syslog-ng Store Box (SSB) prevents brute force attacks when logging in. If you repeatedly try logging in to SSB using incorrect login details within a short period of time (10 times within 60 seconds), the source IP gets blocked on UI destination port 443 for 5 minutes. Your browser displays an Unable to connect page.
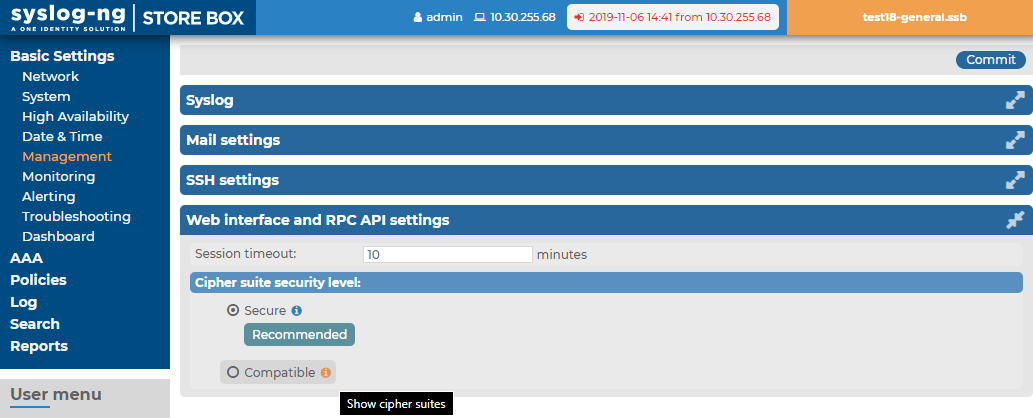
By default, SSB terminates the web session of a user after ten minutes of inactivity. To change this timeout value, adjust the Basic Settings > Management > Web interface and RPC API settings > Session timeout option.
In addition to controlling the web session timeout value, you can also specify the cipher suites to be permitted in the HTTPS connection.
The Basic Settings > Management > Web interface and RPC API settings > Cipher suite option allows you to choose the strength of the allowed cipher suites using one of the following options:
-
Compatible: It is a large set of cipher suites determined by the following cipher string:
ALL:!aNULL:!eNULL
The Compatible setting may allow permitting (and hence not safe) cipher suites for the Transport Layer Security (TLS) negotiations.
-
Secure: A smaller and more strict set of cipher suites where vulnerable cryptographic algorithms are eliminated. This cipher suite set is determined by the following cipher string:
HIGH:!COMPLEMENTOFDEFAULT:!aNULL:!eNULL:!DHE-RSA-AES128-SHA:!DHE-RSA-AES256-SHA:!ECDHE-RSA-AES128-SHA:!ECDHE-RSA-AES256-SHA:!AES128-SHA:!AES256-SHA
Figure 36: Basic Settings > Management > Web interface and RPC API settings — Set session timeout and Cipher suite