Lightweight indexing
One Identity Safeguard for Privileged Sessions is capable of analyzing the contents of the sessions it monitors to provide help analytics and speed up forensics investigations. This process is called indexing.
You can now select the depth of indexing: lightweight and full indexing.
Lightweight indexing is now enabled by default in case of a newly installed SPS or when you add new connection policies. If indexing was enabled for a connection policy it is converted to full indexing automatically during the upgrade.
Lightweight indexing is significantly faster than full indexing, but it extracts only the executed commands and the window titles that appear on the screen. It does not index any other screen content (for example, text that is displayed in a terminal or that appears in an RDP window).
For more information, see "Configuring the internal indexer" in the Administration Guide.
Performance improvements in indexing graphical sessions
To make the text displayed in graphical sessions (for example, RDP) SPS uses optical character recognition. The way this is done has been greatly optimized. Depending on the exact scenario and the contents of the session, this can significantly decrease the time required to index the audit trails.
Safeguard Desktop Player replays audit trails of X11 sessions
The Safeguard Desktop Player application can now replay audit trails that contain graphical X11 sessions (the contents of the X11 Forward channel of the SSH protocol).
For further details, see "Replay X11 sessions" in the Safeguard Desktop Player User Guide.
Audit trail encryption improvements
|

|
Caution:
One Identity Safeguard for Privileged Sessions (SPS) 5 F4 and later versions use a new encryption algorithm to encrypt the recorded audit trails (AES128-GCM). This change has the following effects:
-
If you are using external indexers to index your audit trails, you must upgrade them to the latest version. Earlier versions will not be able to index encrypted audit trails recorded with SPS 5 F4 and later.
-
To replay an encrypted audit trail recorded with SPS 5 F4 or later, you can use the latest version of the Safeguard Desktop Player application, or the browser-based player of SPS. You cannot replay such audit trails using earlier versions of Safeguard Desktop Player, nor any version of the Audit Player application. |
You can now manually re-encrypt your audit trails with a new encryption key. This is useful if you want to share encrypted audit trails with third parties — the data remains encrypted, but you do not have to share your encryption keys. For details, see "Sharing an encrypted audit trail" in the Safeguard Desktop Player User Guide.
Security settings of TLS sessions
You can now uniformly set the TLS security settings of HTTP, RDP, Telnet, and VNC connections, including the permitted ciphers and TLS versions on the <Protocol> Control > Settings pages.
To ensure the security of your sessions, SSL encryption is not supported anymore, only TLS 1.0 and later.
Using GSSAPI in SSH connections
You can now use an Authentication Policy with GSSAPI and a Usermapping Policy in SSH connections. When an SSH Connection Policy uses an Authentication Policy with GSSAPI, and a Usermapping Policy, then SPS stores the user principal as the Gateway username, and the username used on the target as the Server username.
Note that this change has the following side effect: when using an Authentication Policy with GSSAPI, earlier versions of SPS used the client-username@REALM username to authenticate on the target server. Starting with version 5.9.0, it uses the client-username as username. Configure your servers accordingly, or configure a Usermapping Policy for your SSH connections in SPS.
Authenticate HTTP/HTTPS connections on the SPS gateway
SPS now provides a way to authenticate non-transparent HTTP/HTTPS connections on SPS to local and external backends (LDAP, Microsoft Active Directory, RADIUS). The client must support proxy authentication.
For more information, see "Creating a new HTTP authentication policy" in the Administration Guide.
Credential store support for TN3270 protocol
SPS can now be configured to check out passwords from the built-in or external credential stores, such as One Identity Safeguard for Privileged Passwords, and play them in during a connection using the TN3270 protocol.
RDP improvements
You can now display a banner to your clients in RDP sessions. For example, this banner can inform the users that the connection is audited. For details, see "Creating and editing protocol-level RDP settings" in the Administration Guide.
Figure 7: Graphical banner in RDP
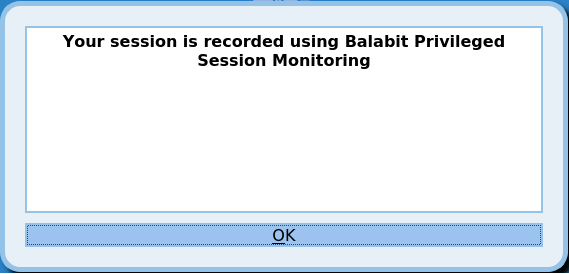
The Authentication and Authorization plugins now can request information interactively from the user in a graphical window, for example, a ticket ID, or a one-type password. To request a plugin that interoperates with your authentication or authorization system, contact our Support Team.
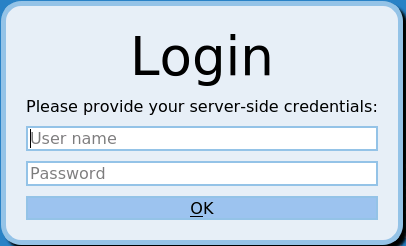
If the server requires Network Level Authentication and the Allow me to save credentials option is not selected in the RDP client, SPS now automatically displays a graphical prompt where the users can enter their usernames and passwords.
Figure 8: Server-side login in RDP
Interactive RDP improvements
When using inband destination selection, your users now do not have to encode any data in the username: SPS can display an interactive prompt in the RDP connection to request the address of the destination server, username, and other required information. For details, see "Inband destination selection in RDP connections" in the Administration Guide.
As a smaller improvement, SPS now supports using certificate chains in the signing CA used for RDP connections.
TLS-encryption for RDP connections
Enabling TLS-encryption in an RDP connection policy has been simplified. When the connection is encrypted, SPS has to show a certificate to the peer. You can define the type of certificate to show to the peers.
In case of compatibility issues, you also have the option to allow fallback to legacy RDP Security Layer (also known as: Standard RDP Security). However, it is not advised due to security reasons.
For more information, see "Enabling TLS-encryption for RDP connections" in the Administration Guide.
Windows 2019 Server support
SPS now supports Windows 2019 Server as a client and server in RDP sessions.
Certificate Revocation Lists (CRLs) in signing CAs
It is now possible to configure the CRL that you generated using your Certificate Authority (CA) in your Public Key Infrastructure (PKI) solution. This is the CRL information that will be shown to clients connecting to SPS. For more information, see "Signing certificates on-the-fly" in the Administration Guide.



