Privilege Manager for Unix licensing
Privilege Manager for Unix 7.0 licensing options include:
30-day evaluation licenses
Privilege Manager for Unix evaluation license allows you to manage unlimited PM Agent hosts for 30 days.
Commercial licenses
A PM Policy license is required for Privilege Manager for Unix features.
Although licenses are allocated on a per-agent basis, you install the licenses on Privilege Manager for Unix policy servers.
The pmlicense command allows you to display current license information, update a license (an expired one or a temporary one before it expires) or create a new one. See Installing licenses or Displaying license usage for more examples of using the pmlicense command.
Deployment scenarios
You can deploy Privilege Manager for Unix software within any organization using UNIX and/or Linux systems. Privilege Manager for Unix offers a scalable solution to meet the needs of the small business through to the extensive demands of the large or global organization.
There is no right or wrong way to deploy Privilege Manager for Unix, and an understanding of the flexibility and scope of the product will aid you in determining the most appropriate solution for your particular requirements. This section describes the following sample implementations:
- a single host installation
- a medium-sized business installation
- a large business installation
- an enterprise installation
Configuration options
Decide which of the following configurations you want to set up:
-
Primary Server Configuration: Configure a single host as the primary policy server hosting the security policy for the policy group using either the pmpolicy (Privilege Manager for Unix) or sudo (Safeguard for Sudo) policy type. See Security policy types for more information about these policy types.
If you are configuring the primary policy server using the sudo policy type, see the One Identity Privilege Manager for Sudo Administration Guide.
- Secondary Server Configuration: Configure a secondary policy server in the policy server group to obtain a copy of the security policy from the primary policy server.
-
PM Agent Configuration: Join a Privilege Manager for Unix Agent host to a pmpolicy server group.
Policy servers can only be joined to policy groups they host (that is, manage). You cannot join a Sudo Plugin host to a pmpolicy server group or the PM Agent host to a sudo policy server group.
Single host deployment
A single-host installation is typically appropriate for evaluations, proof of concept, and demonstrations of Privilege Manager for Unix. This configuration example installs all of the components on a single UNIX/Linux host, with protection offered only within this single host. All logging and auditing takes place on this host.
Medium business deployment
The medium business model is suitable for small organizations with relatively few hosts to protect, all of which may be located within a single data center.
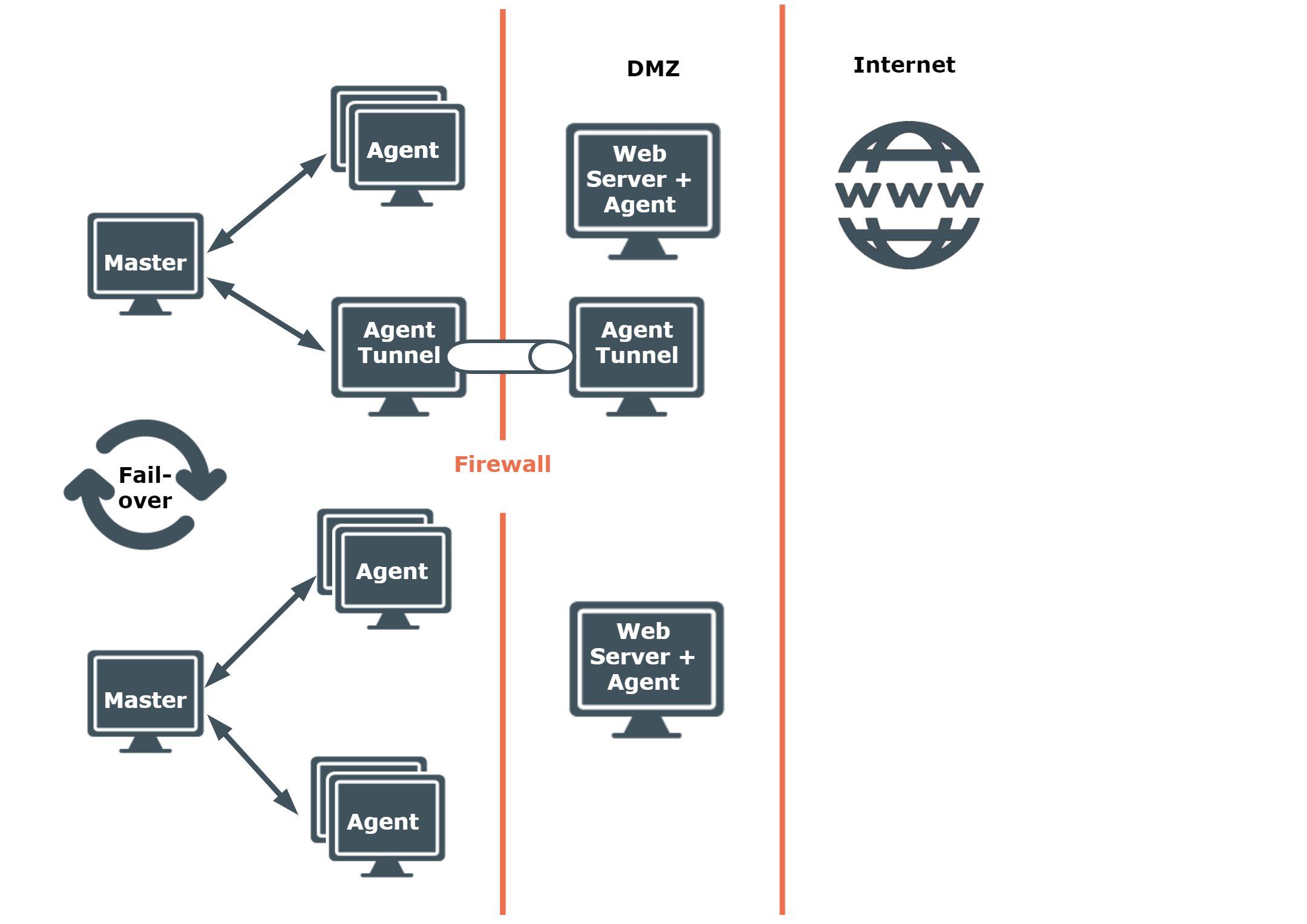
This configuration example comprises multiple UNIX/Linux hosts located within the SME space and one or more web servers located in a DMZ.
The tunneling feature (pmtunneld), enables Privilege Manager for Unix to control privileged commands on the web servers across a firewall, within the DMZ. This configuration significantly reduces the number of open ports at the firewall.
Multiple policy server components (pmmasterd) are installed in a failover configuration, with groups of agents balanced between the policy servers. If a policy server is unavailable for any reason, the agents will failover to the alternative policy server.
Figure 4: Medium business implementation: Minimum 2 Masters and Circa 100 Agents