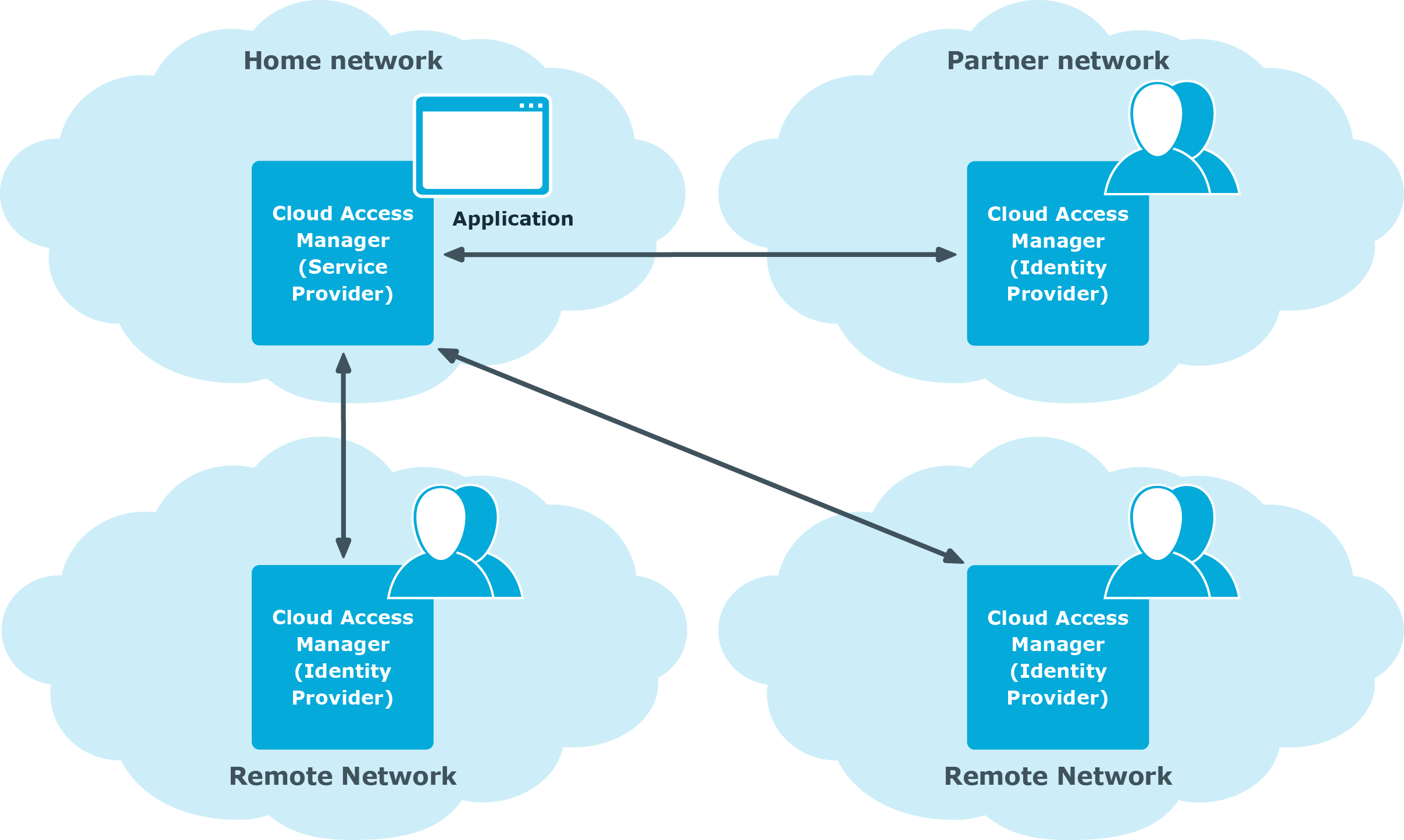
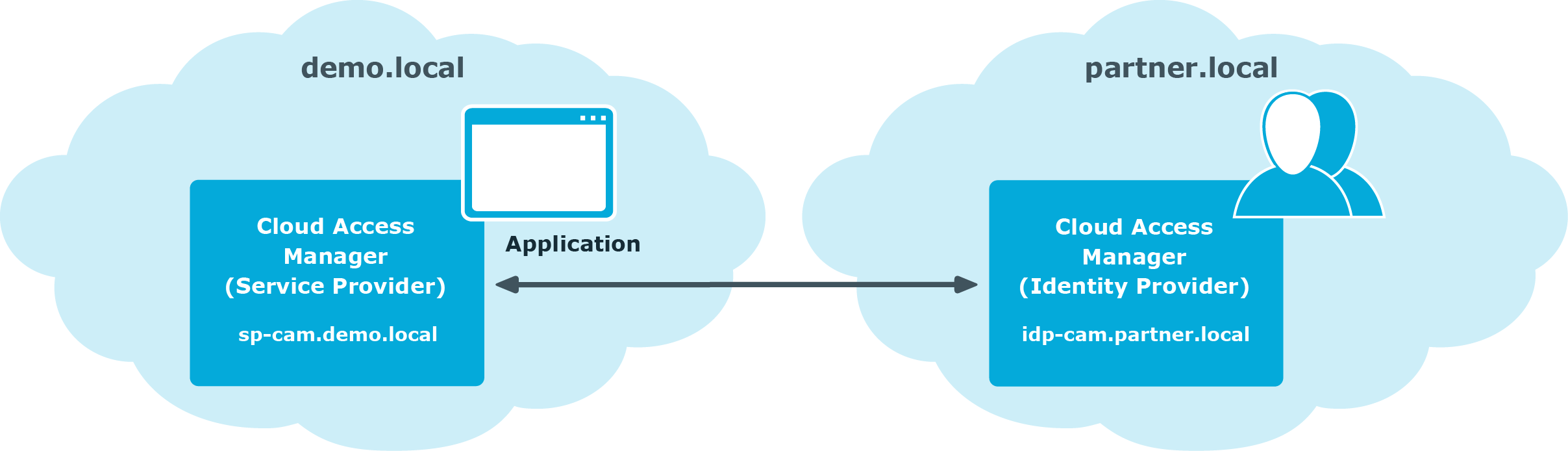
The identity provider must support the SAML or WS-Federation protocol. It can be an on-premise service or a Software-as-a-Service (SaaS) service provided by a third-party vendor, or you can deploy another instance of Cloud Access Manager to perform the role of identity provider, as shown in Figure 1.
Figure 1: Multi-federated Cloud Access Manager deployment
This guide describes how to configure one instance of Cloud Access Manager to operate as an Identity Provider which will federate to another instance of Cloud Access Manager configured to operate as a Service Provider.
Prerequisites
Before starting the configuration, please make sure the following prerequisites are met:
- Two member servers, sp-cam.demo.local and idp-cam.partner.local, are each located in their own Active Directory forest
- A Cloud Access Manager Proof-of-Concept installation exists on each server
- A front-end authenticator is configured on idp-cam.partner.local to connect to the local Active Directory
Configuration
-
Configuring the SAML application on idp-cam.partner.local
describes how to configure the Identity Provider (IDP) Cloud Access Manager instance (on idp-cam.partner.local) with a SAML application to define the service provider (SP) Cloud Access Manager instance (on sp-cam.demo.local).
-
Setting up the front-end authenticator in sp-cam.demo.local
describes how to configure the SP Cloud Access Manager instance (on sp-cam.demo.local) with a front-end authenticator (FEA) definition for the IDP Cloud Access Manager instance (on idp-cam.partner.local).
-
describes how to test a federated logon to the SP Cloud Access Manager instance authenticating against the IDP Cloud Access Manager instance.
Figure 2: Lab deployment with Cloud Access Manager to Cloud Access Manager federation
Configuring the SAML application on idp-cam.partner.local
This section describes how to configure the Identity Provider (IDP) Cloud Access Manager instance on idp-cam.partner.local with a SAML application to define the service provider (SP) Cloud Access Manager instance on sp-cam.demo.local
There are two methods you can use to create the SAML application:
- Using the template provided
- Configuring the application manually
In addition you can:
- Configure the Cloud Access Manager roles to be returned
To configure the SAML application using the template
- Log in as a fallback administrator to the Cloud Access Manager instance on idp-cam.partner.local.
- From the main menu in the Applications section click + Add New.
- In the Create an Application Using a Template section select the One Identity Cloud Access Manager template.
- On the Settings forCloud Access Manager enter sp-cam.demo.local as the Cloud Access Manager hostname and then click Save & Next.
- On the Subject Mapping page click Derive the username from an attribute.
- In the Take the username from the following attribute field enter sAMAccountName.
- Click Next.
- The Permissions page is displayed. Here you can grant or deny access to the application based on role membership. Select Allow Role Access to specify which roles will have access to Cloud Access Manager.
- Enter a name for this application configuration.
- Click Next.
- The Application Portal configuration screen allows you to determine how the app link to the Cloud Access Manager SP instance is presented on the local Application Portal. For this example, users will navigate directly to the Cloud Access Manager SP Application Portal. This means that the URL to the local Cloud Access Manager IDP Application Portal will not be published, and therefore the settings here are not important. Leave all settings as they are and click Finish.
- The Federation Settings page provides you with information that you may need to configure your Service Provider. In this example, we will generate metadata to set up our Service Provider. Click Download Metadata and transfer the downloaded file to your sp-cam.demo.local machine.
Configuring the SAML application manually
- Log in as a fallback administrator to the Cloud Access Manager instance on idp-cam.partner.local.
- From the main menu, in the Applications section, click + Add New.
- The Create New Application page is displayed. Click Configure Manually.
- The Back-end SSO Method page is displayed. Select SAML and then click Next.
-
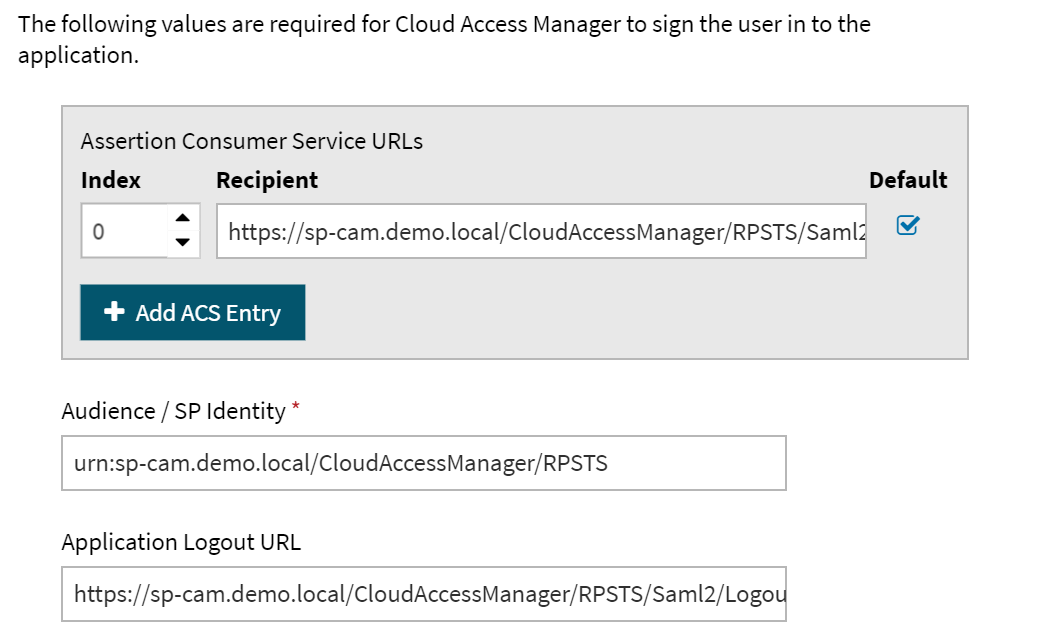
On the Federation Settings screen, enter the Recipient and the Audience / SP Identity as follows:
Recipient:
https://sp-cam.demo.local/CloudAccessManager/RPSTS/Saml2/Default.aspx
Audience/SP Identity:
urn:sp-cam.demo.local/CloudAccessManager/RPSTS
Application Logout URL:
https://sp-cam.demo.local/CloudAccessManager/RPSTS/Saml2/Logout.aspx
- On the Subject Mapping page, click Derive the username from an attribute.
- In the Take the username from the following attribute field, enter sAMAccountName.
- Click Next.
- Click Next to advance to the External Access page. This asks you whether the application should be proxied for situations where external users are required to access applications on your internal network. When Cloud Access Manager is operating as an IDP, the application (SP) does not run on your internal network and therefore this is not required. Select Do not proxy this application.
- Click Next.
- The Permissions page is displayed. Here you can grant or deny access to the application based on role membership. Select Allow Role Access to specify which roles will have access toCloud Access Manager.
-
Now enter a name for this application configuration.
- Click Next.
-
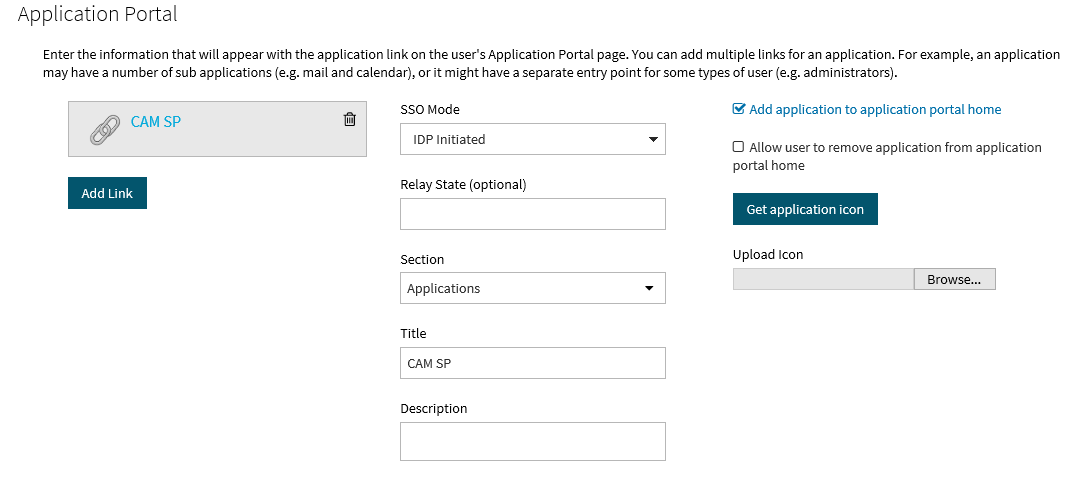
The Application Portal configuration screen allows you to determine how the app link to the Cloud Access Manager SP instance is presented on the local Application Portal. Since in this example users will navigate directly to the Cloud Access Manager SP Application Portal, the URL to the local Cloud Access Manager IDP Application Portal will not be published, so the settings here are not important. Select IDP-Initiated under SSO Mode and click Finish.
- The Federation Settings page provides you with information you may need to configure your Service Provider. In this example, we will generate metadata to set up our Service Provider. Click Download Metadata and transfer the downloaded file to your sp-cam.demo.local machine.
Configuring Cloud Access Manager roles to be returned
To configure the IDP instance to return the Cloud Access Manager roles that users belong to, use the following steps. You can then employ these roles in the SP instance to control user access to applications.
- Log in as a fallback administrator to the Cloud Access Manager instance on idp-cam.partner.local
- From the main menu, in the Applications section, click View and Edit.
- Select the One Identity Cloud Access Manager application that you created in the previous sections.
- Select the Claim Mapping section.
- Select the Send Cloud Access Manager role claim checkbox.
- Click Finish.