This section describes how patterns work. This information applies to program patterns and message patterns alike, even though message patterns are used to illustrate the procedure.
Figure 218: Applying patterns
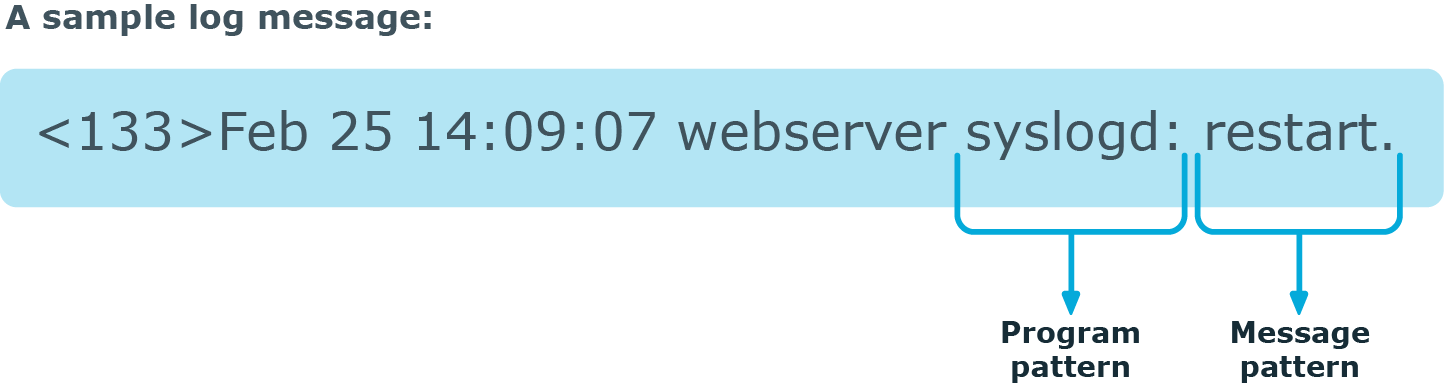
Patterns can consist of literals (keywords, or rather, keycharacters) and pattern parsers. Pattern parsers attempt to parse a sequence of characters according to certain rules.
NOTE: Wildcards and regular expressions cannot be used in patterns. The @ character must be escaped, that is, to match for this character, you have to write @@ in your pattern. This is required because pattern parsers of syslog-ng are enclosed between @ characters.
When a new message arrives, syslog-ng attempts to classify it using the pattern database. The available patterns are organized alphabetically into a tree, and syslog-ng inspects the message character-by-character, starting from the beginning. This approach ensures that only a small subset of the rules must be evaluated at any given step, resulting in high processing speed. Note that the speed of classifying messages is practically independent from the total number of rules.
For example, if the message begins with the Apple string, only patterns beginning with the character A are considered. In the next step, syslog-ng selects the patterns that start with Ap, and so on, until there is no more specific pattern left.
Note that literal matches take precedence over pattern parser matches: if at a step there is a pattern that matches the next character with a literal, and another pattern that would match it with a parser, the pattern with the literal match is selected. Using the previous example, if at the third step there is the literal pattern Apport and a pattern parser Ap@STRING@, the Apport pattern is matched. If the literal does not match the incoming string (foe example, Apple), syslog-ng attempts to match the pattern with the parser. However, if there are two or more parsers on the same level, only the first one will be applied, even if it does not perfectly match the message.
If there are two parsers at the same level (for example, Ap@STRING@ and Ap@QSTRING@), it is random which pattern is applied (technically, the one that is loaded first). However, if the selected parser cannot parse at least one character of the message, the other parser is used. But having two different parsers at the same level is extremely rare, so the impact of this limitation is much less than it appears.
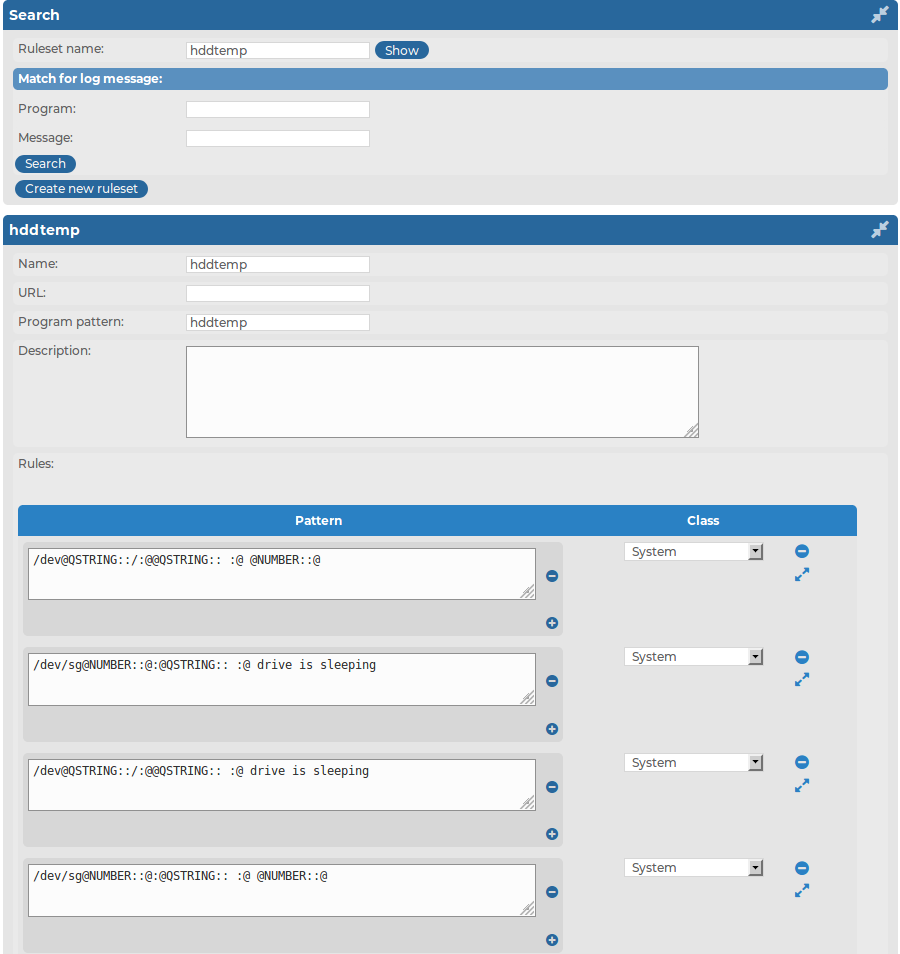
To display the rules of a ruleset, enter the name of the ruleset into the Search > Ruleset name field, and click Show. If you do not know the name of the ruleset, type the beginning letter(s) of the name, and the names of the matching rulesets will be displayed. If you are looking for a specific rule, enter a search term into the Program or Message field and select Search. The rulesets that contain matching rules will be displayed.
NOTE: Rulesets containing large number of rules may not display correctly.
Figure 219: Log > Pattern Database > Search > Ruleset name — Searching rules
The following describes how to create a new ruleset and new rules.
To create a new ruleset and new rules
-
Select Log > Pattern Database > Create new ruleset.
TIP: If you search for a ruleset that does not exist, syslog-ng Store Box(SSB) offers you to create a new ruleset with the name you were searching for.
-
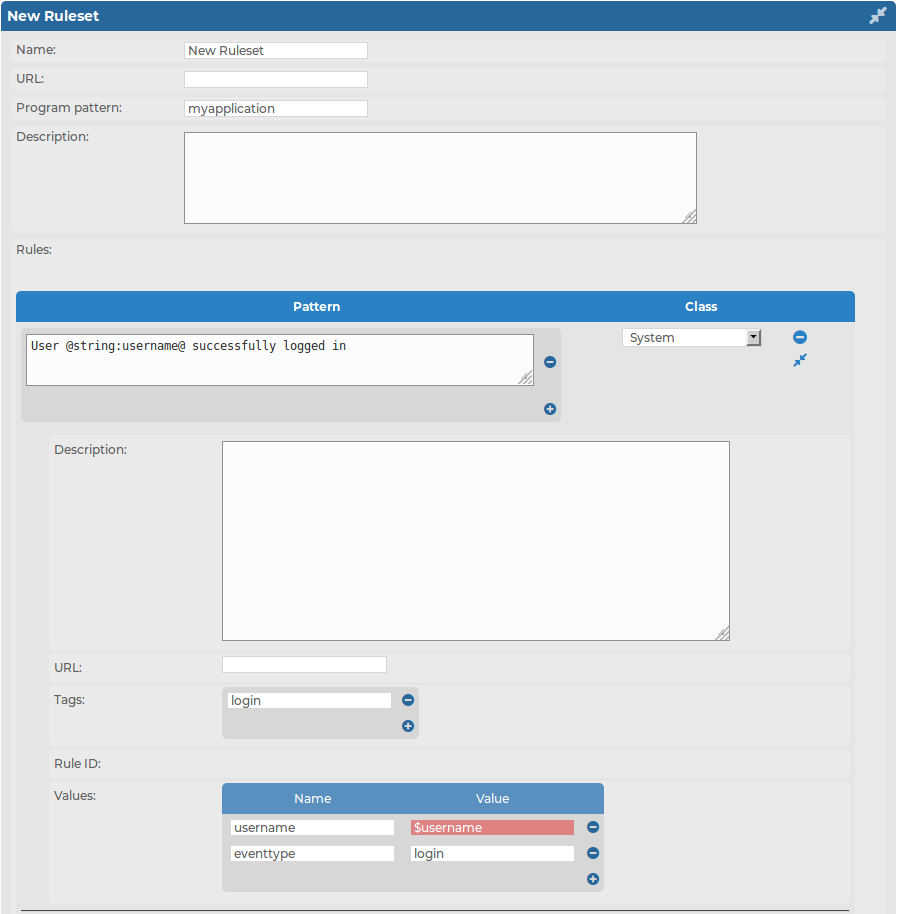
Enter a name for the ruleset into the Name field.
Figure 220: Log > Pattern Database > Create new ruleset — Creating pattern database rulesets
-
Enter the name of the application or a pattern that matches the applications into the Program pattern field. For details, see Using pattern parsers.
-
Optionally, add a description to the ruleset.
-
Add rules to the class.
-
Click  in the Rules section.
in the Rules section.
-
Enter the beginning of the log message or a pattern that matches the log message into the Pattern field. For details, see Using pattern parsers. Note that only messages sent by applications matching the Program pattern will be affected by this pattern.
-
Select the type of the message from the Class field. This class will be assigned to messages matching the pattern of this rule. The following classes are available: Violation, Security, and System.
If alerting is enabled at Log > Options > Alerting, SSB automatically sends an alert if a message is classified as Violation.
-
Optionally, you can add a description, custom tags, and name-value pairs to the rule. Note that the values of name-value pairs can contain macros in the ${macroname} format. For details on pattern databases and macros, see The syslog-ng Premium Edition Administration Guide.
-
Repeat the previous step to add more rules.
-
Click  .
.
To export the entire pattern database, navigate to Log > Pattern Database and select Export.
To export a ruleset, enter the name of the ruleset into the Search > Ruleset name field, click Show, and select Export ruleset. If you do not know the name of the ruleset, enter a search term into the Program or Message field and select Search. The rulesets that contain matching rules will be displayed.




 in the Rules section.
in the Rules section. .
.